Question 21
Refer to the exhibits.
A customer wants to deploy 12 FortiAP 431F devices on high density conference center, but they do not currently have any PoE switches to connect them to. They want to be able to run them at full power while having network redundancy.
From the FortiSwitch models and sample retail prices shown in the exhibit, which build of materials would have the lowest cost, while fulfilling the customer’s requirements?
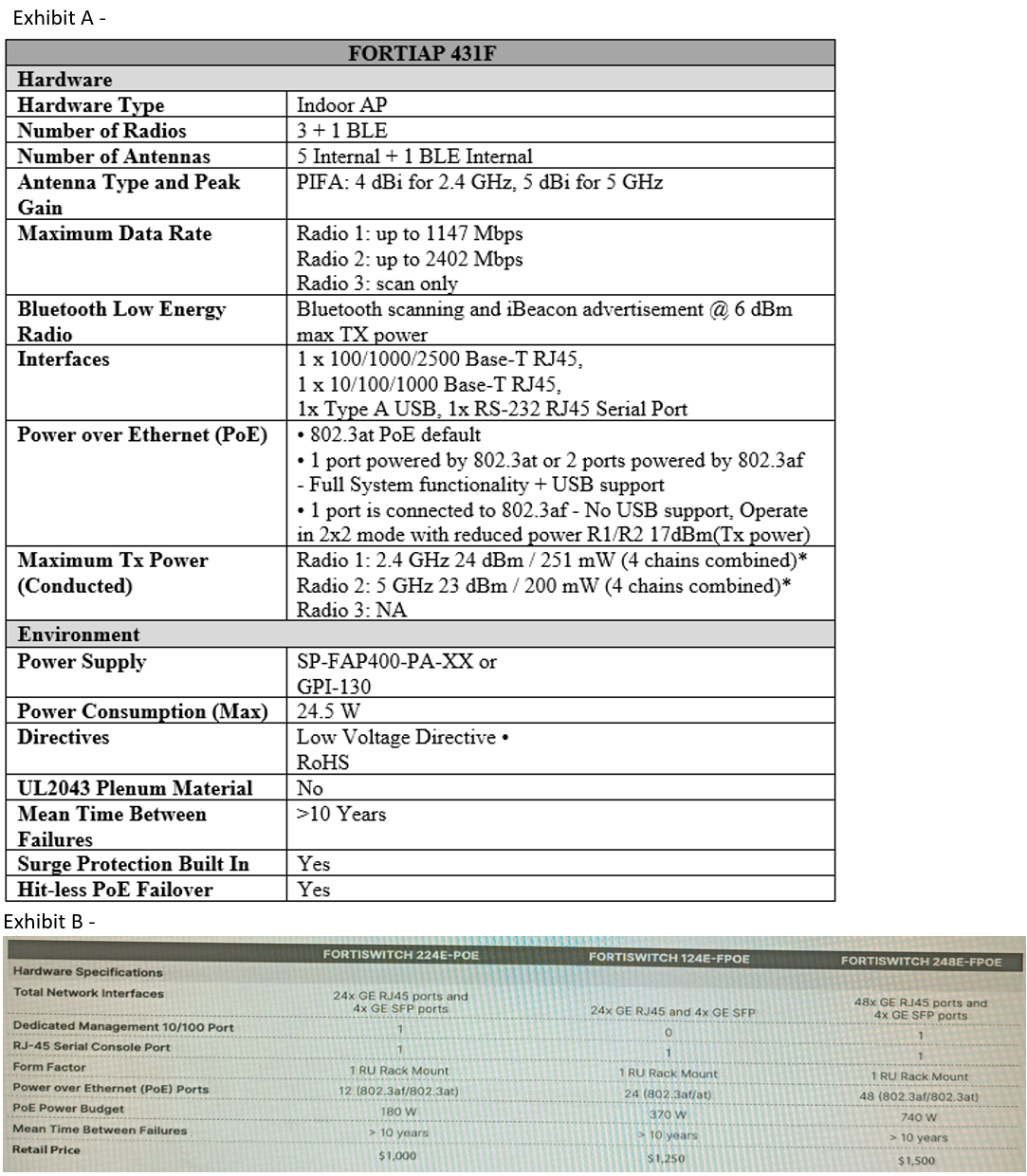
A. 1x FortiSwitch 248E-FPOE
B. 2x FortiSwitch 224E-POE
C. 2x FortiSwitch 248E-FPOE
D. 2x FortiSwitch 124E-FPOE
Question 22
Refer to the exhibits.
A customer is looking for a solution to authenticate the clients connected to a hardware switch interface of a FortiGate 400E.
Referring to the exhibits, which two conditions allow authentication to the client devices before assigning an IP address? (Choose two.)
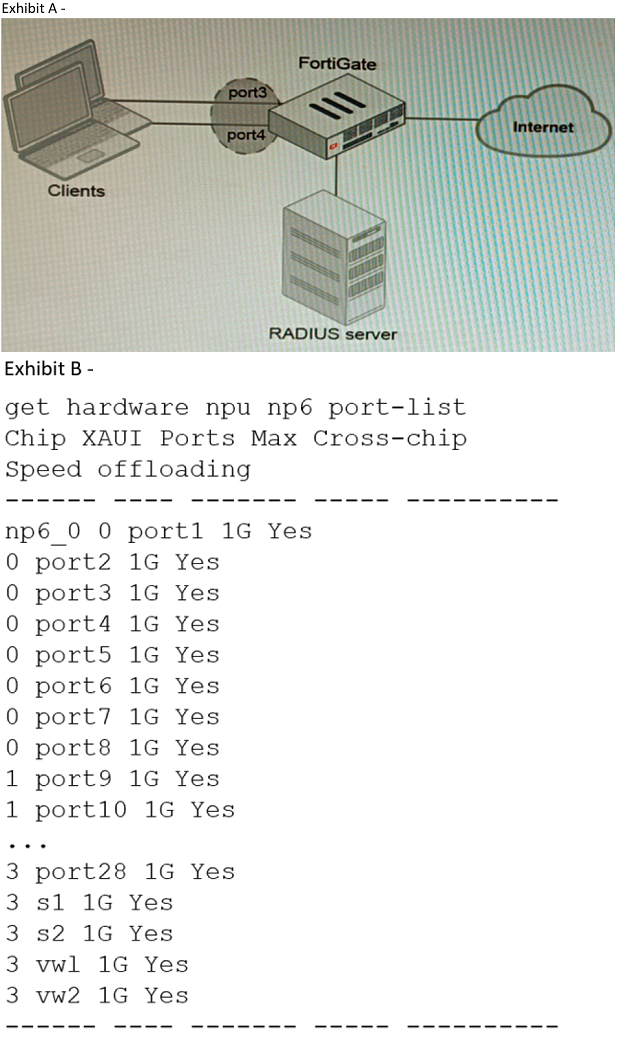
A. FortiGate devices with NP6 and hardware switch interfaces cannot support 802.1X authentication
B. Devices connected directly to ports 3 and 4 can perform 802.1X authentication
C. Ports 3 and 4 can be part of different switch interfaces
D. Client devices must have 802.1X authentication enabled
Question 23
You want to use the MTA adapter feature on FortiSandbox in an HA-Cluster.
Which statement about this solution is true?
A. The configuration of the MTA Adapter Local Interface is different than on port1
B. The MTA adapter is only available in the primary node
C. The MTA adapter mode is only detection mode
D. The configuration is different than on a standalone device
Question 24
Refer to the exhibit showing the history logs from a FortiMail device.
Which FortiMail email security feature can an administrator enable to treat these emails as spam?
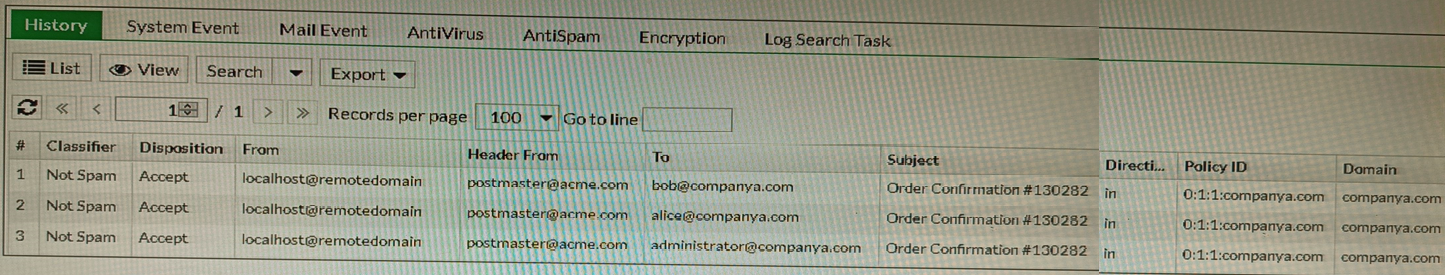
A. DKIM validation in a session profile
B. Sender domain validation in a session profile
C. Impersonation analysis in an antispam profile
D. Soft fail SPF validation in an antispam profile
Question 25
Refer to the exhibits, which show a firewall policy configuration and a network topology.
Configuration -Topology -An administrator has configured an inbound SSL inspection profile on a FortiGate device (FG-1) that is protecting a data center hosting multiple web pages.
Given the scenario shown in the exhibits, which certificate will FortiGate use to handle requests to xyz.
com?
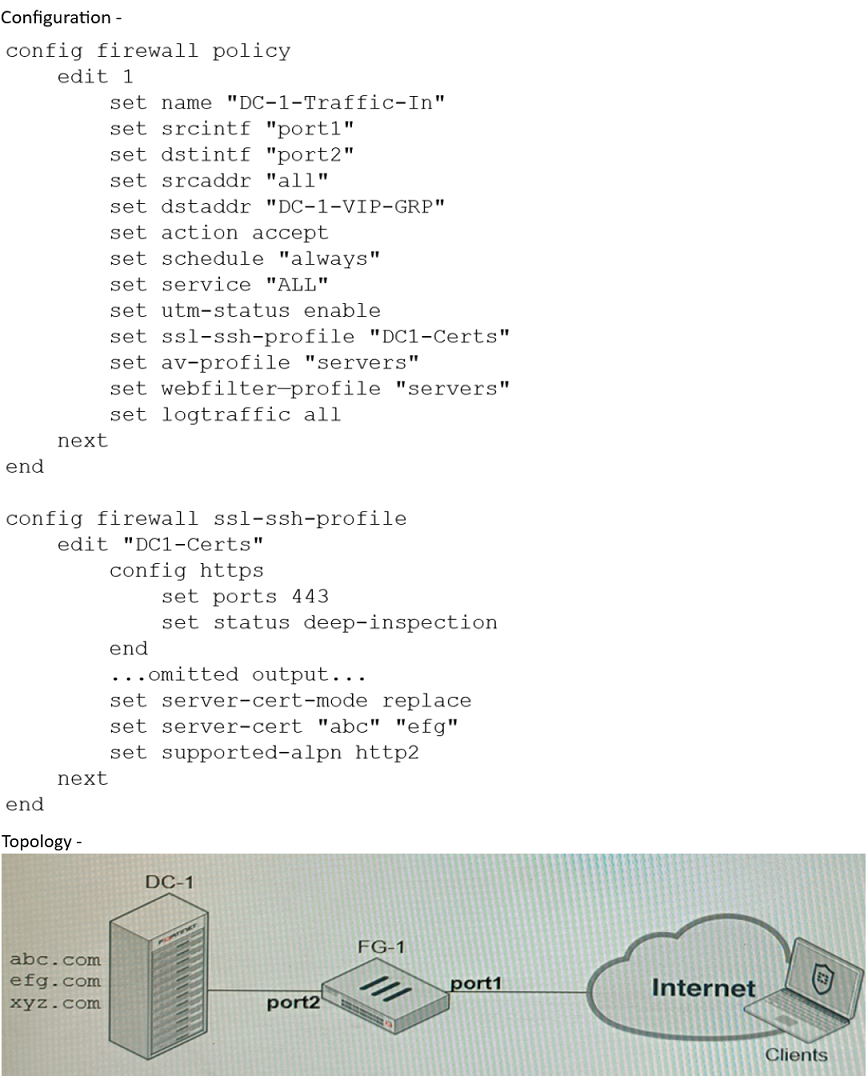
A. FortiGate will fall-back to the default Fortinet_CA_SSL certificate
B. FortiGate will reject the connection since no certificate is defined
C. FortiGate will use the Fortmet_CA_Untrusted certificate for the untrusted connection
D. FortiGate will use the first certificate in the server-cert list—the abc.com certificate
Question 26
Refer to the exhibits.
Configuration -Topology -A FortiGate cluster (CL-1) protects a data center hosting multiple web applications. A pair of FortiADC devices are already configured for SSL decryption (FAD-1), and re-encryption (FAD-2). CL-1 must accept unencrypted traffic from FAD-1, perform application detection on the plain-text traffic, and forward the inspected traffic to FAD-2.
The SSL-Offload-App-Detect application list and SSL-Offload protocol options profile are applied to the firewall policy handling the web application traffic on CL-1.
Given this scenario, which two configuration tasks must the administrator perform on CL-1? (Choose two.)
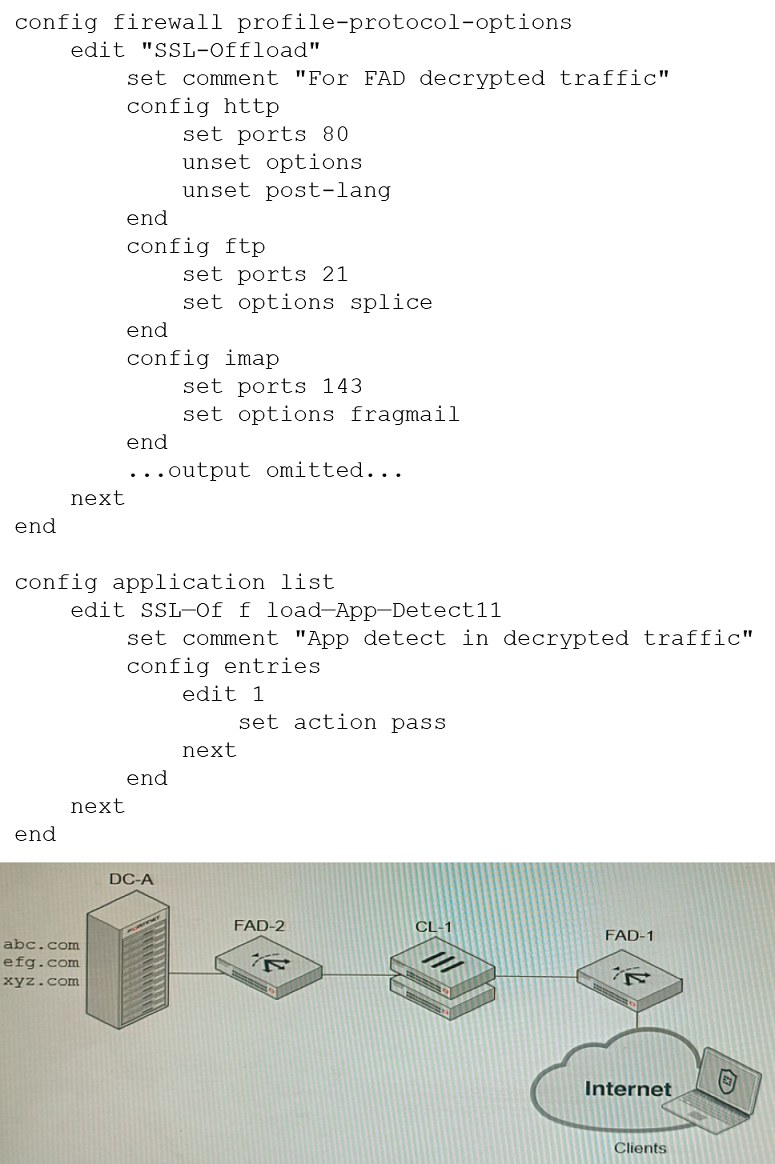
A.
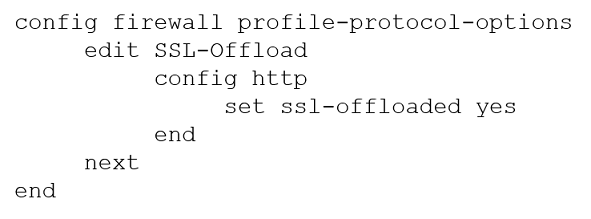
B.
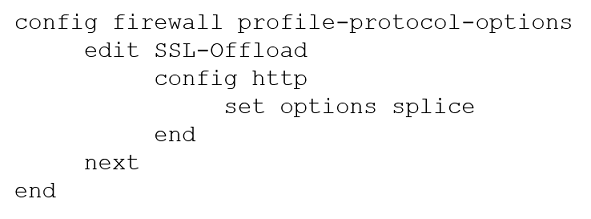
C.
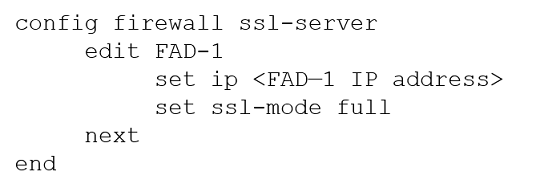
D.

E.

Question 27
You are migrating the branches of a customer to FortiGate devices. They require independent routing tables on the LAN side of the network.
After reviewing the design, you notice the firewall will have many BGP sessions as you have two data centers (DC) and two ISPs per DC while each branch is using at least 10 internal segments.
Based on this scenario, what would you suggest as the more efficient solution, considering that in the future the number of internal segments, DCs or internet links per DC will increase?
A. No change in design is needed as even small FortiGate devices have a large memory capacity
B. Acquire a FortiGate model with more capacity, considering the next 5 years growth
C. Implement network-id, neighbor-group and increase the advertisement-interval
D. Redesign the SD-WAN deployment to only use a single VPN tunnel and segment traffic using VRFs on BGP
Question 28
You must analyze an event that happened at 20:
37 UTC.
One log relevant to the event is extracted from FortiGate logs:
The devices and the administrator are all located in different time zones Daylight savings time (DST) is disabled.
