Question 521
What does the number in an NTP stratum level represent?
A. The number of hops it takes to reach the authoritative time source
B. The amount of offset between the device clock and true time
C. The number of hops it takes to reach the primary time server
D. The amount of drift between the device clock and true time
Question 522
Refer to the exhibit. Clients report that they cannot connect to this SSID using the provided PSK
Which action will resolve this issue?
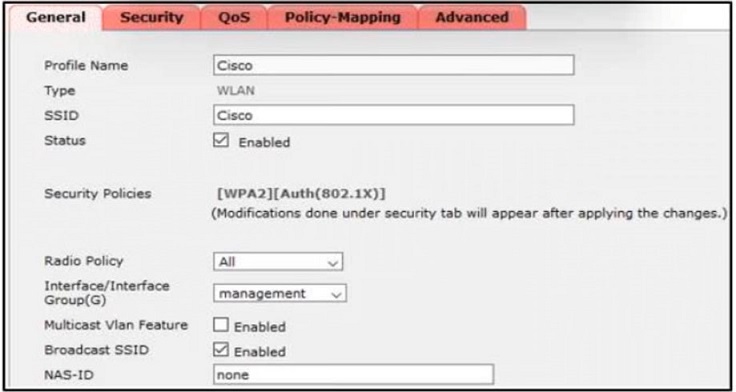
A. Apply the correct interface to this WLAN
B. Apply the changes this SSID
C. Select the PSK under authentication key management
D. Define the correct Radio Policy.
Question 523
Which QoS queuing method transmits packets out of the interface in the order the packets arrive?
A. custom
B. weighted-fair
C. FIFO
D. priority
Question 524
Which two results occur if Cisco DNA Center loses connectivity to devices in the SD-Access fabric? (Choose two.)
A. Users lose connectivity
B. Already connected users are unaffected but new users cannot connect
C. All devices reload after detecting loss of connection to Cisco DNA Center
D. User connectivity is unaffected
E. Cisco DNA Center is unable to collect monitoring data in Assurance
Question 525
Refer to the exhibit. The connection between SW1 and SW2 is not operational
Which two actions resolve the issue? (Choose two.)

A. configure switchport nonegotiate on SW1
B. configure switchport nonegotiate on SW2
C. configure switchport mode access on SW2
D. configure switchport mode trunk on SW2
E. configure switchport mode dynamic desirable on SW2
Question 526
What does a YANG model provide?
A. standardized data structure independent of the transport protocols
B. creation of transport protocols and their interaction with the OS
C. user access to interact directly with the CLI of the device to receive or modify network configurations
D. standardized data structure that can be used only with NETCONF or RESTCONF transport protocols
Question 527
A system must validate access rights to all its resources and must not rely on a cached permission matrix. If the access level to a given resource is revoked but is not reflected in the permission matrix, the security is violated
Which term refers to this REST security design principle?
A. economy of mechanism
B. complete mediation
C. separation of privilege
D. least common mechanism
Question 528
Refer to the exhibit
Which command set completes the ERSPAN session configuration?
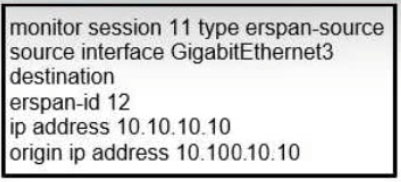
A. monitor session 11 type erspan-destination destination interface GigabitEthemet4 source erspan-id 11 ip address 10.10.10.10
B. monitor session 12 type erspan-destination destination interface GigabitEthernet4 source erspan-id 12 ip address 10.10.10.10
C. monitor session 11 type erspan-destination destination interface GigabitEthernet4 source erspan-id 12 ip address 10.100.10.10
D. monitor session 12 type erspan-destination destination interface GigabitEthernet4 source erspan-id 11 ip address 10.10.10.10
Question 529
"HTTP/1.
1 204 No Content" is returned when the curl -i -X DELETE command is issued
Which situation has occurred?
A. The command succeeded in deleting the object.
B. The object was located at the URI, but it could not be deleted
C. The object could not be located at the URI path.
D. The URI was invalid.
Question 530
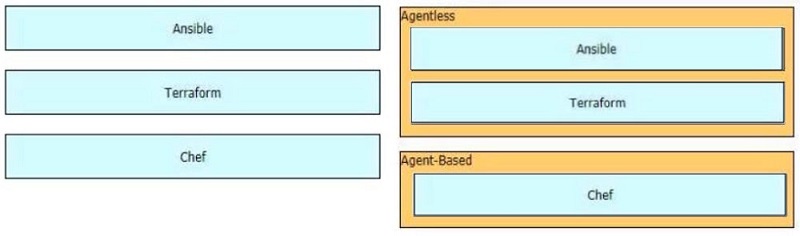
DRAG DROP -Drag and drop the tools from the left onto the agent types on the right.
Select and Place: