Question 681
A network administrator enabled port security on a switch interface connected to a printer. What is the next configuration action in order to allow the port to learn the MAC address of the printer and insert it into the table automatically?
A. enable dynamic MAC address learning
B. implement static MAC addressing
C. enable sticky MAC addressing
D. implement auto MAC address learning
Question 682
Refer to the exhibit. An engineer booted a new switch and applied this configuration via the console port. Which additional configuration must be applied to allow administrators to authenticate directly to enable privilege mode via Telnet using a local username and password?
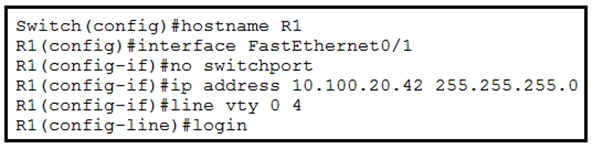
A. R1(config)#username admin R1(config-if)#line vty 0 4 R1(config-line)#password p@ss1234 R1(config-line)#transport input telnet
B. R1(config)#username admin privilege 15 secret p@ss1234 R1(config-if)#line vty 0 4 R1(config-line)#login local
C. R1(config)#username admin secret p@ss1234 R1(config-if)#line vty 0 4 R1(config-line)#login local R1(config)#enable secret p@ss1234
D. R1(config)#username admin R1(config-if)#line vty 0 4 R1(config-line)#password p@ss1234
Question 683
Which effect does the aaa new-model configuration command have?
A. It enables AAA services on the device.
B. It configures the device to connect to a RADIUS server for AAA.
C. It associates a RADIUS server to the group.
D. It configures a local user on the device.
Question 684
Refer to the exhibit. Which two events occur on the interface, if packets from an unknown Source address arrive after the interface learns the maximum number of secure MAC address? (Choose two.)
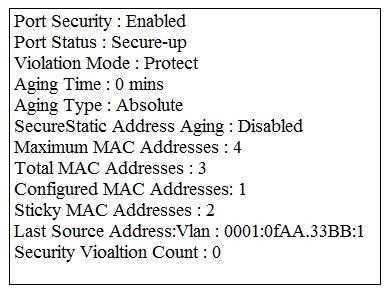
A. The security violation counter dose not increment
B. The port LED turns off
C. The interface is error-disabled
D. A syslog message is generated
E. The interface drops traffic from unknown MAC address
Question 685
Which technology must be implemented to configure network device monitoring with the highest security?
A. IP SLA
B. syslog
C. NetFlow
D. SNMPv3
Question 686
Refer to the exhibit. Which two statements about the interface that generated the output are true? (Choose two.)
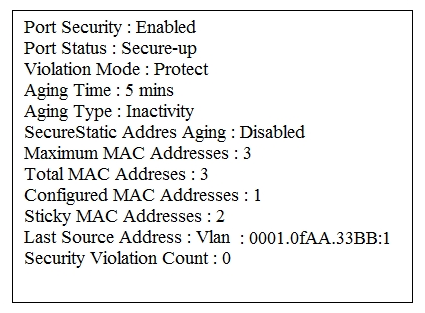
A. learned MAC addresses are deleted after five minutes of inactivity
B. the interface is error-disabled if packets arrive from a new unknown source address
C. it has dynamically learned two secure MAC addresses
D. it has dynamically learned three secure MAC addresses
E. the security violation counter increments if packets arrive from a new unknown source address
Question 687
Refer to the exhibit. Which statement about the interface that generated the output is true?
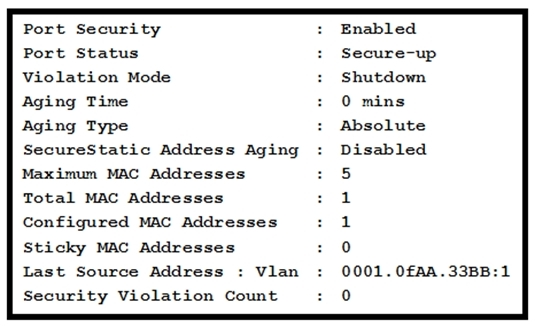
A. A syslog message is generated when a violation occurs.
B. One secure MAC address is manually configured on the interface.
C. One secure MAC address is dynamically learned on the interface.
D. Five secure MAC addresses are dynamically learned on the interface.
Question 688
Refer to the exhibit. What is the effect of this configuration?

A. The switch port remains administratively down until the interface is connected to another switch.
B. Dynamic ARP Inspection is disabled because the ARP ACL is missing.
C. The switch port interface trust state becomes untrusted.
D. The switch port remains down until it is configured to trust or untrust incoming packets.
Question 689
What is the difference between AAA authentication and authorization?
A. Authentication identifies and verifies a user who is attempting to access a system, and authorization controls the tasks the user performs.
B. Authentication controls the system processes a user accesses, and authorization logs the activities the user initiates.
C. Authentication verifies a username and password, and authorization handles the communication between the authentication agent and the user database.
D. Authentication identifies a user who is attempting to access a system, and authorization validates the user's password.
Question 690
When configuring a WLAN with WPA2 PSK in the Cisco Wireless LAN Controller GUI, which two formats are available to select? (Choose two.)
A. decimal
B. ASCII
C. hexadecimal
D. binary
E. base64




