Question 701
Refer to the exhibit. Which configuration for RTR-1 denies SSH access from PC-1 to any RTR-1 interface and allows all other traffic?
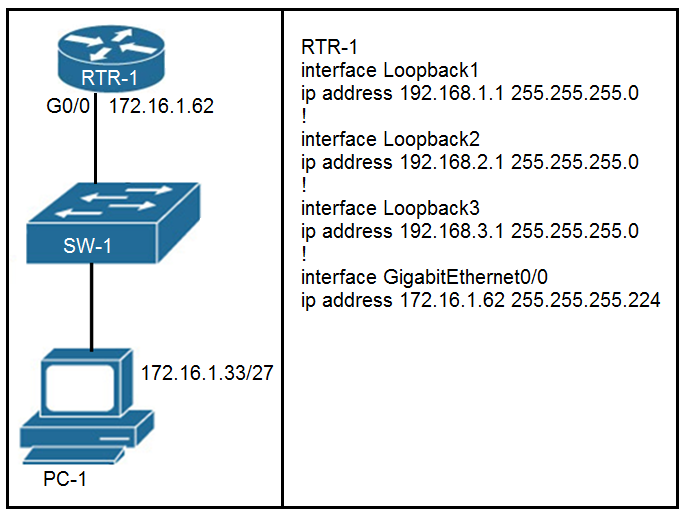
A.
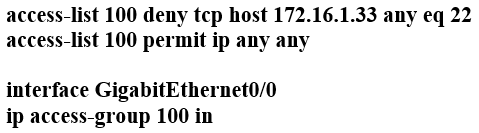
B.
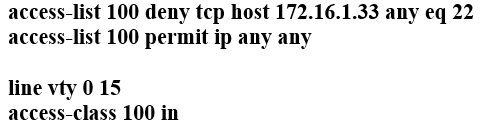
C.
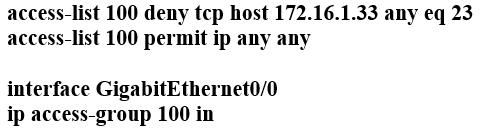
D.
Question 702
While examining excessive traffic on the network, it is noted that all incoming packets on an interface appear to be allowed even though an IPv4 ACL is applied to the interface. Which two misconfigurations cause this behavior? (Choose two.)
A. The ACL is empty
B. A matching permit statement is too broadly defined
C. The packets fail to match any permit statement
D. A matching deny statement is too high in the access list
E. A matching permit statement is too high in the access list
Question 703
The service password-encryption command is entered on a router. What is the effect of this configuration?
A. restricts unauthorized users from viewing clear-text passwords in the running configuration
B. prevents network administrators from configuring clear-text passwords
C. protects the VLAN database from unauthorized PC connections on the switch
D. encrypts the password exchange when a VPN tunnel is established
Question 704
Which WPA3 enhancement protects against hackers viewing traffic on the Wi-Fi network?
A. SAE encryption
B. TKIP encryption
C. scrambled encryption key
D. AES encryption
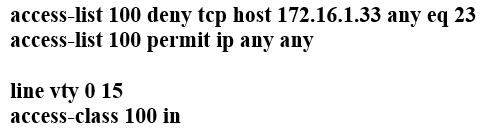
Question 705
Refer to the exhibit. If the network environment is operating normally, which type of device must be connected to interface fastethernet 0/1?
A. DHCP client
B. access point
C. router
D. PC
Question 706
Refer to the exhibit. An administrator configures four switches for local authentication using passwords that are stored as a cryptographic hash. The four switches must also support SSH access for administrators to manage the network infrastructure. Which switch is configured correctly to meet these requirements?
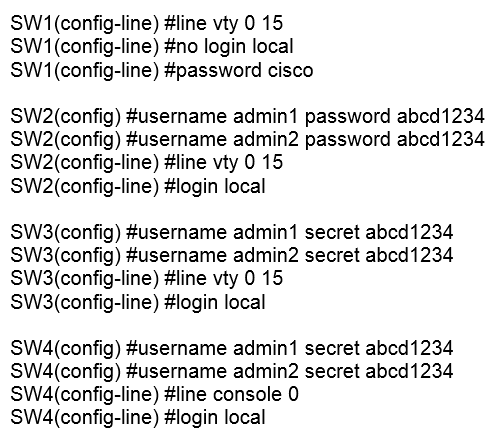
A. SW1
B. SW2
C. SW3
D. SW4
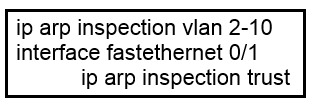
Question 707
Refer to the exhibit. What is the effect of this configuration?

A. The switch discards all ingress ARP traffic with invalid MAC-to-IP address bindings.
B. All ARP packets are dropped by the switch.
C. Egress traffic is passed only if the destination is a DHCP server.
D. All ingress and egress traffic is dropped because the interface is untrusted.
Question 708
When a site-to-site VPN is used, which protocol is responsible for the transport of user data?
A. IPsec
B. IKEv1
C. MD5
D. IKEv2
Question 709
Which type of wireless encryption is used for WPA2 in preshared key mode?
A. AES-128
B. TKIP with RC4
C. AES-256
D. RC4
Question 710
Which command prevents passwords from being stored in the configuration as plain text on a router or switch?
A. enable secret
B. enable password
C. service password-encryption
D. username cisco password encrypt







