Question 691
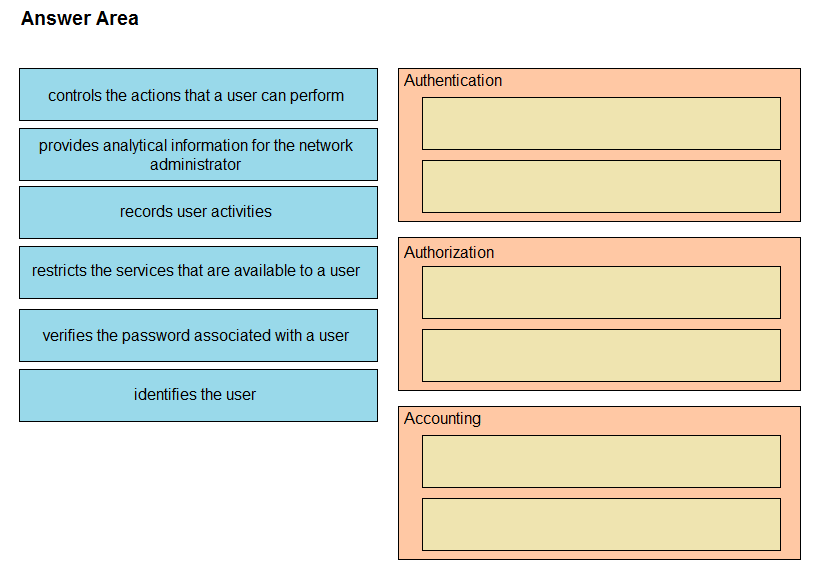
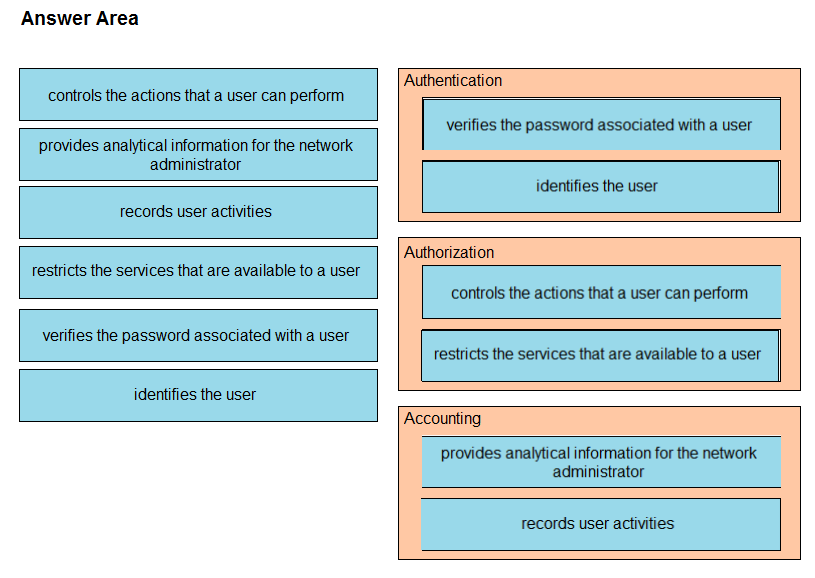
DRAG DROP -Drag and drop the AAA functions from the left onto the correct AAA services on the right.
Select and Place:
Question 692
An engineer is asked to protect unused ports that are configured in the default VLAN on a switch. Which two steps will fulfill the request? (Choose two.)
A. Configure the ports as trunk ports.
B. Enable the Cisco Discovery Protocol.
C. Configure the port type as access and place in VLAN 99.
D. Administratively shut down the ports.
E. Configure the ports in an EtherChannel.
Question 693
An email user has been lured into clicking a link in an email sent by their company's security organization. The webpage that opens reports that it was safe, but the link may have contained malicious code.
Which type of security program is in place?
A. user awareness
B. brute force attack
C. physical access control
D. social engineering attack
Question 694
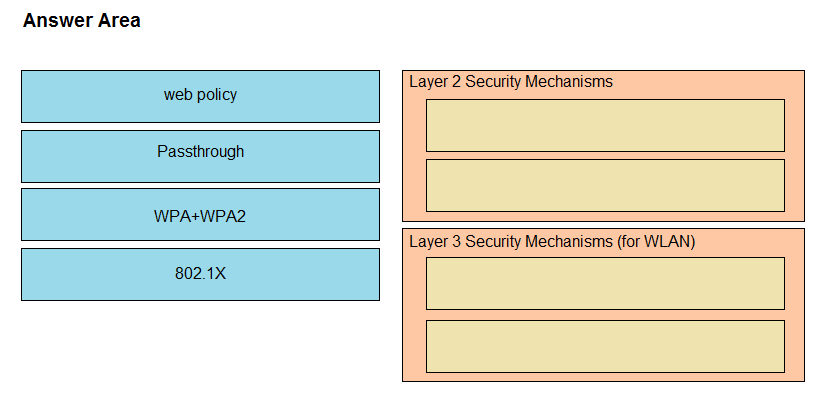
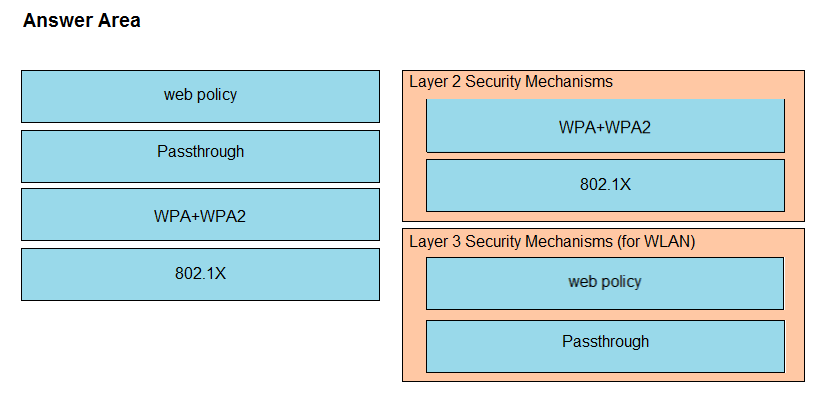
DRAG DROP -Drag and drop the Cisco Wireless LAN Controller security settings from the left onto the correct security mechanism categories on the right.
Select and Place:
Question 695
Which feature on the Cisco Wireless LAN Controller when enabled restricts management access from specific networks?
A. TACACS
B. CPU ACL
C. Flex ACL
D. RADIUS
Question 696
Which set of actions satisfy the requirement for multifactor authentication?
A. The user enters a user name and password, and then re-enters the credentials on a second screen.
B. The user swipes a key fob, then clicks through an email link.
C. The user enters a user name and password, and then clicks a notification in an authentication app on a mobile device.
D. The user enters a PIN into an RSA token, and then enters the displayed RSA key on a login screen.
Question 697
Which configuration is needed to generate an RSA key for SSH on a router?
A. Configure VTY access.
B. Configure the version of SSH.
C. Assign a DNS domain name.
D. Create a user with a password.
Question 698
Refer to the exhibit. An extended ACL has been configured and applied to router R2. The configuration failed to work as intended.
Which two changes stop outbound traffic on TCP ports 25 and 80 to 10.0.20.0/26 from the 10.0.10.0/26 subnet while still allowing all other traffic? (Choose two.)
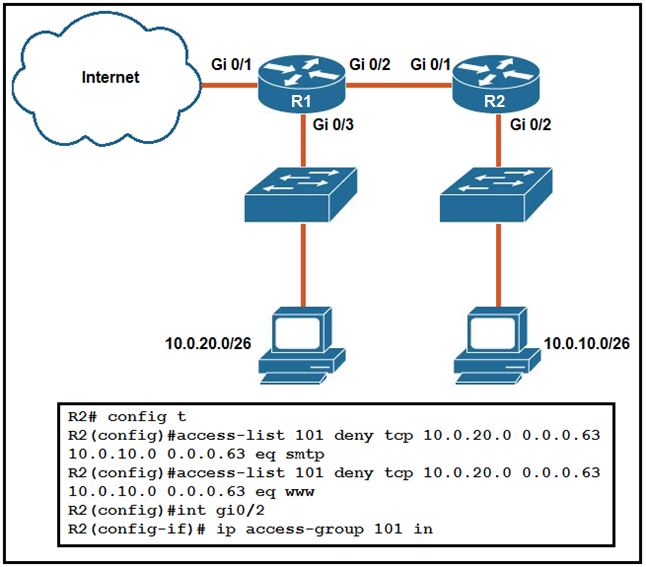
A. Add a "permit ip any any" statement at the end of ACL 101 for allowed traffic.
B. Add a "permit ip any any" statement to the beginning of ACL 101 for allowed traffic.
C. The ACL must be moved to the Gi0/1 interface outbound on R2.
D. The source and destination IPs must be swapped in ACL 101.
E. The ACL must be configured the Gi0/2 interface inbound on R1.
Question 699
An engineer must configure a WLAN using the strongest encryption type for WPA2-PSK. Which cipher fulfills the configuration requirement?
A. WEP
B. AES
C. RC4
D. TKIP
Question 700
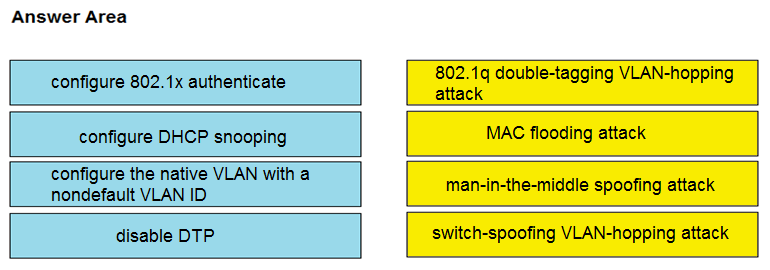
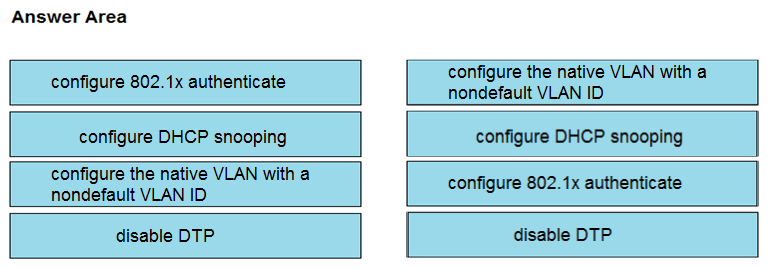
DRAG DROP -Drag and drop the attack-mitigation techniques from the left onto the types of attack that they mitigate on the right.
Select and Place: