Question 461
Drag and drop the TCP/IP protocols from the left onto their primary transmission protocols on the right. Select and Place:
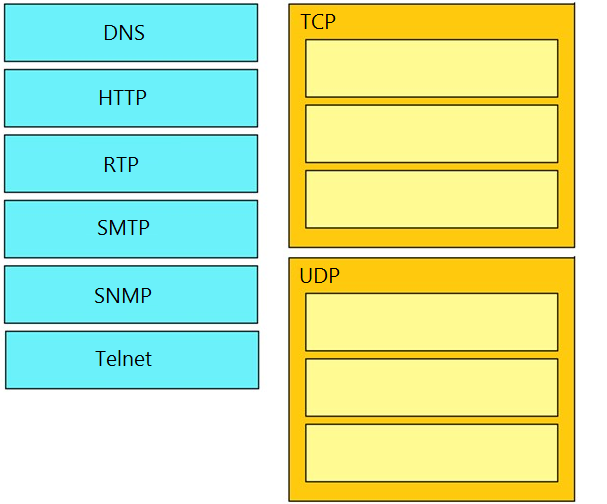
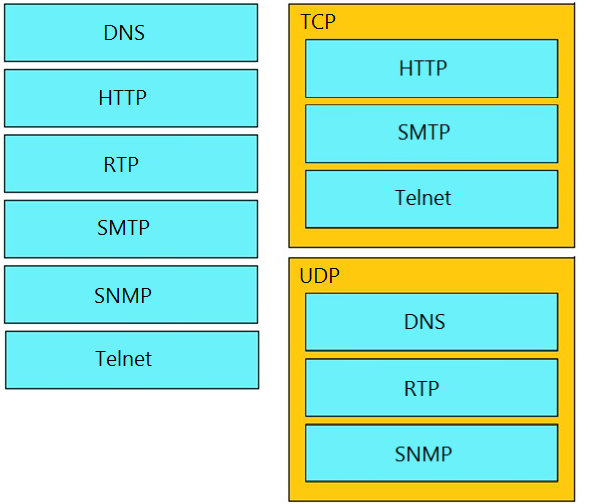
Question 462
An engineer must configure the IPv6 address 2001:0db8:0000:0000:0700:0003:400F:572B on the serial0/0 interface of the HQ router and wants to compress it for easier configuration. Which command must be issued on the router interface?
A. ipv6 address 2001:db8::700:3:400F:572B
B. ipv6 address 2001:db8:0::700:3:4F:572B
C. ipv6 address 2001:Odb8::7:3:4F:572B
D. ipv6 address 2001::db8:0000::700:3:400F:572B
Question 463
What describes the operation of virtual machines?
A. Virtual machines are responsible for managing and allocating host hardware resources
B. In a virtual machine environment, physical servers must run one operating system at a time.
C. Virtual machines are the physical hardware that support a virtual environment.
D. Virtual machines are operating system instances that are decoupled from server hardware
Question 464
Which WLC port connects to a switch to pass normal access-point traffic?
A. redundancy
B. console
C. distribution system
D. service
Question 465
An engineering team asks an implementer to configure syslog for warning conditions and error conditions.
Which command does the implementer configure to achieve the desired result?
A. logging trap 5
B. logging trap 2
C. logging trap 4
D. logging trap 3
Question 466
Drag and Drop Question Drag and drop the 802.11 wireless standards from the left onto the matching statements on the right.
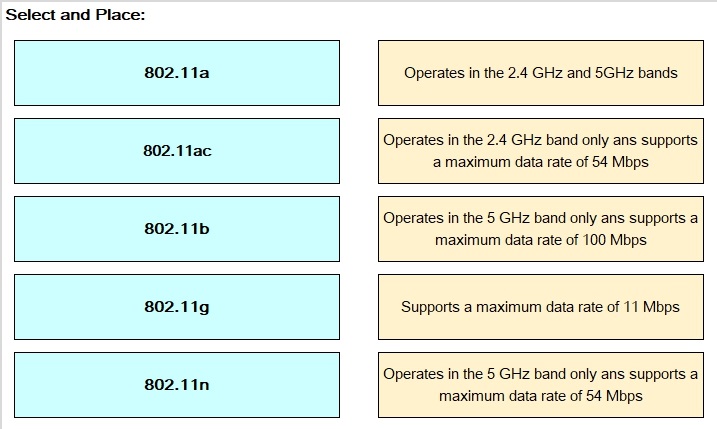
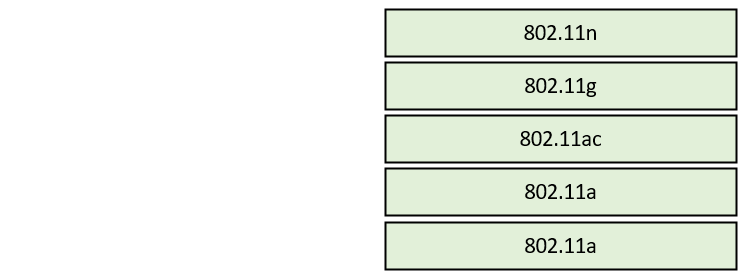
Question 467
What is the purpose of using First Hop Redundancy Protocol in a specific subnet?
A. Filter traffic based on destination IP addressing
B. Sends the default route to the hosts on a network
C. ensures a loop-free physical topology
D. forwards multicast hello messages between routers
Question 468
What must be considered when using 802:11 ta?
A. It is compatible with 802 lib- and 802 11-compliant wireless devices
B. It is used in place of 802 11b/g when many nonoverlapping channels are required
C. It is susceptible to interference from 2 4 GHz devices such as microwave ovens.
D. It is chosen over 802 11b/g when a lower-cost solution is necessary
Question 469
When a site-to-site VPN is configured, which IPsec mode provides encapsulation and encryption of the entire original P packet?
A. IPsec tunnel mode with AH
B. IPsec transport mode with AH
C. IPsec tunnel mode with ESP
D. IPsec transport mode with ESP
Question 470
What does physical access control regulate?
A. access to spec fie networks based on business function
B. access to servers to prevent malicious activity
C. access :o computer networks and file systems
D. access to networking equipment and facilities



