Configuring Inter-VLAN Routing with Router on a Stick (RoaS)
Objective
The objective of this lab exercise is to configure a router to provide inter-VLAN communication. By default, hosts in one VLAN cannot communicate with hosts in another VLAN without a router routing between the two VLANs.
Purpose
Inter-VLAN routing configuration is a fundamental skill. Most networks typically have more than one VLAN, and the hosts in these VLANs are required to communicate with each other if the need arises. As a Cisco engineer, as well as in the Cisco CCNA exam, you will be expected to know how to configure inter-VLAN routing. In this example, you don’t have a Layer 3 switch, so you must use a router to route.
Lab Topology
Use the following topology to complete this lab exercise:
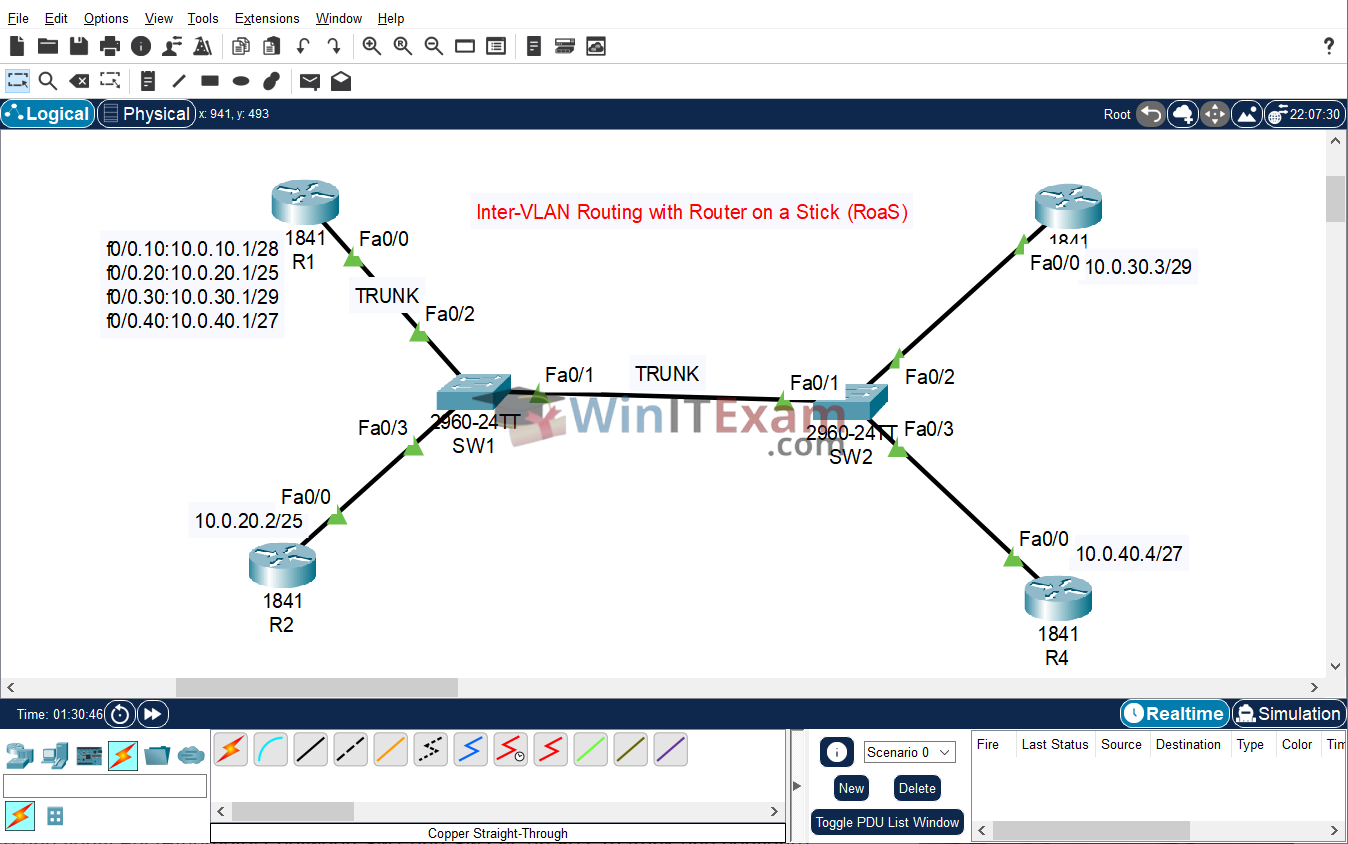
Task 1: Configure Hostnames
Objective: Configure a hostname on switches 1 and 2 and routers 1 through 4 as illustrated in the topology above.
Configuration:
Switch1#configure terminal Switch1(config)#hostname SW1 Switch2#configure terminal Switch2(config)#hostname SW2 Router1#configure terminal Router1(config)#hostname R1 Router2#configure terminal Router2(config)#hostname R2 Router3#configure terminal Router3(config)#hostname R3 Router4#configure terminal Router4(config)#hostname R4
Task 2: Configure VTP Transparent Mode
Objective: Configure and verify SW1 and SW2 as VTP Transparent switches. Both switches should be in the VTP domain named CISCO. Secure VTP messages with the password CISCO.
Configuration:
SW1#configure terminal SW1(config)#vtp mode transparent SW1(config)#vtp domain CISCO SW1(config)#vtp password CISCO SW1(config)#exit SW2#configure terminal SW2(config)#vtp mode transparent SW2(config)#vtp domain CISCO SW2(config)#vtp password CISCO SW2(config)#exit
Task 3: Configure Trunks and VLANs
Objective: Configure and verify FastEthernet0/1 between SW1 and SW2 as an 802.1q trunk and configure VLANs as depicted in the topology above. Assign ports to depicted VLANs and configure SW1 FastEthernet0/2 as a trunk. VLAN20 should have untagged Ethernet frames. Remember that on 802.1q trunks, only the native VLAN is untagged.
Configuration:
SW1#config t Enter configuration commands, one per line. End with CTRL/Z. SW1(config)#interface fastethernet0/1 SW1(config-if)#switchport mode trunk SW1(config-if)#exit SW1(config)#vlan 10 SW1(config-vlan)#name SALES SW1(config-vlan)#exit SW1(config)#vlan 20 SW1(config-vlan)#name TECH SW1(config-vlan)#exit SW1(config)#vlan 30 SW1(config-vlan)#name ADMIN SW1(config-vlan)#exit SW1(config)#vlan 40 SW1(config-vlan)#name TEST SW1(config-vlan)#exit SW1(config)#interface fastethernet0/2 SW1(config-if)#switchport mode trunk SW1(config-if)#switchport trunk native vlan 20 SW1(config-if)#exit SW1(config)#interface fastethernet0/3 SW1(config-if)#switchport mode access SW1(config-if)#switchport access vlan 20 SW1(config-if)#end SW1#show interfaces trunk Port Mode Encapsulation Status Native vlan Fa0/1 on 802.1q trunking 1 Fa0/2 on 802.1q trunking 20 Port Vlans allowed on trunk Fa0/1 1-1005 Fa0/2 1-1005 Port Vlans allowed and active in management domain Fa0/1 1,10,20,30,40 Fa0/2 1,10,20,30,40 Port Vlans in spanning tree forwarding state and not pruned Fa0/1 1,10,20,30,40 Fa0/2 1,10,20,30,40 SW2#config t Enter configuration commands, one per line. End with CTRL/Z. SW2(config)#interface fastethernet0/1 SW2(config-if)#switchport mode trunk SW2(config-if)#exit SW2(config)#vlan 10 SW2(config-vlan)#name SALES SW2(config-vlan)#exit SW2(config)#vlan 20 SW2(config-vlan)#name TECH SW2(config-vlan)#exit SW2(config)#vlan 30 SW2(config-vlan)#name ADMIN SW2(config-vlan)#exit SW2(config)#vlan 40 SW2(config-vlan)#name TEST SW2(config-vlan)#exit SW2(config)#interface fastethernet0/2 SW2(config-if)#switchport mode access SW2(config-if)#switchport access vlan 30 SW2(config-if)#exit SW2(config)#interface fastethernet0/3 SW2(config-if)#switchport mode access SW2(config-if)#switchport access vlan 40 SW2(config-if)#end SW2#show interfaces trunk Port Mode Encapsulation Status Native vlan Fa0/1 on 802.1q trunking 1 Port Vlans allowed on trunk Fa0/1 1-1005 Port Vlans allowed and active in management domain Fa0/1 1,10,20,30,40 Port Vlans in spanning tree forwarding state and not pruned Fa0/1 1
Task 4: Configure IP Addresses
Objective: Configure IP addresses on R2, R3, and R4 as illustrated in the Lab.
Configuration:
R2#configure terminal R2(config)#interface FastEthernet0/0 R2(config-if)#ip address 10.0.20.2 255.255.255.128 R2(config-if)#no shutdown R2(config-if)#end R3#configure terminal R3(config)#interface FastEthernet0/0 R3(config-if)#ip address 10.0.30.3 255.255.255.248 R3(config-if)#no shutdown R3(config-if)#end R4#configure terminal R4(config)#interface FastEthernet0/0 R4(config-if)#ip address 10.0.40.4 255.255.255.224 R4(config-if)#no shutdown R4(config-if)#end
Task 5: Configure Router Subinterfaces
Objective: Configure subinterfaces of R1 FastEthernet0/0 in the corresponding VLANs in the diagram. Also, configure interface VLAN10 on SW2 with the IP address 10.0.10.2/28.
Configuration:
R1#config t Enter configuration commands, one per line. End with CTRL/Z. R1(config)#interface fastethernet0/0 R1(config-if)#description "Connected To Switch Trunk Fa0/2" R1(config-if)#no shutdown R1(config-if)#exit R1(config)#interface fastethernet0/0.10 R1(config-subif)#description "Subinterface For VLAN 10" R1(config-subif)#encapsulation dot1Q 10 R1(config-subif)#ip address 10.0.10.1 255.255.255.240 R1(config-subif)#exit R1(config)#interface fastethernet0/0.20 R1(config-subif)#description "Subinterface For VLAN 20" R1(config-subif)#encapsulation dot1Q 20 native R1(config-subif)#ip address 10.0.20.1 255.255.255.128 R1(config-subif)#exit R1(config)#interface fastethernet0/0.30 R1(config-subif)#description "Subinterface For VLAN 30" R1(config-subif)#encapsulation dot1Q 30 R1(config-subif)#ip address 10.0.30.1 255.255.255.248 R1(config-subif)#exit R1(config)#interface fastethernet0/0.40 R1(config-subif)#description "Subinterface For VLAN 40" R1(config-subif)#encapsulation dot1Q 40 R1(config-subif)#ip address 10.0.40.1 255.255.255.224 R1(config-subif)#end R1#show ip interface brief Interface IP-Address OK? Method Status Protocol FastEthernet0/0 unassigned YES unset up up FastEthernet0/0.10 10.0.10.1 YES manual up up FastEthernet0/0.20 10.0.20.1 YES manual up up FastEthernet0/0.30 10.0.30.1 YES manual up up FastEthernet0/0.40 10.0.40.1 YES manual up up FastEthernet0/1 unassigned YES unset administratively down down Vlan1 unassigned YES unset administratively down down SW2(config)#interface vlan1 SW2(config-if)#shutdown SW2(config)#interface vlan10 SW2(config-if)#ip address 10.0.10.2 255.255.255.240 SW2(config-if)#no shutdown SW2(config)#end SW2#show ip interface brief Interface IP-Address OK? Method Status Protocol Vlan1 unassigned YES manual administratively down down Vlan10 10.0.10.2 YES manual up up
Task 6: Test Network Connectivity
Objective: Test network connectivity by pinging from R1 to routers R2, R3, and R4.
Configuration:
R1#ping 10.0.10.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.10.2, timeout is 2 seconds: ..!!! Success rate is 60 percent (3/5), round-trip min/avg/max = 0/0/0 ms R1#ping 10.0.20.2 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.20.2, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/0 ms R1#ping 10.0.30.3 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.30.3, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/0 ms R1#ping 10.0.40.4 Type escape sequence to abort. Sending 5, 100-byte ICMP Echos to 10.0.40.4, timeout is 2 seconds: .!!!! Success rate is 80 percent (4/5), round-trip min/avg/max = 0/0/0 ms NOTE: The first ping packet times out due to ARP resolution. Subsequent packets will be successful.
Cisco Packet Tracer file:
Load and open the .pkt Lab file in Cisco Packet Tracer from here: Inter-VLAN_Routing_with_Router_on_a_Stick.pkt