Question 51
Which statement describes a characteristic of automation stitches?
A. They can have one or more triggers.
B. They can be run only on devices in the Security Fabric.
C. They can run multiple actions simultaneously.
D. They can be created on any device in the fabric.
Question 52
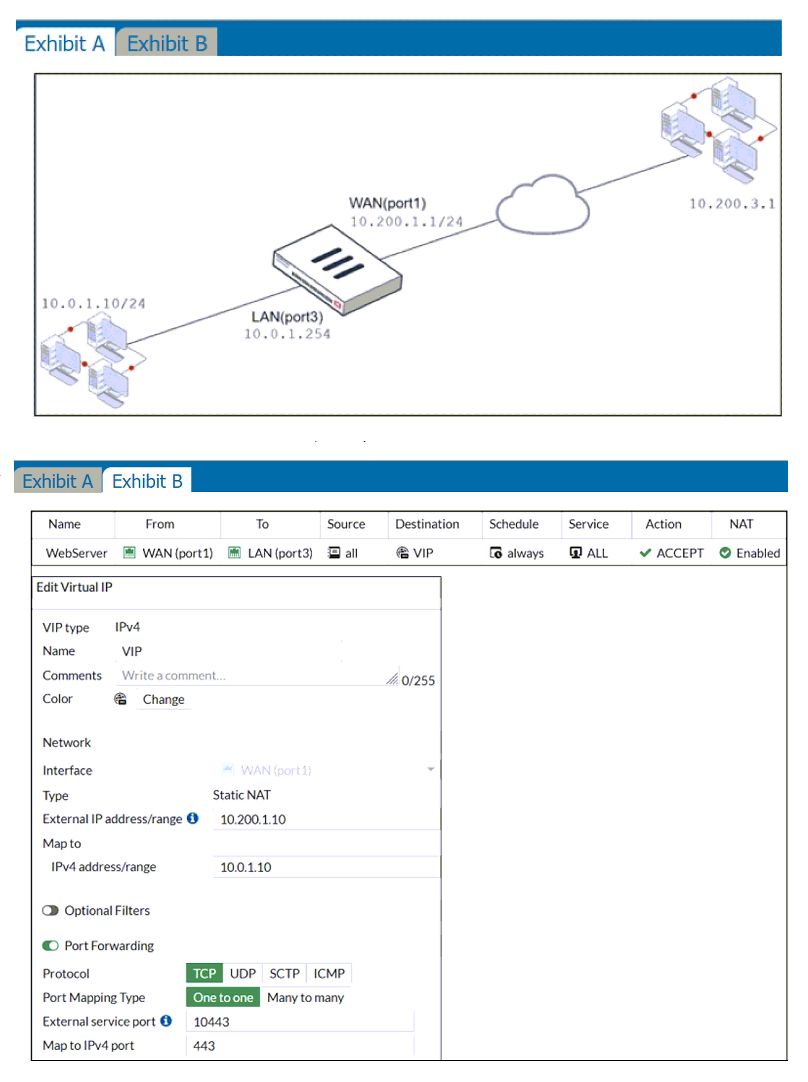
Refer to the exhibits.
Exhibit A shows a network diagram. Exhibit B shows the firewall policy configuration and a VIP object configuration.
The WAN (port1) interface has the IP address 10.200.1.1/24.
The LAN (port3) interface has the IP address 10.0.1.254/24.
If the host 10.200.3.1 sends a TCP SYN packet on port 10443 to 10.200.1.10, what will the source address, destination address, and destination port of the packet be, after FortiGate forwards the packet to the destination?
