Question 491
Which level of severity must be set to get informational syslogs?
A. alert
B. critical
C. notice
D. debug
Question 492
How does QoS optimize voice traffic?
A. reducing bandwidth usage
B. by reducing packet loss
C. by differentiating voice and video traffic
D. by increasing jitter
Question 493
Refer to the exhibit. What is the metric of the route to the 192.168.10.33/28 subnet?

A. 84
B. 110
C. 128
D. 192
E. 193
Question 494
Which two protocols must be disabled to increase security for management connections to a Wireless LAN Controller?(Choose two )
A. Telnet
B. SSH
C. HTTP
D. HTTPS
E. TFTP
Question 495
Which function is performed by DHCP snooping?
A. propagates VLAN information between switches
B. listens to multicast traffic for packet forwarding
C. provides DDoS mitigation
D. rate-limits certain traffic
Question 496
When a client and server are not on the same physical network, which device is used to forward requests and replies between client and server for DHCP?
A. DHCP relay agent
B. DHCP server
C. DHCPDISCOVER
D. DHCPOFFER
Question 497
Which plane is centralized by an SON controller?
A. management-plane
B. control-plane
C. data-plane
D. services-plane
Question 498
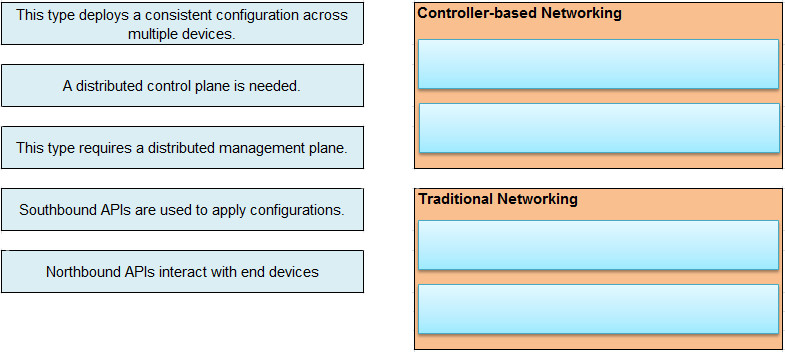
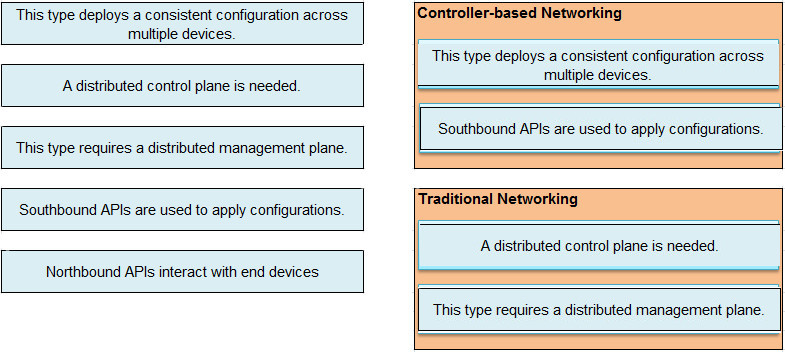
Drag and Drop Question Drag and drop the statement about networking from the left into the Corresponding networking types on the right. Not all statements are used.
