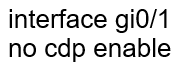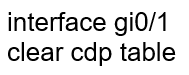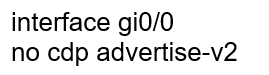Question 451
Which JSON data type is an unordered set of attribute- value pairs?
A. array
B. string
C. object
D. Boolean
Question 452
What is the benefit of using FHRP?
A. reduced management overhead on network routers
B. balancing traffic across multiple gateways in proportion to their loads
C. higher degree of availability
D. reduced ARP traffic on the network
Question 453
Which two QoS tools provides congestion management? ( Choose two )
A. CAR
B. CBWFQ
C. PQ
D. PBR
E. FRTS
Question 454
A network administrator must to configure SSH for remote access to router R1 The requirement is to use a public and private key pair to encrypt management traffic to and from the connecting client. Which configuration, when applied, meets the requirements?
A. R1#enable R1#configure terminal R1(config)#ip domain-name cisco.com R1(config)#crypto key generate ec keysize 1024
B. R1#enable R1#configure terminal R1(config)#ip domain-name cisco.com R1(config)#crypto key generate ec keysize 2048
C. R1#enable R1#configure terminal R1(config)#ip domain-name cisco.com R1(config)#crypto key encrypt rsa name myKey
D. R1#enable R1#configure terminal R1(config)#ip domain-name cisco.com R1(config)#crypto key generate rsa modulus 1024
Question 455
When deploying syslog, which severity level logs informational message?
A. 0
B. 2
C. 4
D. 6
Question 456
What are two improvements provided by automation for network management in an SDN environment? (Choose two)
A. Data collection and analysis tools establish a baseline for the network
B. Artificial intelligence identifies and prevents potential design failures.
C. Machine learning minimizes the overall error rate when automating troubleshooting processes
D. New devices are onboarded with minimal effort
E. Proprietary Cisco APIs leverage multiple network management tools.
Question 457
Which technology allows for multiple operating systems to be run on a single host computer?
A. virtual routing and forwarding
B. network port ID v sualization
C. virtual device on exts
D. server visualization
Question 458
What occurs when overlapping Wi-Fi channels are implemented?
A. The wireless network becomes vulnerable to unauthorized access.
B. Wireless devices are unable to distinguish between different SSIDs
C. Users experience poor wireless network performance.
D. Network communications are open to eavesdropping.
Question 459
Refer to the exhibit. An administrator must turn off the Cisco Discovery Protocol on the port configured with address last usable address in the 10.0.0.0/30 subnet. Which command set meets the requirement?
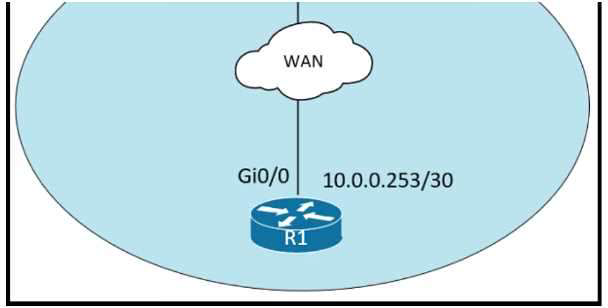
A.
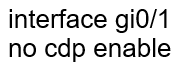
B.
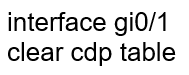
C.
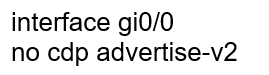
D.

Question 460
Which 802.11 management frame type is sent when a client roams between access points on the same SSID?
A. Reassociation Request
B. Probe Request
C. Authentication Request
D. Association Request