Cisco IOS Operating System
Lab Overview
This lab explores basic navigation of the Cisco IOS operating system CLI (Command Line Interface). Only a single device is required. This is a guided walkthrough of the IOS command line interface.
Step-by-Step Instructions
1- Initial Setup
- Open Cisco Packet Tracer.
- Drag and drop the Router 2911 as shown in the below screenshot:

2- Accessing the CLI
- Click on Router0 and then the CLI tab to access the console.
- If prompted to enter the initial configuration dialog after the device has booted up, enter ‘no’.
- Press Enter to get started, then use the command “enable” to enter Privileged Exec mode.
For rebooting the device, use the command “reload”.
3- Understanding Modes
- User Exec Mode: The symbol “>” in “Router>enable” means that we are in user Exec mode.
- Privileged Exec Mode: The symbol “#” in “Router#” means that we are in privileged Exec mode.
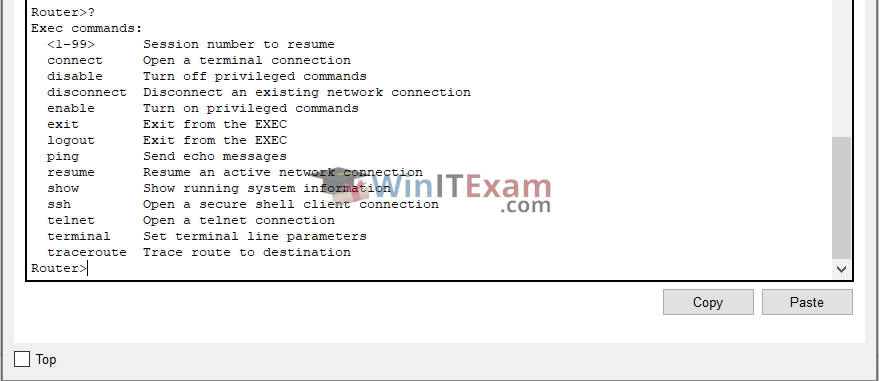
4- User Exec Mode and CLI Command Help

5- Privileged Exec (Enable) Mode and Context Sensitive Help
Router>enable
Router#
Router#disable
Router>
Router>en
Router#
6- Command Abbreviation and Context Sensitive Help
Router#di
% Ambiguous command: "di"
Router#di?
dir disable disconnect
Router#sh?
show
7- Using Tab Completion and Error Handling
Router#sh aaa us
Router#sh aaa user
Router#sh aaa user all
Router#
Router#sh aaa usor all
^
% Invalid input detected at '^' marker.
Router#sh aaa
% Incomplete command.
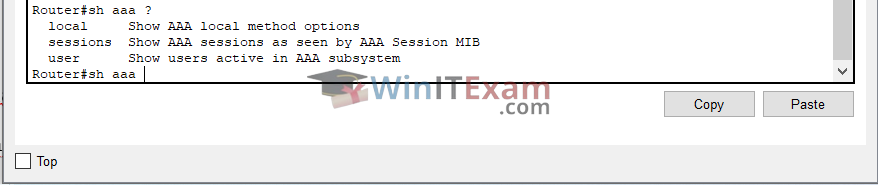
Router#sh aaa ?
local Show AAA local method options
sessions Show AAA sessions as seen by AAA Session MIB
user Show users active in AAA subsystem
8- Global Configuration Mode
Router#configure terminal
Enter configuration commands, one per line. End with CNTL/Z.
Router(config)#
Router(config)#ip host Server1 1.1.1.1
Router(config)#ip host Server2 2.2.2.2
Router(config)#hostname R1
R1(config)#
R1(config)#show ip interface brief
^
% Invalid input detected at '^' marker.
R1(config)#do show ip interface brief
Interface IP-Address OK? Method Status Protocol
GigabitEthernet0/0 unassigned YES unset administratively down down
GigabitEthernet0/1 unassigned YES unset administratively down down
GigabitEthernet0/2 unassigned YES unset administratively down down
Vlan1 unassigned YES unset administratively down down
9- Interface Configuration Mode
R1(config)#interface gigabitEthernet 0/0
R1(config-if)#
R1(config-if)#exit
R1(config)#
R1(config-if)#end
R1#
R1#show running-config
Building configuration...
Current configuration : 687 bytes
!
version 15.1
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R1
!
!
!
!
!
!
!
!
no ip cef
no ipv6 cef
!
!
!
!
license udi pid CISCO2911/K9 sn FTX152457FX
!
!
!
!
!
!
!
!
!
!
!
spanning-tree mode pvst
!
!
!
!
!
interface GigabitEthernet0/0
no ip address
duplex auto
speed auto
shutdown
!
interface GigabitEthernet0/1
no ip address
duplex auto
speed auto
shutdown
!
interface GigabitEthernet0/2
no ip address
duplex auto
speed auto
shutdown
!
interface Vlan1
no ip address
shutdown
!
ip classless
!
ip flow-export version 9
!
!
!
!
!
!
!
line con 0
!
line aux 0
!
line vty 0 4
login
!
!
!
end
10- Viewing and Filtering Configuration
R1#sh run | begin Hostname
R1#
R1#sh run | include interface
interface GigabitEthernet0/0
interface GigabitEthernet0/1
interface GigabitEthernet0/2
interface Vlan1
R1#sh run | exclude interface
Building configuration...
Current configuration : 737 bytes
!
version 15.1
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname R1
Output truncated –
11- IOS Configuration Management
R1#copy run start
Destination filename [startup-config]?
Building configuration...
[OK]
R1#config t
R1(config)#hostname RouterX
RouterX(config)#
RouterX(config)#do show startup-config
Using 690 bytes
!
version 15.1
no service timestamps log datetime msec
no service timestamps debug datetime msec
no service password-encryption
!
hostname RouterX
!
!
!
RouterX#copy run flash:
Destination filename [running-config]?
Building configuration...
[OK]
RouterX#copy run tftp
Address or name of remote host []? 10.10.10.10
Destination filename [RouterX-confg]?
Writing running-config........
%Error opening tftp://10.10.10.10/RouterX-confg (Timed out)
RouterX#reload
Proceed with reload? [confirm]
Conclusion
This lab provided a comprehensive introduction to navigating and using the Cisco IOS operating system. From basic command execution to configuration management, these steps lay the foundation for more advanced networking tasks.
By following this guide, you will gain a solid understanding of the Cisco IOS CLI, enabling you to effectively manage and troubleshoot Cisco devices in your network.