Question 499
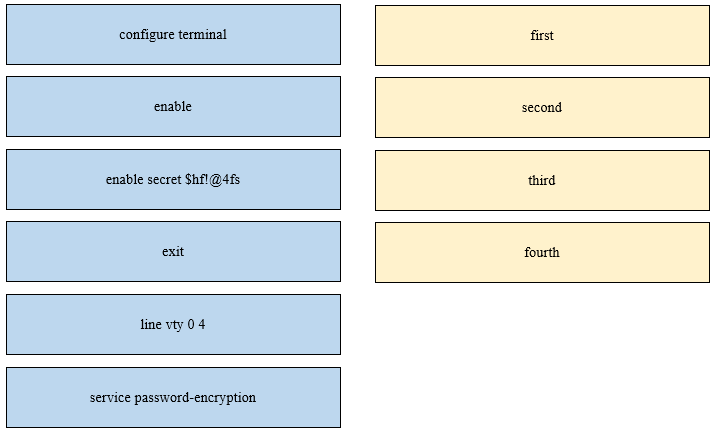
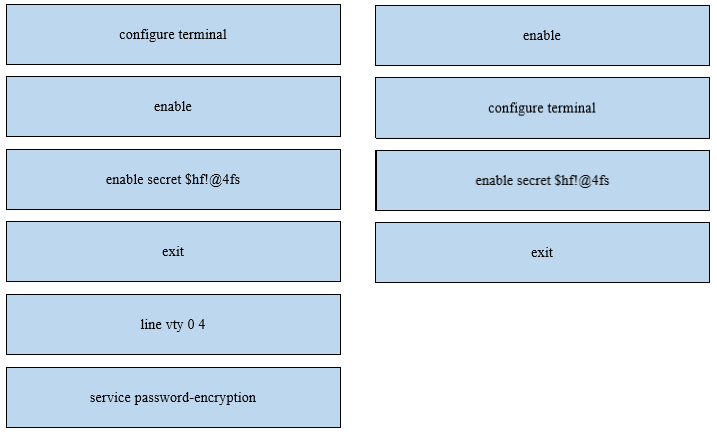
DRAG DROP - An engineer is configuring an encrypted password for the enable command on a router where the local user database has already been configured. Drag and drop the configuration commands from the left into the correct sequence on the right. Not all commands are used. Select and Place:
Question 500
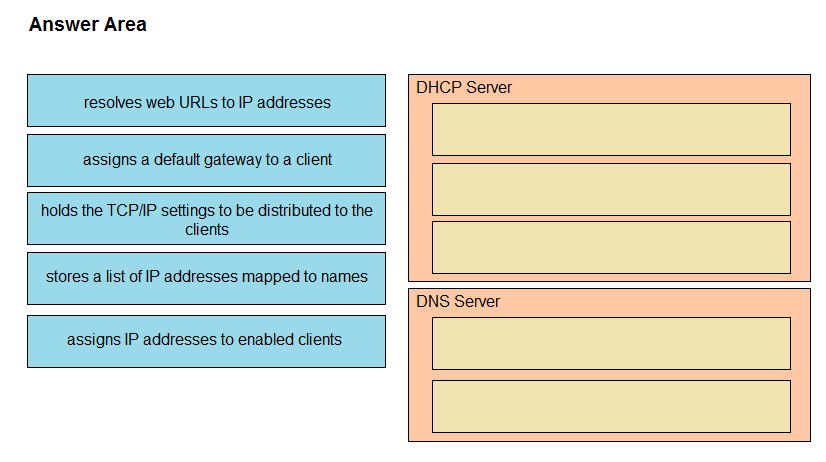
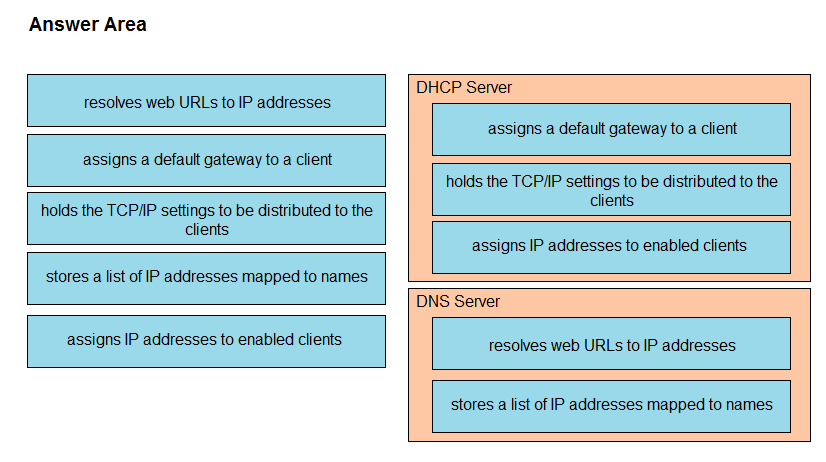
DRAG DROP - Drag and drop the functions from the left onto the correct network components on the right. Select and Place: