Securing VTP Domains on Cisco Catalyst Switches
Objective
The objective of this lab exercise is for you to learn and understand how to secure VTP domains using Cisco Catalyst Switches. By default, VTP domains are not password-protected.
Purpose
Securing the VTP domain is a fundamental skill. When VTP domains are not configured with a password, rogue switches can be added to the network and disrupt service. As a Cisco engineer, as well as in the Cisco CCNA exam, you will be expected to know how to configure VTP passwords.
Lab Topology
Use the following topology to complete this lab exercise:
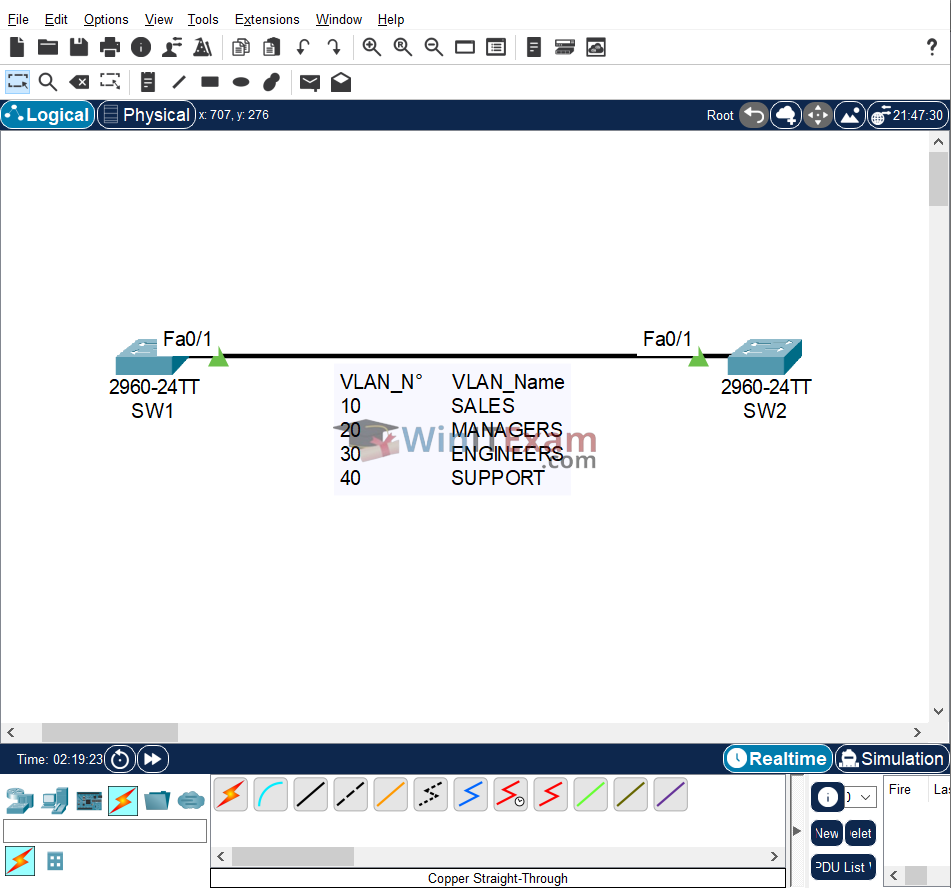
Task 1: Configure Hostname
Objective: In preparation for VLAN configuration, configure a hostname on Sw1 and Sw2 as depicted in the topology.
Configuration Steps:
Switch#config t Enter configuration commands, one per line. End with CTRL/Z. Switch(config)#hostname SW1 SW1(config)# Switch#config t Enter configuration commands, one per line. End with CTRL/Z. Switch(config)#hostname SW2 SW2(config)#
Task 2: Configure VTP Server and Client
Objective: Configure and verify SW1 as a VTP server switch and configure SW2 as a VTP client switch. Both switches should be in the VTP domain named CISCO. Secure VTP messages with the VTP password CISCO.
Configuration Steps:
SW1#config t
Enter configuration commands, one per line. End with CTRL/Z.
SW1(config)#vtp domain CISCO
Changing VTP domain name from Null to CISCO
SW1(config)#vtp password CISCO
Setting device VLAN database password to CISCO
SW1(config)#exit
SW1#show vtp status
VTP Version capable : 1 to 2
VTP version running : 1
VTP Domain Name : CISCO
VTP Pruning Mode : Disabled
VTP Traps Generation : Disabled
Device ID : 00D0.BCC1.7500
Configuration last modified by 0.0.0.0 at 0-0-00 00:00:00
Local updater ID is 0.0.0.0 (no valid interface found)
Feature VLAN :
--------------
VTP Operating Mode : Server
Maximum VLANs supported locally : 255
Number of existing VLANs : 5
Configuration Revision : 0
MD5 digest : 0xBD 0x05 0xF5 0x71 0x93 0xD7 0x12 0x75
0x8D 0x44 0x24 0xD5 0x26 0x62 0x9B 0x18
SW2#config t
Enter configuration commands, one per line. End with CTRL/Z.
SW2(config)#vtp mode client
Setting device to VTP CLIENT mode.
SW2(config)#vtp domain CISCO
Changing VTP domain name from Null to CISCO
SW2(config)#vtp password CISCO
Setting device VLAN database password to CISCO
SW2(config)#exit
SW2#show vtp status
VTP Version capable : 1 to 2
VTP version running : 1
VTP Domain Name : CISCO
VTP Pruning Mode : Disabled
VTP Traps Generation : Disabled
Device ID : 0030.F222.A500
Configuration last modified by 0.0.0.0 at 0-0-00 00:00:00
Feature VLAN :
--------------
VTP Operating Mode : Client
Maximum VLANs supported locally : 255
Number of existing VLANs : 5
Configuration Revision : 0
MD5 digest : 0xBD 0x05 0xF5 0x71 0x93 0xD7 0x12 0x75
0x8D 0x44 0x24 0xD5 0x26 0x62 0x9B 0x18
Task 3: Configure 802.1Q Trunk
Objective: Configure and verify FastEthernet0/1 between SW1 and SW2 as an 802.1Q trunk.
Verification Commands:
SW1#config t Enter configuration commands, one per line. End with CTRL/Z. SW1(config)#interface fastethernet0/1 SW1(config-if)#switchport mode trunk SW2#config t Enter configuration commands, one per line. End with CTRL/Z. SW2(config)#interface fastethernet0/1 SW2(config-if)#switchport mode trunk SW2#copy running-config startup-config
Task 4: Configure and Verify VLANs
Objective: Configure and verify VLANs 10 to 40 on SW1 with the names provided. Validate that these VLANs are still propagated to SW2 after VTP has been secured.
Verification Commands:
SW1#config t
Enter configuration commands, one per line. End with CTRL/Z.
SW1(config)#vlan 10
SW1(config-vlan)#name SALES
SW1(config-vlan)#exit
SW1(config)#vlan 20
SW1(config-vlan)#name MANAGERS
SW1(config-vlan)#exit
SW1(config)#vlan 30
SW1(config-vlan)#name ENGINEERS
SW1(config-vlan)#exit
SW1(config)#vlan 40
SW1(config-vlan)#name SUPPORT
SW1(config-vlan)#end
SW1#copy running-config startup-config
SW1#show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/1, Fa0/2, Fa0/3, Fa0/4
Fa0/5, Fa0/6, Fa0/7, Fa0/8
Fa0/9, Fa0/10, Fa0/11, Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig0/1, Gig0/2
10 SALES active
20 MANAGERS active
30 ENGINEERS active
40 SUPPORT active
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
SW2#show vlan brief
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------------
1 default active Fa0/2, Fa0/3, Fa0/4, Fa0/5
Fa0/6, Fa0/7, Fa0/8, Fa0/9
Fa0/10, Fa0/11, Fa0/12, Fa0/13
Fa0/14, Fa0/15, Fa0/16, Fa0/17
Fa0/18, Fa0/19, Fa0/20, Fa0/21
Fa0/22, Fa0/23, Fa0/24, Gig0/1
Gig0/2
10 SALES active
20 MANAGERS active
30 ENGINEERS active
40 SUPPORT active
1002 fddi-default active
1003 token-ring-default active
1004 fddinet-default active
1005 trnet-default active
Note: Ensure that the MD5 digest at the end of the output of the show vtp status command is the same when VTP passwords have been configured on switches within the same VTP domain.
Cisco Packet Tracer file:
Load and open the .pkt Lab file in Cisco Packet Tracer from here: Securing_VTP_Domains.pkt