Question 731
What is a function of Opportunistic Wireless Encryption in an environment?
A. provide authentication
B. protect traffic on open networks
C. offer compression
D. increase security by using a WEP connection
Question 732
DRAG DROP -Drag and drop the AAA features from the left onto the corresponding AAA security services on the right. Not all options are used.
Select and Place:
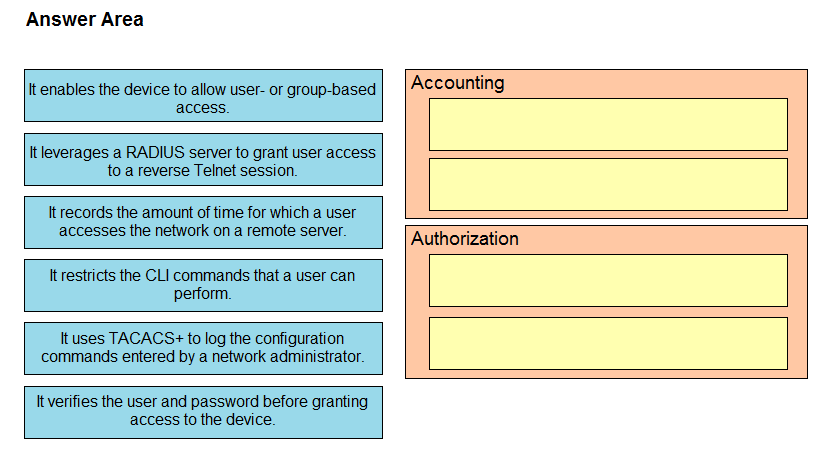
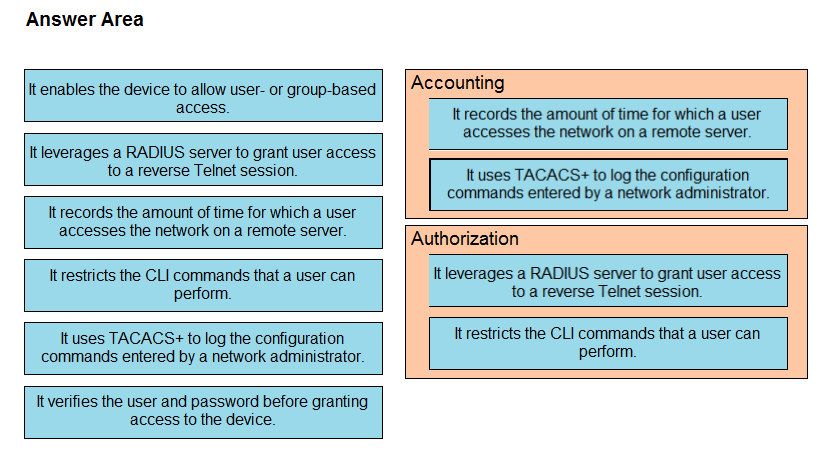
Question 733
Refer to the exhibit. Clients on the WLAN are required to use 802.11r. What action must be taken to meet the requirement?
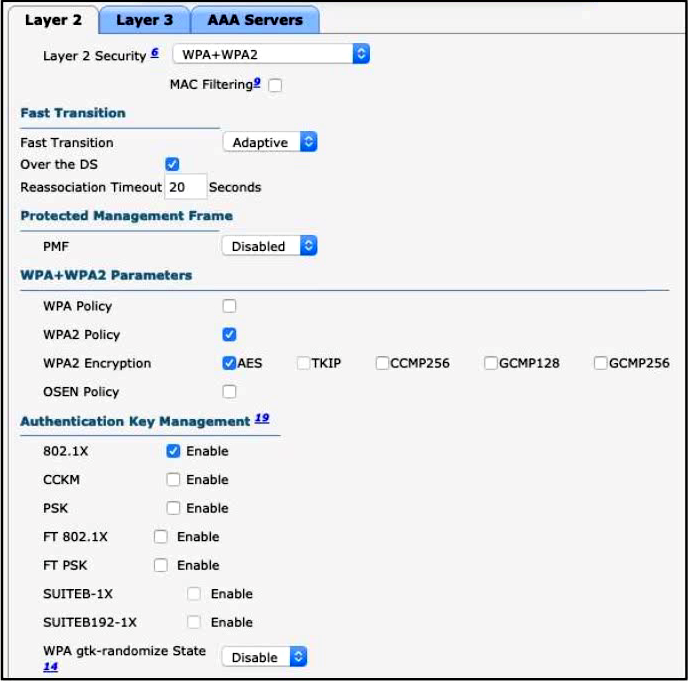
A. Under Protected Management Frames, set the PMF option to Required.
B. Enable CCKM under Authentication Key Management.
C. Set the Fast Transition option and the WPA gtk-randomize State to disable.
D. Set the Fast Transition option to Enable and enable FT 802.1X under Authentication Key Management.
Question 734
Refer to the exhibit. What must be configured to enable 802.11w on the WLAN?
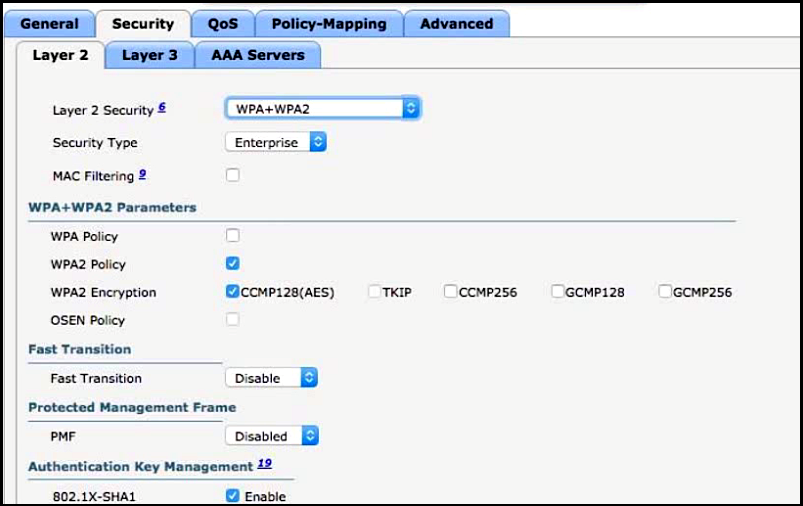
A. Set Fast Transition to Enabled.
B. Enable WPA Policy.
C. Set PMF to Required.
D. Enable MAC Filtering.
Question 735
Which encryption method is used by WPA3?
A. TKIP
B. AES
C. SAE
D. PSK
Question 736
After a recent security breach and a RADIUS failure, an engineer must secure the console port of each enterprise router with a local username and password.
Which configuration must the engineer apply to accomplish this task?
A. aaa new-model line con 0 password plaintextpassword privilege level 15
B. aaa new-model aaa authorization exec default local aaa authentication login default radius username localuser privilege 15 secret plaintextpassword
C. username localuser secret plaintextpassword line con 0 no login local privilege level 15
D. username localuser secret plaintextpassword line con 0 login authentication default privilege level 15
Question 737
Which wireless security protocol relies on Perfect Forward Secrecy?
A. WEP
B. WPA2
C. WPA
D. WPA3
Question 738
A network engineer is replacing the switches that belong to a managed-services client with new Cisco Catalyst switches. The new switches will be configured for updated security standards including replacing.
Telnet services with encrypted connections and doubling the modulus size from 1024. Which two commands must the engineer configure on the new switches?(Choose two.)
A. transport input ssh
B. transport input all
C. crypto key generate rsa modulus 2048
D. crypto key generate rsa general-keys modulus 1024
E. crypto key generate rsa usage-keys
Question 739
What are two examples of multifactor authentication? (Choose two.)
A. single sign-on
B. soft tokens
C. passwords that expire
D. shared password repository
E. unique user knowledge
Question 740
Which characteristic differentiates the concept of authentication from authorization and accounting?
A. consumption-based billing
B. identity verification
C. user-activity logging
D. service limitations



