Question 721
A network engineer is asked to configure VLANS 2, 3, and 4 for a new implementation. Some ports must be assigned to the new VLANS with unused ports remaining. Which action should be taken for the unused ports?
A. configure in a nondefault native VLAN
B. configure ports in the native VLAN
C. configure ports in a black hole VLAN
D. configure ports as access ports
Question 722
When a WPA2-PSK WLAN is configured in the Wireless LAN Controller, what is the minimum number of characters that is required in ASCII format?
A. 6
B. 8
C. 12
D. 18
Question 723
What mechanism carries multicast traffic between remote sites and supports encryption?
A. ISATAP
B. IPsec over ISATAP
C. GRE
D. GRE over IPsec
Question 724
Refer to the exhibit. An access-list is required to permit traffic from any host on interface Gi0/0 and deny traffic from interface Gi0/1. Which access list must be applied?
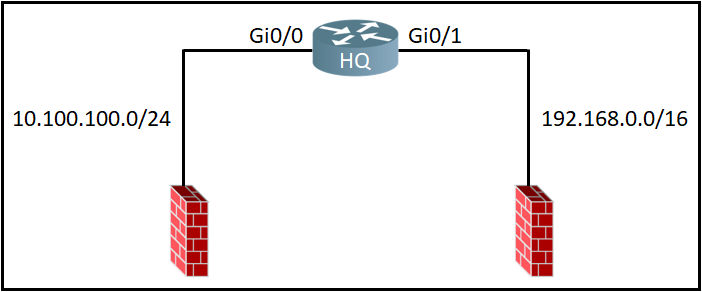
A. ip access-list standard 99 permit 10.100.100.0 0.0.0.255 deny 192.168.0.0 0.0.255.255
B. ip access-list standard 99 permit 10.100.100.0 0.0.0.255 deny 192.168.0.0 0.255.255.255
C. ip access-list standard 199 permit 10.100.100.0 0.0.0.255 deny 192.168.0.0 0.255.255.255
D. ip access-list standard 199 permit 10.100.100.0 0.0.0.255 deny 192.168.0.0 0.0.255.255
Question 725
Refer to the exhibit. Which two commands must be configured on router R1 to enable the router to accept secure remote-access connections? (Choose two.)
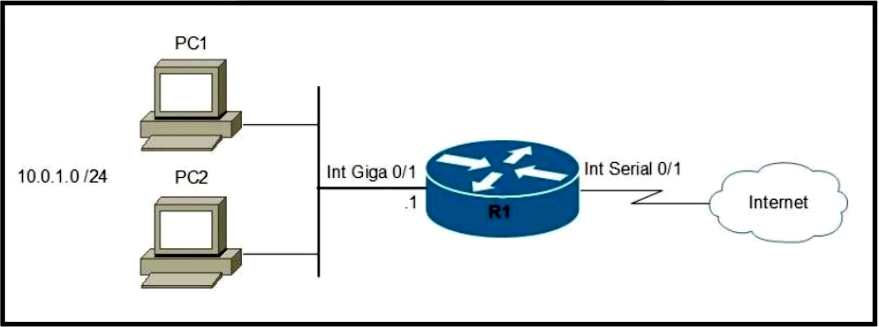
A. ip ssh pubkey-chain
B. username cisco password 0 cisco
C. crypto key generate rsa
D. transport input telnet
E. login console
Question 726
Which service is missing when RADIUS is selected to provide management access to the WLC?
A. authorization
B. authentication
C. accounting
D. confidentiality
Question 727
Which action implements physical access control as part of the security program of an organization?
A. setting up IP cameras to monitor key infrastructure
B. configuring a password for the console port
C. backing up syslogs at a remote location
D. configuring enable passwords on network devices
Question 728
Which field within the access-request packet is encrypted by RADIUS?
A. authorized services
B. password
C. authenticator
D. username
Question 729
A Cisco engineer is configuring a factory-default router with these three passwords:
- The user EXEC password for console access is p4ssw0rd1.
- The user EXEC password for Telnet access is s3cr3t2.
- The password for privileged EXEC mode is priv4t3p4ss.
Which command sequence must the engineer configure?
A. enable secret priv4t3p4ss ! line con 0 password p4ssw0rd1 ! line vty 0 15 password s3cr3t2
B. enable secret priv4t3p4ss ! line con 0 password p4ssw0rd1 login ! line vty 0 15 password s3cr3t2 login
C. enable secret priv4t3p4ss ! line con 0 password login p4ssw0rd1 ! line vty 0 15 password login s3cr3t2 login
D. enable secret privilege 15 priv4t3p4ss ! line con 0 password p4ssw0rd1 login ! line vty 0 15 password s3cr3t2 login
Question 730
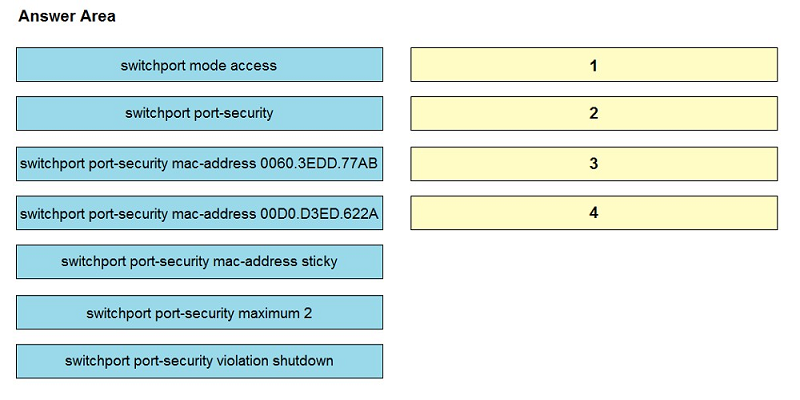
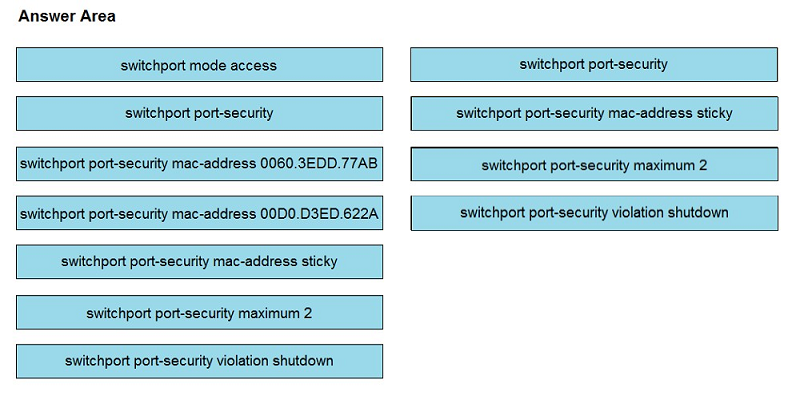
DRAG DROP -An engineer is tasked to configure a switch with port security to ensure devices that forward unicasts, multicasts, and broadcasts are unable to flood the port. The port must be configured to permit only two random MAC addresses at a time. Drag and drop the required configuration commands from the left onto the sequence on the right. Not all commands are used.
Select and Place: