Configuring Advanced Static Switch Access Port Security on Cisco Catalyst Switches
Objective
The objective of this lab exercise is to learn and understand how to configure static MAC entries for port security. By default, MAC entries are learned dynamically on a switchport.
Purpose
Static port security MAC entries are an advanced skill. Static MAC address entries are manually configured by the administrator. As a Cisco engineer, understanding advanced features will give you the edge over your fellow CCNAs.
Lab Topology
Use the following topology to complete this lab exercise:
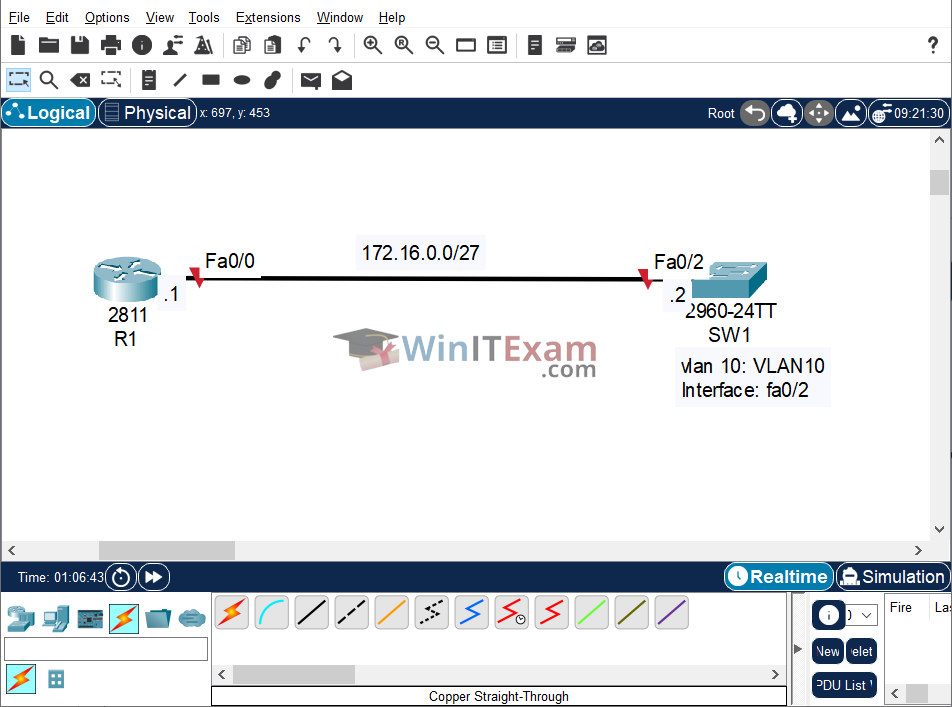
Task 1: Configure Hostnames and VLAN
Objective: Configure hostnames on SW1 and R1 as illustrated in the topology. Create VLAN10 on switch SW1 and assign port FastEthernet0/2 to this VLAN as an access port.
Configuration Steps:
SW1#config t Enter configuration commands, one per line. End with CTRL/Z. SW1(config)#hostname SW1 SW1(config)# R1#config t Enter configuration commands, one per line. End with CTRL/Z. R1(config)#hostname R1 R1(config)# SW1#config t Enter configuration commands, one per line. End with CTRL/Z. SW1(config)#vlan 10 SW1(config-vlan)#name VLAN10 SW1(config-vlan)#exit SW1(config)#interface fastethernet0/2 SW1(config-if)#switchport mode access SW1(config-if)#switchport access vlan 10 SW1(config-if)#end
Task 2: Configure IP Addresses
Objective: Configure IP address 172.16.0.1/27 on R1’s FastEthernet0/0 interface and IP address 172.16.0.2/27 on Sw2’s VLAN10 interface. Verify that R1 can ping SW1, and vice versa.
Configuration Steps:
R1#config t Enter configuration commands, one per line. End with CTRL/Z. R1(config)#interface fastethernet0/0 R1(config-if)#ip address 172.16.0.1 255.255.255.224 R1(config-if)#no shutdown R1(config-if)#end R1#copy running-config startup-config SW1#config t Enter configuration commands, one per line. End with CTRL/Z. SW1(config)#interface vlan10 SW1(config-if)#ip address 172.16.0.2 255.255.255.224 SW1(config-if)#no shutdown SW1(config-if)#end R1#ping 172.16.0.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.0.2, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/0 ms SW1#ping 172.16.0.1 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 172.16.0.1, timeout is 2 seconds: !!!!! Success rate is 100 percent (5/5), round-trip min/avg/max = 0/0/0 ms
Task 3: Configure Static Port Security MAC Entries
Objective: Configure port security on port FastEthernet0/2 on SW1 for the following static MAC addresses:
- 000a.1111.ab01
- 000b.2222.cd01
- 000c.3333.ef01
- 000d.4444.ac01
The switch should restrict access to these ports for MAC addresses that are not known. Verify your configuration with port-security commands in Cisco IOS.
Configuration:
SW1#conf t
Enter configuration commands, one per line. End with CNTL/Z.
SW1(config)#interface fastethernet0/2
SW1(config-if)#switchport port-security
SW1(config-if)#switchport port-security maximum 4
SW1(config-if)#switchport port-security mac-address 000a.1111.ab01
SW1(config-if)#switchport port-security mac-address 000b.2222.cd01
SW1(config-if)#switchport port-security mac-address 000c.3333.ef01
SW1(config-if)#switchport port-security mac-address 000d.4444.ac01
SW1(config-if)#end
SW1#copy running-config startup-config
Destination filename [startup-config]?
Building configuration...
[OK]
SW1#show port-security
Secure Port MaxSecureAddr CurrentAddr SecurityViolation Security Action
(Count) (Count) (Count)
--------------------------------------------------------------------
Fa0/2 4 4 0 Shutdown
----------------------------------------------------------------------
SW1#show port-security address
%SYS-5-CONFIG_I: Configured from console by console
Secure Mac Address Table
-----------------------------------------------------------------------------
Vlan Mac Address Type Ports Remaining Age
(mins)
---- ----------- ---- ----- -------------
10 000A.1111.AB01 SecureConfigured Fa0/2 -
10 000B.2222.CD01 SecureConfigured Fa0/2 -
10 000C.3333.EF01 SecureConfigured Fa0/2 -
10 000D.4444.AC01 SecureConfigured Fa0/2 -
-----------------------------------------------------------------------------
Total Addresses in System (excluding one mac per port) : 3
Max Addresses limit in System (excluding one mac per port) : 1024
Note: The requirements of this task seem pretty simple; however, a common mistake is often made by people who forget that by default, the maximum number of addresses that can be secured is one. Therefore, since you were given four MAC addresses, you need to increase the port security limit to four. Otherwise, if you did not add the switchport port-security maximum 4 command, you would receive the following error when trying to add the second static MAC address for port security:
SW1#conf t Enter configuration commands, one per line. End with CNTL/Z. SW1(config)#interface fastethernet0/5 SW1(config-if)#switchport port-security Command rejected: FastEthernet0/5 is a dynamic port. SW1(config-if)#switchport port-security mac-address 000a.1111.ab01 SW1(config-if)#switchport port-security mac-address 000b.2222.cd01 Total secure mac-addresses on interface FastEthernet0/5 has reached maximum limit.
Cisco Packet Tracer file:
Load and open the .pkt Lab file in Cisco Packet Tracer from here: Advanced_Static_Switch_Access_Port_Security.pkt