Question 741
Which two practices are recommended for an acceptable security posture in a network? (Choose two.)
A. Use a cryptographic keychain to authenticate to network devices.
B. Place internal email and file servers in a designated DMZ.
C. Back up device configurations to encrypted USB drives for secure retrieval.
D. Disable unused or unnecessary ports, interfaces, and services.
E. Maintain network equipment in a secure location.
Question 742
How does WPA3 improve security?
A. It uses SAE for authentication.
B. It uses RC4 for encryption.
C. It uses TKIP for encryption.
D. It uses a 4-way handshake for authentication.
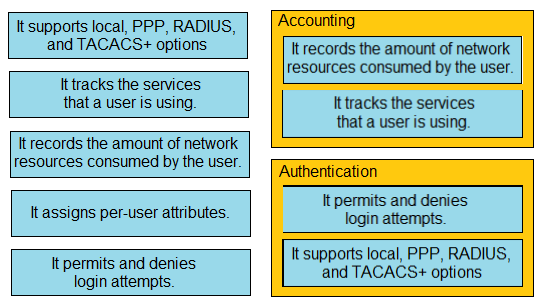
Question 743
DRAG DROP -Drag and drop the statements about AAA from the left onto the corresponding AAA services on the right. Not all options are used.
Select and Place:
Question 744
DRAG DROP -Drag and drop the elements of a security program from the left onto the corresponding descriptions on the right.
Select and Place:
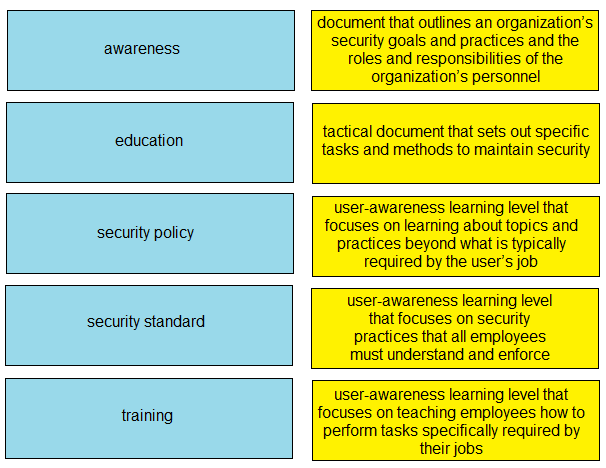
Question 745
What is the default port-security behavior on a trunk link?
A. It places the port in the err-disabled state if it learns more than one MAC address.
B. It causes a network loop when a violation occurs.
C. It disables the native VLAN configuration as soon as port security is enabled.
D. It places the port in the err-disabled state after 10 MAC addresses are statically configured.
Question 746
An engineer is configuring remote access to a router from IP subnet 10.139.58.0/28. The domain name, crypto keys, and SSH have been configured. Which configuration enables the traffic on the destination router?
A. line vty 0 15 access-class 120 in ! ip access-list extended 120 permit tcp 10.139.58.0 0.0.0.15 any eq 22
B. interface FastEthernet0/0 ip address 10.122.49.1 255.255.255.252 ip access-group 10 in ! ip access-list standard 10 permit udp 10.139.58.0 0.0.0.7 host 10.122.49.1 eq 22
C. interface FastEthernet0/0 ip address 10.122.49.1 255.255.255.252 ip access-group 110 in ! ip access-list standard 110 permit tcp 10.139.58.0 0.0.0.15 eq 22 host 10.122.49.1
D. line vty 0 15 access-group 120 in ! ip access-list extended 120 permit tcp 10.139.58.0 0.0.0.15 any eq 22
Question 747
In an SDN architecture, which function of a network node is centralized on a controller?
A. Creates the IP routing table
B. Discards a message due filtering
C. Makes a routing decision
D. Provides protocol access for remote access devices
Question 748
Refer to the exhibit. What are the two steps an engineer must take to provide the highest encryption and authentication using domain credentials from LDAP?(Choose two.)
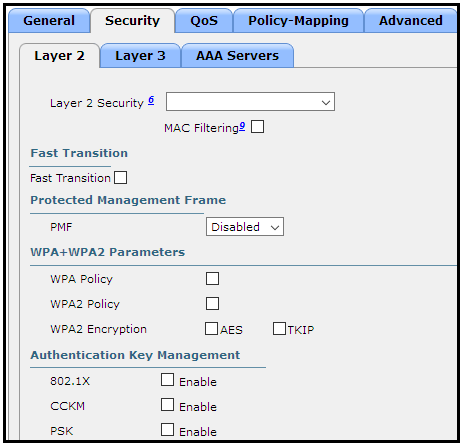
A. Select PSK under Authentication Key Management.
B. Select Static-WEP + 802.1X on Layer 2 Security.
C. Select WPA+WPA2 on Layer 2 Security.
D. Select 802.1X from under Authentication Key Management.
E. Select WPA Policy with TKIP Encryption.
Question 749
Which enhancement is implemented in WPA3?
A. employs PKI to identify access points
B. applies 802.1x authentication
C. uses TKIP
D. protects against brute force attacks
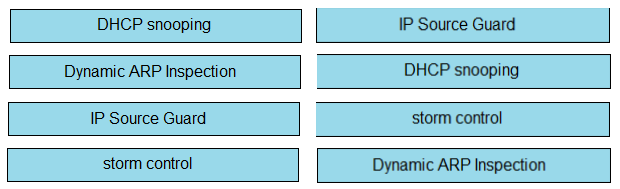
Question 750
DRAG DROP -Drag and drop the Cisco IOS attack mitigation features from the left onto the types of network attack they mitigate on the right.
Select and Place: