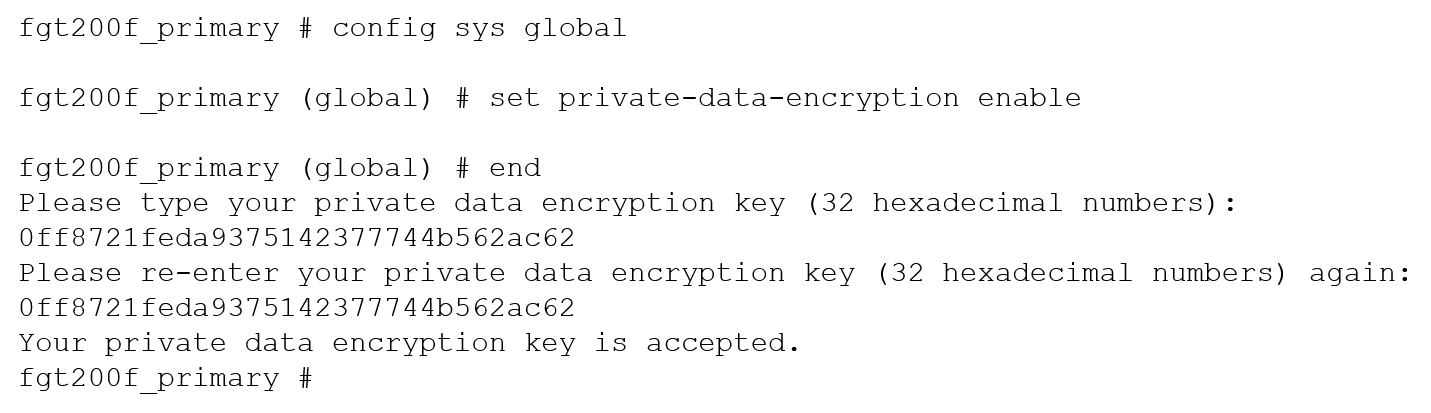
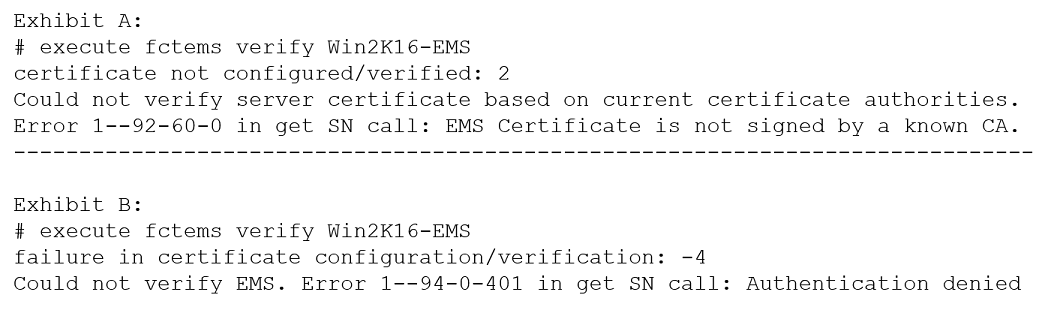
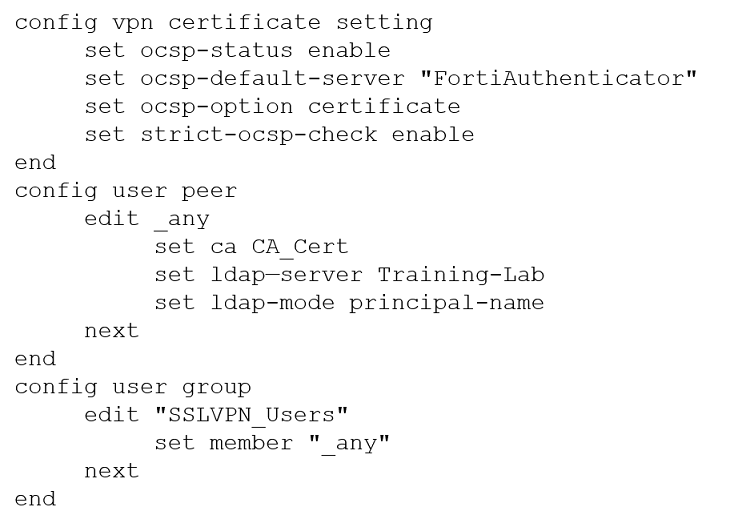
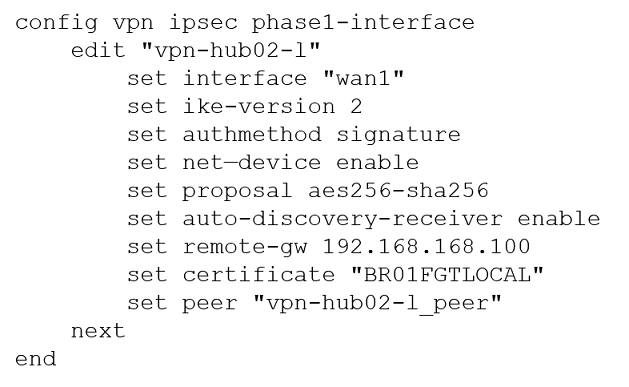
A customer with a FortiDDoS 200F protecting their fibre optic internet connection from incoming traffic sees that all the traffic was dropped by the device even though they were not under a DoS attack. The traffic flow was restored after it was rebooted using the GUI.
Which two options will prevent this situation in the future? (Choose two.)
A. Change the Adaptive Mode.
B. Create an HA setup with a second FortiDDoS 200F.
C. Move the internet connection from the SFP interfaces to the LC interfaces.
D. Replace with a FortiDDoS 1500F.