Question 711
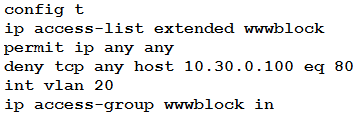
Refer to the exhibit. A network engineer must block access for all computers on VLAN 20 to the web server via HTTP. All other computers must be able to access the web server. Which configuration when applied to switch A accomplishes the task?
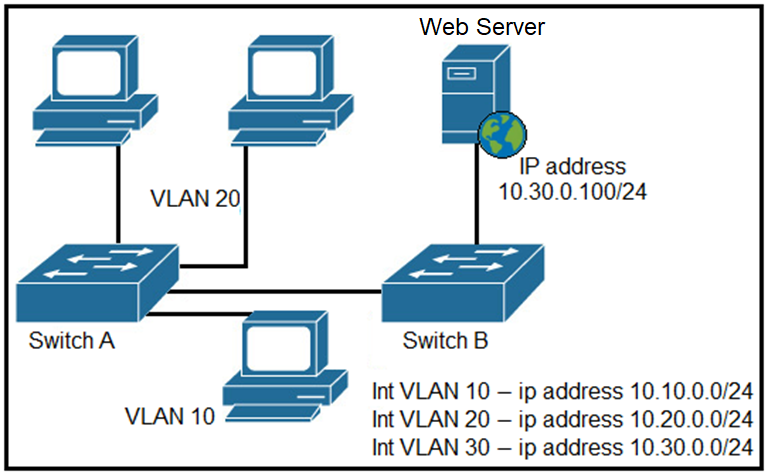
A.
B.
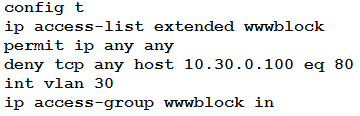
C.
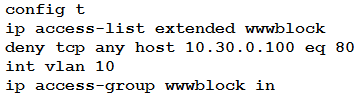
D.
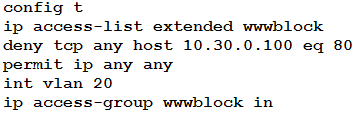
Question 712
In which two ways does a password manager reduce the chance of a hacker stealing a user's password? (Choose two.)
A. It encourages users to create stronger passwords
B. It uses an internal firewall to protect the password repository from unauthorized access
C. It stores the password repository on the local workstation with built-in antivirus and anti-malware functionality
D. It automatically provides a second authentication factor that is unknown to the original user
E. It protects against keystroke logging on a compromised device or web site
Question 713
Which goal is achieved by the implementation of private IPv4 addressing on a network?
A. provides an added level of protection against Internet exposure
B. provides a reduction in size of the forwarding table on network routers
C. allows communication across the Internet to other private networks
D. allows servers and workstations to communicate across public network boundaries
Question 714
Which type of attack is mitigated by dynamic ARP inspection?
A. DDoS
B. malware
C. man-in-the-middle
D. worm
Question 715
What are two recommendations for protecting network ports from being exploited when located in an office space outside of an IT closet? (Choose two.)
A. enable the PortFast feature on ports
B. configure static ARP entries
C. configure ports to a fixed speed
D. implement port-based authentication
E. shut down unused ports
Question 716
A port security violation has occurred on a switch port due to the maximum MAC address count being exceeded. Which command must be configured to increment the security-violation count and forward an SNMP trap?
A. switchport port-security violation access
B. switchport port-security violation protect
C. switchport port-security violation restrict
D. switchport port-security violation shutdown
Question 717
A network administrator must configure SSH for remote access to router R1. The requirement is to use a public and private key pair to encrypt management traffic to and from the connecting client. Which configuration, when applied, meets the requirements?
A. R1#enable R1#configure terminal R1(config)#ip domain-name cisco.com R1(config)#crypto key generate ec keysize 1024
B. R1#enable R1#configure terminal R1(config)#ip domain-name cisco.com R1(config)#crypto key generate ec keysize 2048
C. R1#enable R1#configure terminal R1(config)#ip domain-name cisco.com R1(config)#crypto key encrypt rsa name myKey
D. R1#enable R1#configure terminal R1(config)#ip domain-name cisco.com R1(config)#crypto key generate rsa modulus 1024
Question 718
When a WLAN with WPA2 PSK is configured in the Wireless LAN Controller GUI, which format is supported?
A. decimal
B. ASCII
C. unicode
D. base64
Question 719
Which two protocols must be disabled to increase security for management connections to a Wireless LAN Controller? (Choose two.)
A. HTTPS
B. SSH
C. HTTP
D. Telnet
E. TFTP
Question 720
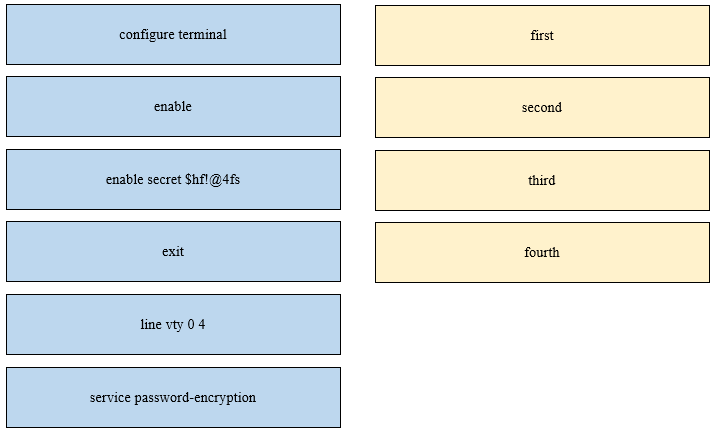
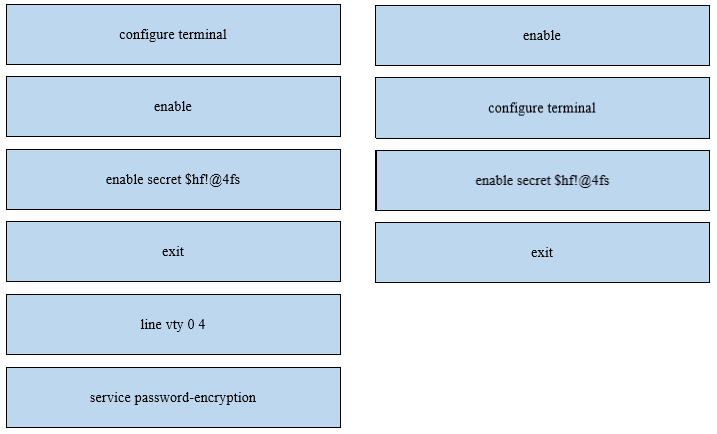
DRAG DROP -An engineer is configuring an encrypted password for the enable command on a router where the local user database has already been configured. Drag and drop the configuration commands from the left into the correct sequence on the right. Not all commands are used.
Select and Place: