Question 751
Refer to the exhibit. An engineer is updating the management access configuration of switch SW1 to allow secured, encrypted remote configuration. Which two commands or command sequences must the engineer apply to the switch? (Choose two.)
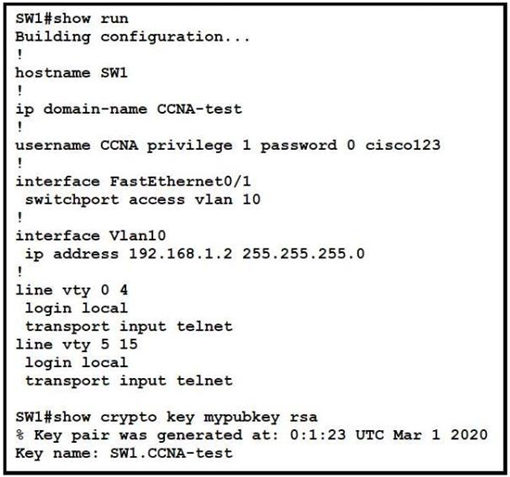
A. SW1(config)#enable secret ccnaTest123
B. SW1(config)#username NEW secret R3mote123
C. SW1(config)#line vty 0 15 SW1(config-line)#transport input ssh
D. SW1(config)# crypto key generate rsa
E. SW1(config)# interface f0/1 SW1(confif-if)# switchport mode trunk
Question 752
Which port security violation mode allows from valid MAC addresses to pass but blocks traffic from invalid MAC addresses?
A. restrict
B. shutdown
C. protect
D. shutdown VLAN
Question 753
A customer wants to provide wireless access to contractors using a guest portal on Cisco ISE. The portal is also used by employees. A solution is implemented, but contractors receive a certificate error when they attempt to access the portal. Employees can access the portal without any errors. Which change must be implemented to allow the contractors and employees to access the portal?
A. Install an Internal CA signed certificate on the Cisco ISE.
B. Install a trusted third-party certificate on the Cisco ISE.
C. Install an internal CA signed certificate on the contractor devices.
D. Install a trusted third-party certificate on the contractor devices.
Question 754
Which two wireless security standards use counter mode cipher block chaining Message Authentication Code Protocol for encryption and data integrity? (Choose two.)
A. Wi-Fi 6
B. WPA3
C. WEP
D. WPA2
E. WPA
Question 755
A network engineer is implementing a corporate SSID for WPA3-Personal security with a PSK. Which encryption cipher must be configured?
A. CCMP128
B. GCMP256
C. CCMP256
D. GCMP128
Question 756
What is a practice that protects a network from VLAN hopping attacks?
A. Implement port security on internet-facing VLANs
B. Enable dynamic ARP inspection
C. Assign all access ports to VLANs other than the native VLAN
D. Configure an ACL to prevent traffic from changing VLANs
Question 757
An administrator must use the password complexity not manufacturer-name command to prevent users from adding `Cisco` as a password. Which command must be issued before this command?
A. login authentication my-auth-list
B. service password-encryption
C. password complexity enable
D. confreg 0x2142
Question 758
An organization has decided to start using cloud-provided services. Which cloud service allows the organization to install its own operating system on a virtual machine?
A. platform-as-a-service
B. network-as-a-service
C. software-as-a-service
D. infrastructure-as-a-service
Question 759
How do traditional campus device management and Cisco DNA Center device management differ in regards to deployment?
A. Traditional campus device management allows a network to scale more quickly than with Cisco DNA Center device management.
B. Cisco DNA Center device management can deploy a network more quickly than traditional campus device management.
C. Cisco DNA Center device management can be implemented at a lower cost than most traditional campus device management options.
D. Traditional campus device management schemes can typically deploy patches and updates more quickly than Cisco DNA Center device management.
Question 760
Which purpose does a northbound API serve in a controller-based networking architecture?
A. facilitates communication between the controller and the applications
B. reports device errors to a controller
C. generates statistics for network hardware and traffic
D. communicates between the controller and the physical network hardware
