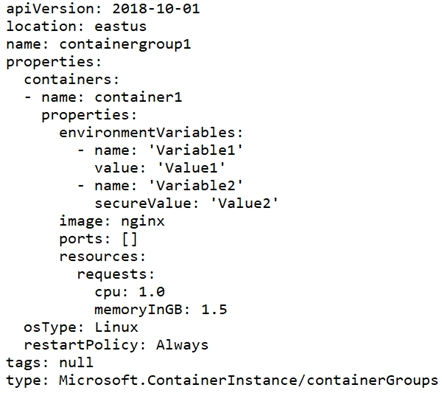
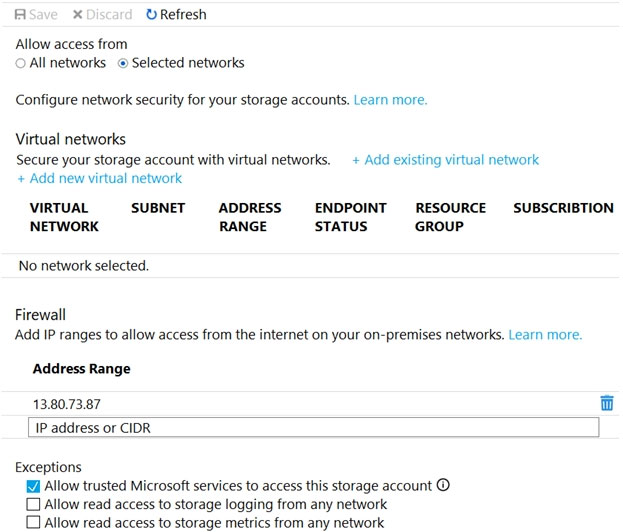
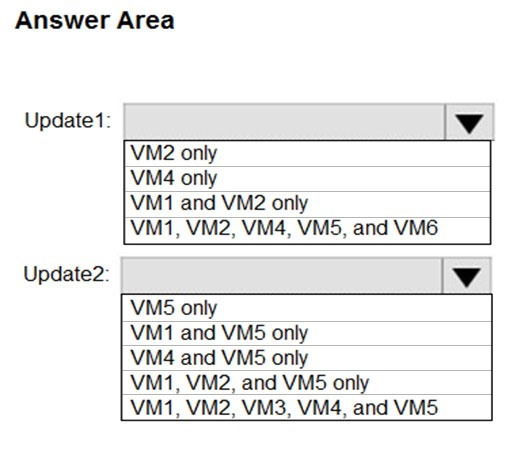
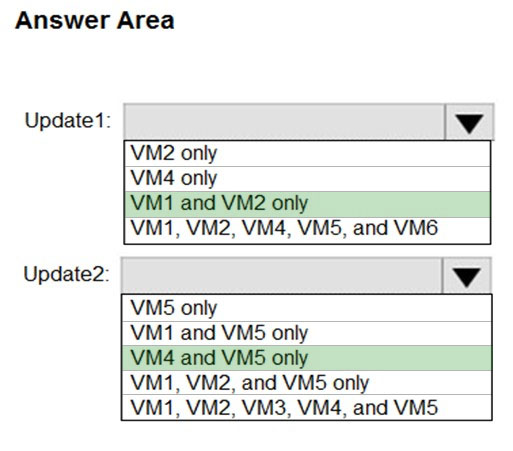
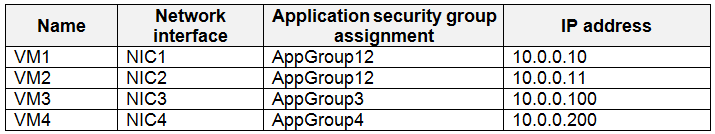
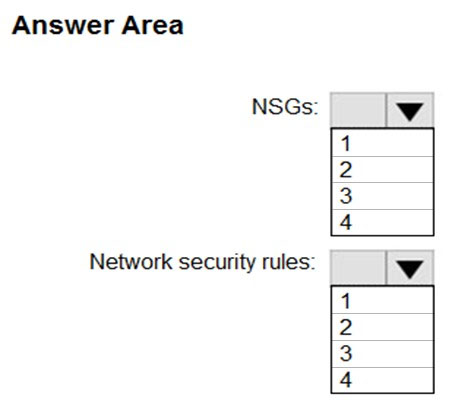
Locking prevents other users in your organization from accidentally deleting or modifying critical resources, such as Azure subscription, resource group, or resource.
Note: In Azure, the term resource refers to an entity managed by Azure. For example, virtual machines, virtual networks, and storage accounts are all referred to as Azure resources.
1. In the Azure portal, type Virtual Networks in the search box, select Virtual Networks from the search results then select VNET2. Alternatively, browse to
Virtual Networks in the left navigation pane.
2. In the Settings blade for virtual network VNET2, select Locks.
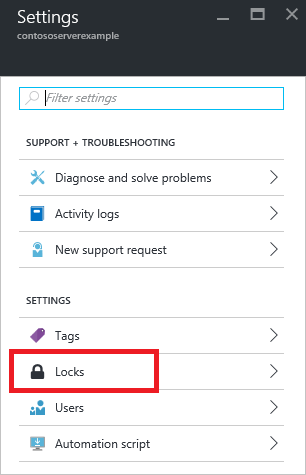
3. To add a lock, select Add.
4. For Lock type select Delete lock, and click OK
Reference:
https://docs.microsoft.com/en-us/azure/azure-resource-manager/resource-group-lock-resources