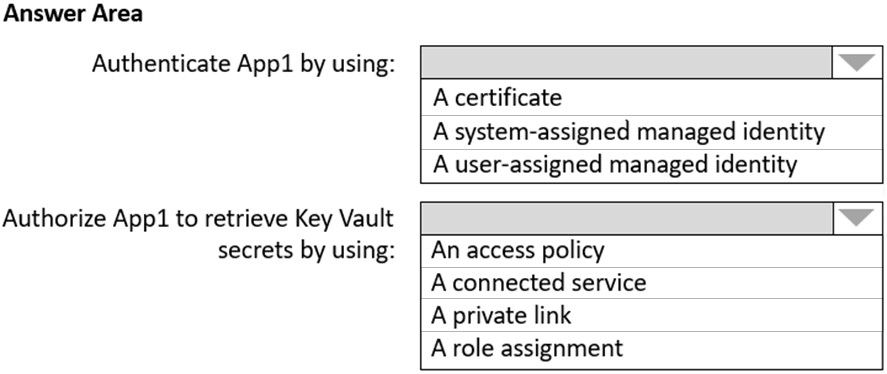
Scenario: Security Requirement -
All secrets used by Azure services must be stored in Azure Key Vault.
Services that require credentials must have the credentials tied to the service instance. The credentials must NOT be shared between services.
Box 1: A system-assigned managed identity
No one knows the credentials of managed identities.
Managed Identities exist in two formats:
* System assigned: in this scenario, the identity is linked to a single Azure Resource, eg a Virtual Machine, a Logic App, a Storage Account, Web App, Function,... so almost anything. Next, they also "live" with the Azure Resource, which means they get deleted when the Azure Resource gets deleted.
* User Assigned Managed Identity (incorrect for this question), which means that you first have to create it as a stand-alone Azure resource by itself, after which it can be linked to multiple Azure Resources.
Box 2: An access policy -
Set up an access policy for the system-assigned managed identity.
Note: Grant access -
The managed identity needs to be granted access to read the secret that we'll store in the Key Vault.
1. Navigate to your newly created Key Vault
2. Select Access Policy from the menu on the left side.
3. Select Add Access Policy
4. Etc.
Reference:
https://devblogs.microsoft.com/devops/demystifying-service-principals-managed-identities/
https://docs.microsoft.com/en-us/azure/active-directory/managed-identities-azure-resources/tutorial-windows-vm-access-nonaad