The FortiGate is at GMT-10:
00 -The FortiAnalyzer is at GMT-08:
00Your browser local time zone is at GMT-03:
00You want to review this log on FortiAnalyzer GUI, what time should you use as a filter?
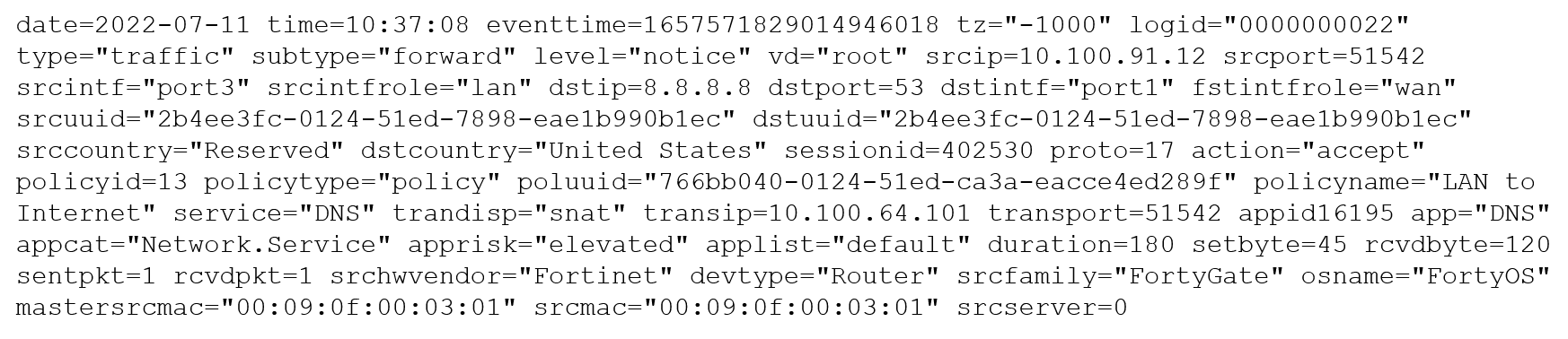
A. 20:37:08
B. 10:37:08
C. 17:37:08
D. 12:37:08
Question 29
A customer is planning on moving their secondary data center to a cloud-based IaaS. They want to place all the Oracle-based systems on Oracle Cloud, while the other systems will be on Microsoft Azure with ExpressRoute service to their main data center.
They have about 200 branches with two internet services as their only WAN connections. As a security consultant you are asked to design an architecture using Fortinet products with security, redundancy, and performance as a priority.
Which two design options are true based on these requirements? (Choose two.)
A. Systems running on Azure will need to go through the main data center to access the services on Oracle Cloud.
B. Use FortiGate VM for IPSEC over ExpressRoute, as traffic is not encrypted by Azure.
C. Branch FortiGate devices must be configured as VPN clients for the branches’ internal network to be able to access Oracle services without using public IPs.
D. Two ExpressRoute services to the main data center are required to implement SD-WAN between a FortiGate VM in Azure and a FortiGate device at the data center edge.
Question 30
Refer to the exhibit, which shows the high availability configuration for the FortiAuthenticator (FAC1).
Based on this information, which statement is true about the next FortiAuthenticator (FAC2) member that will join an HA cluster with this FortiAuthenticator (FAC1)?
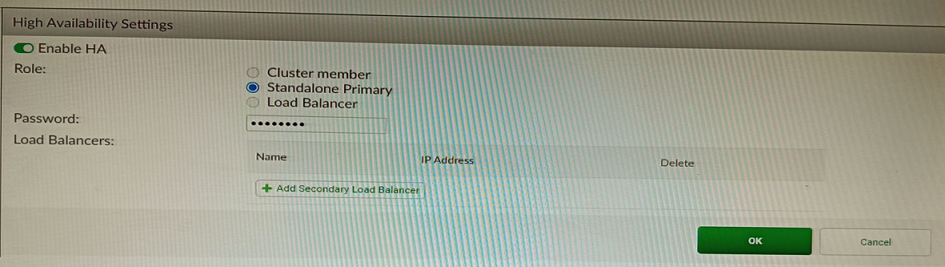
A. FAC2 can only process requests when FAC1 fails.
B. FAC2 can have its HA interface on a different network than FAC1
C. The FortiToken license will need to be installed on the FAC2
D. FSSO sessions from FAC1 will be synchronized to FAC2