A. 10.0.1.254, 10.0.1.10, and 443, respectively
B. 10.0.1.254, 10.0.1.10, and 10443, respectively
C. 10.200.3.1, 10.0.1.10, and 443, respectively
Question 53
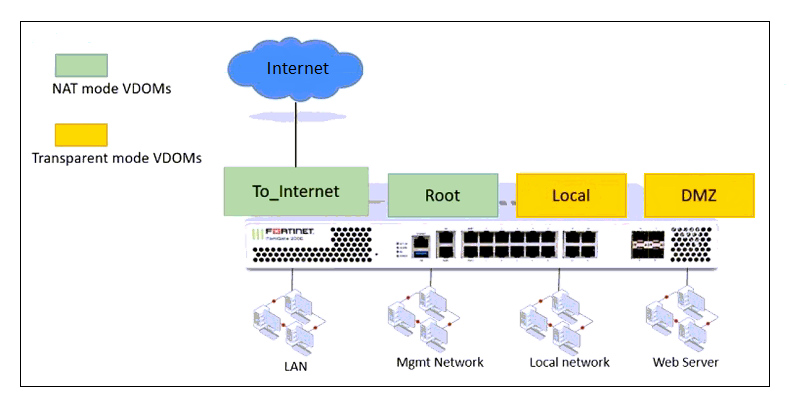
Refer to the exhibit.
The Root and To_Internet VDOMs are configured in NAT mode. The DMZ and Local VDOMs are configured in transparent mode.
The Root VDOM is the management VDOM. The To_Internet VDOM allows LAN users to access the internet. The To_Internet VDOM is the only VDOM with internet access and is directly connected to the ISP modem.
What can you conclude about this configuration?
A. Inter-VDOM links are not required between the Root and To_Internet VDOMs because the Root VDOM is used only as a management VDOM.
B. A default static route is not required on the To_Internet VDOM to allow LAN users to access the internet.
C. Inter-VDOM links are required to allow traffic between the Local and DMZ VDOMs.
D. Inter-VDOM links are required to allow traffic between the Local and Root VDOMs.
Question 54
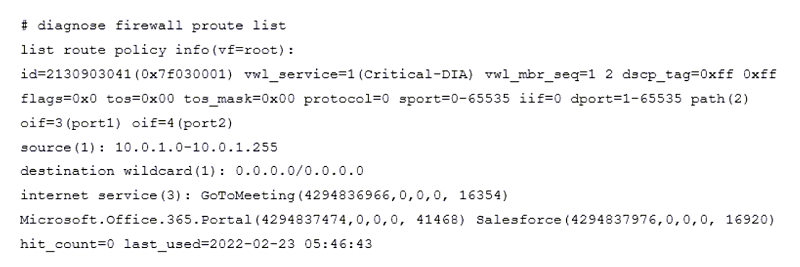
Refer to the exhibit.
The exhibit shows the output of a diagnose command.
What does the output reveal about the policy route?
A. It is an ISDB route in policy route.
B. It is a regular policy route.
C. It is an ISDB policy route with an SDWAN rule.
D. It is an SDWAN rule in policy route.
Question 55
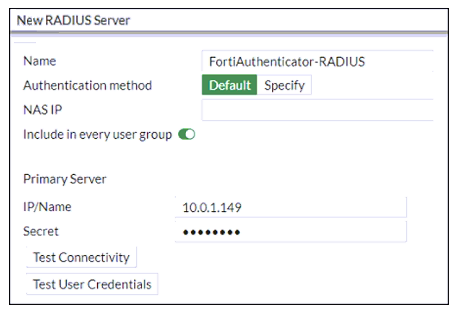
Refer to the exhibit.
An administrator added a configuration for a new RADIUS server. While configuring, the administrator selected the Include in every user group option.
What is the impact of using the Include in every user group option in a RADIUS configuration?
A. This option places all users into every RADIUS user group, including groups that are used for the LDAP server on FortiGate.
B. This option places the RADIUS server, and all users who can authenticate against that server, into every FortiGate user group.
C. This option places all FortiGate users and groups required to authenticate into the RADIUS server, which, in this case, is FortiAuthenticator.
D. This option places the RADIUS server, and all users who can authenticate against that server, into every RADIUS group.
Question 56
Refer to the exhibit.
A network administrator is troubleshooting an IPsec tunnel between two FortiGate devices. The administrator has determined that phase 1 status is up, but phase 2 fails to come up.
Based on the phase 2 configuration shown in the exhibit, which configuration change will bring phase 2 up?
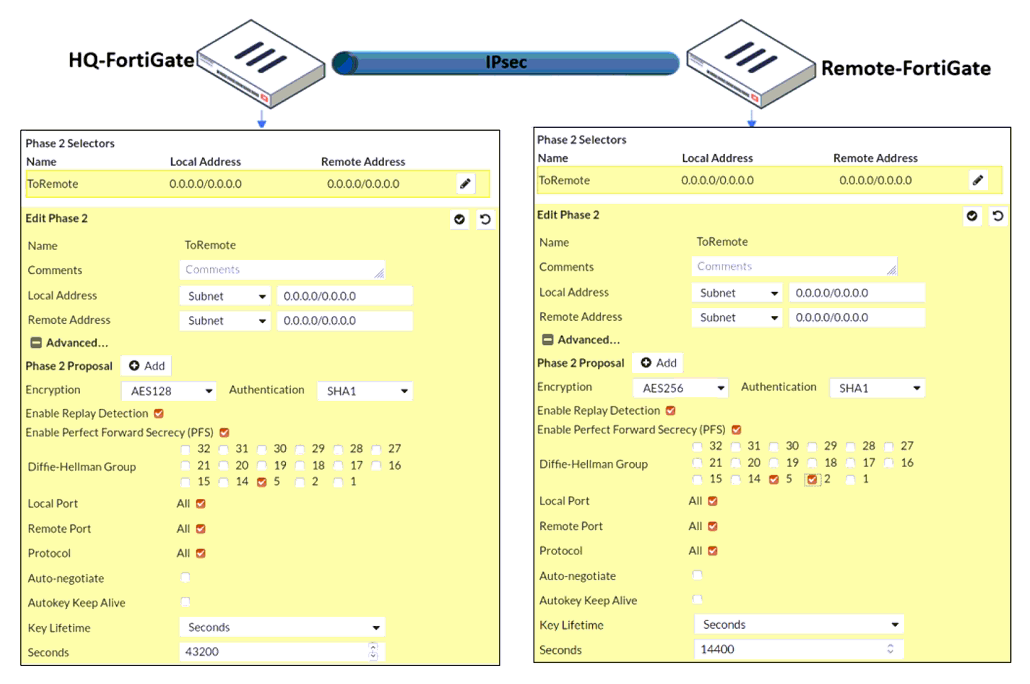
A. On Remote-FortiGate, set Seconds to 43200.
B. On HQ-FortiGate, set Encryption to AES256.
C. On HQ-FortiGate, enable Diffie-Hellman Group 2.
D. On HQ-FortiGate, enable Auto-negotiate.
Question 57
An administrator configures FortiGuard servers as DNS servers on FortiGate using default settings.
What is true about the DNS connection to a FortiGuard server?
A. It uses UDP 8888.
B. It uses UDP 53.
C. It uses DNS over HTTPS.
D. It uses DNS over TLS.
Question 58
Refer to the exhibit.
The exhibit shows the IPS sensor configuration.
If traffic matches this IPS sensor, which two actions is the sensor expected to take? (Choose two.)
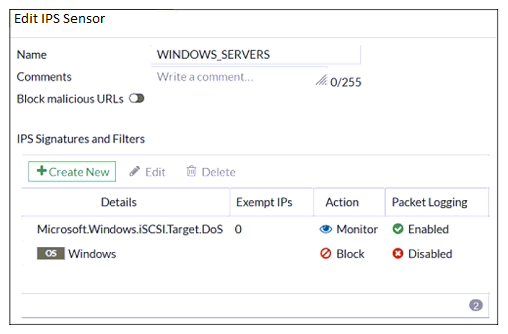
A. The sensor will gather a packet log for all matched traffic.
B. The sensor will reset all connections that match these signatures.
C. The sensor will block all attacks aimed at Windows servers.
D. The sensor will allow attackers matching the Microsoft Windows.iSCSI.Target.DoS signature.
Question 59
Which two types of traffic are managed only by the management VDOM? (Choose two.)
A. DNS
B. FortiGuard web filter queries
C. PKi
D. Traffic shaping
Question 60
Refer to the exhibits.
The SSL VPN connection fails when a user attempts to connect to it.
What should the user do to successfully connect to the SSL VPN?
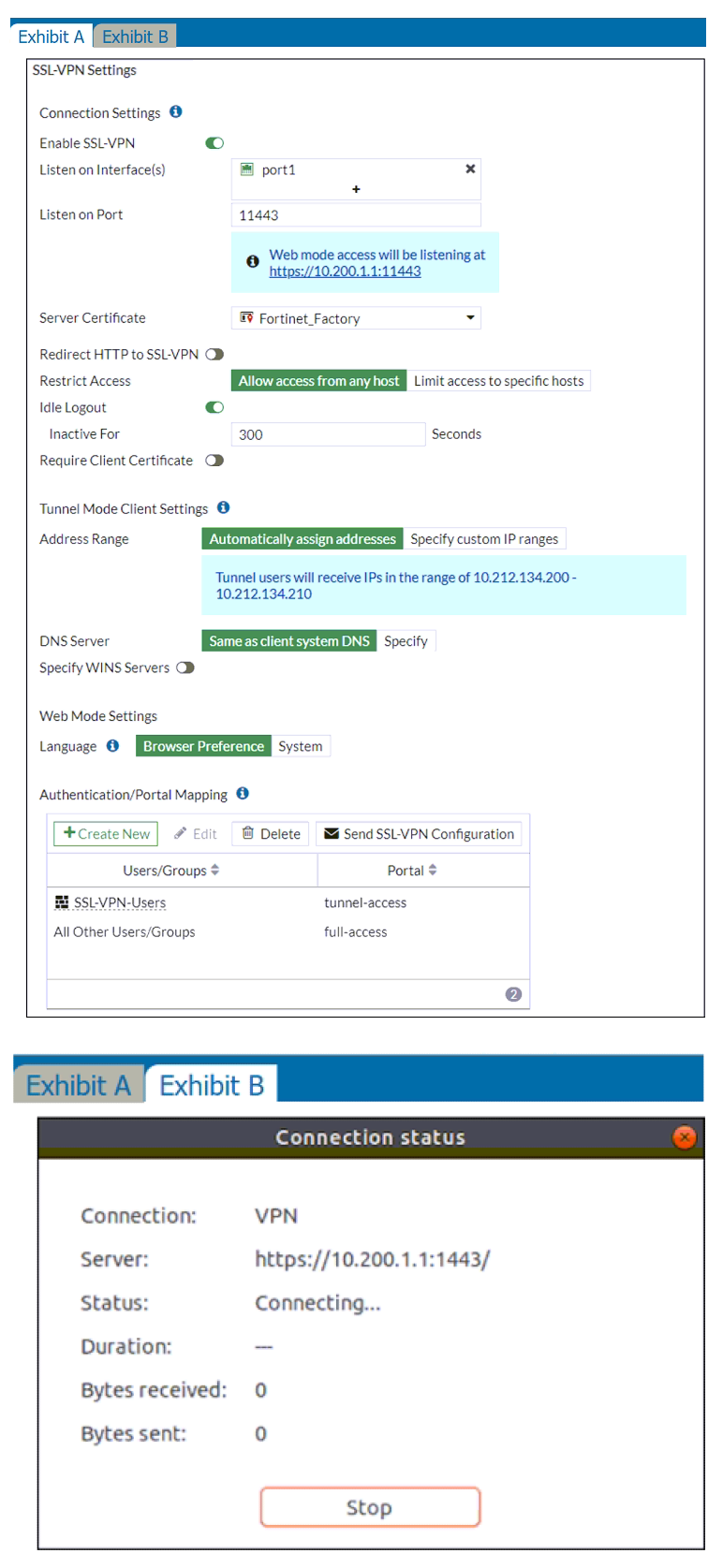
A. Change the SSL VPN port on the client.
B. Change the idle-timeout.
C. Change the SSL VPN portal to the tunnel.
D. Change the server IP address.






