Configuring Errdisable Recovery on Cisco Switches
Objective
The objective of this lab exercise is for you to learn and understand how the errdisable recovery feature works on a Layer 2 network. This lab will not work on Packet Tracer.
Purpose
Understanding how errdisable functionality works on a Layer 2 switch is a fundamental skill that will allow a network engineer to recover a port from the error-disable state. As a Cisco engineer, as well as in the Cisco CCNA exam, you will be expected to know how to recover any port in an error-disable state.
Lab Topology
Use the following topology to complete this lab exercise:
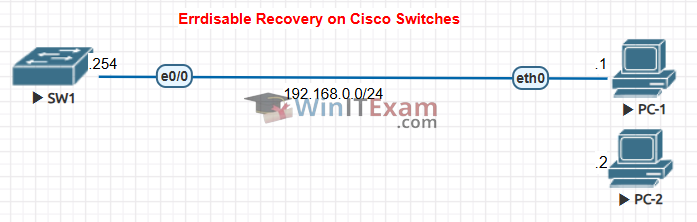
Task 1: Configure Hostname
Objective: Configure the hostname on SW1 as illustrated in the topology.
Configuration:
SW1#conf t Enter configuration commands, one per line. End with CTRL/Z. SW1(config)#hostname SW1
Task 2: Create SVI for VLAN1
Objective: Create an SVI for VLAN1 on the switch and apply the respective IP address as illustrated in the topology (do the same thing with PC1).
Configuration:
SW1#conf t Enter configuration commands, one per line. End with CTRL/Z. SW1(config)#interface vlan 1 SW1(config-if)#ip address 192.168.0.254 255.255.255.0 SW1(config-if)#no shut SW1(config-if)#end SW1#
Task 3: Configure Port Security
Objective: Configure SW1 port 0/1 with the following settings:
- Access-port mode
- Access-port VLAN1
- Switchport port-security enabled
- Switchport port-security maximum MACs of 1
- Switchport port-security violation mode shutdown
Configuration:
SW1#conf t Enter configuration commands, one per line. End with CTRL/Z. SW1(config)#interface gigabit0/1 SW1(config-if)#switchport mode access SW1(config-if)#switchport access vlan 1 SW1(config-if)#switchport port-security SW1(config-if)#switchport port-security maximum 1 SW1(config-if)#switchport port-security violation shutdown SW1(config-if)#end
Task 4: Test Port Security Violation
Objective: Remove PC1 and attach PC2 to the same port with a different IP address (192.168.10.2) and see how the port is shut down.
Configuration:
VPCS> ping 192.168.0.254 84 bytes from 192.168.0.254 icmp_seq=1 ttl=255 time=0.390 ms 84 bytes from 192.168.0.254 icmp_seq=2 ttl=255 time=0.455 ms 84 bytes from 192.168.0.254 icmp_seq=3 ttl=255 time=0.267 ms 84 bytes from 192.168.0.254 icmp_seq=4 ttl=255 time=0.387 ms 84 bytes from 192.168.0.254 icmp_seq=5 ttl=255 time=0.663 ms Switch CLI Message: %PORT_SECURITY-2-PSECURE_VIOLATION: Security violation occurred, caused by MAC address 001d.60b3.0aff on port FastEthernet0/1 Switch#show interface gigabit0/1 gigabitethernet0/1 is down, line protocol is down (err-disabled)
Task 5: Configure Errdisable Recovery
Objective: Configure the switch so that any port being shut down by a security violation will recover automatically after 5 minutes. Check the status of the port where PC2 is connected after 5 minutes to ensure that the port is up and running. Issue a relevant show command.
Configuration:
SW1#conf t Enter configuration commands, one per line. End with CTRL/Z. SW1(config)#errdisable recovery cause psecure-violation SW1(config)#errdisable recovery inte SW1(config)#errdisable recovery interval 300 SW1(config)#end SW1# *Jul 28 07:56:58.645: %SYS-5-CONFIG_I: Configured from console by console Switch CLI Messages: %PM-4-ERR_RECOVER: Attempting to recover from psecure-violation err-disable state on interface gigabit0/1 %LINK-3-UPDOWN: Interface gigabit0/1, changed state to up %LINEPROTO-5-UPDOWN: Line protocol on Interface gigabit0/1, changed state to up channel-misconfig (STP) Disabled dhcp-rate-limit Disabled dtp-flap Disabled gbic-invalid Disabled inline-power Disabled l2ptguard Disabled link-flap Disabled mac-limit Disabled link-monitor-failure Disabled loopback Disabled oam-remote-failure Disabled pagp-flap Disabled port-mode-failure Disabled pppoe-ia-rate-limit Disabled psecure-violation Enabled security-violation Disabled sfp-config-mismatch Disabled storm-control Disabled udld Disabled unicast-flood Disabled vmps Disabled psp Disabled dual-active-recovery Disabled Timer interval: 300 seconds Interfaces that will be enabled at the next timeout:0 Interface Errdisable reason Time left(sec) --------- ------------------ -------------- Gig0/1 security-violation 300