Question 31
An administrator wants to configure dead peer detection (DPD) on IPsec VPN for detecting dead tunnels. The requirement is that FortiGate sends DPD probes only when no traffic is observed in the tunnel.
Which DPD mode on FortiGate will meet this requirement?
A. On Demand
B. On Idle
C. Disabled
D. Enabled
Question 32
An administrator does not want to report the login events of service accounts to FortiGate.
Which setting on the collector agent is required to achieve this?
A. Add user accounts to the Ignore User List.
B. Add user accounts to Active Directory (AD).
C. Add user accounts to the FortiGate group filter.
D. Add the support of NTLM authentication.
Question 33
Refer to the exhibit.
Based on the ZTNA tag, the security posture of the remote endpoint has changed.
What will happen to endpoint active ZTNA sessions?
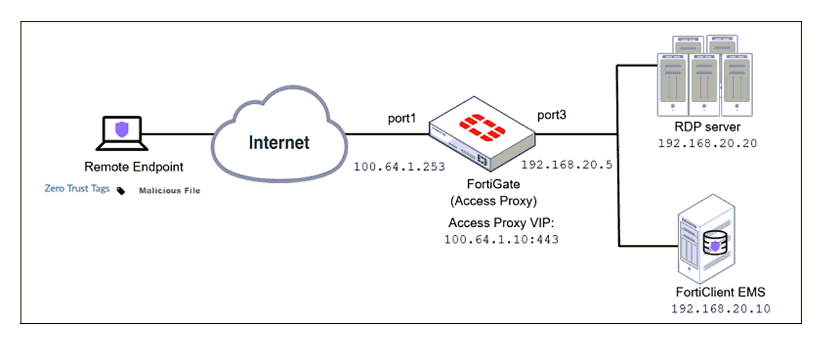
A. They will be re-evaluated to match the endpoint policy.
B. They will be re-evaluated to match the firewall policy.
C. They will be re-evaluated to match the ZTNA policy.
D. They will be re-evaluated to match the security policy.
Question 34
Refer to the exhibit.
The exhibit shows a diagram of a FortiGate device connected to the network and the firewall policy and IP pool configuration on the FortiGate device.
Which two actions does FortiGate take on internet traffic sourced from the subscribers? (Choose two.)
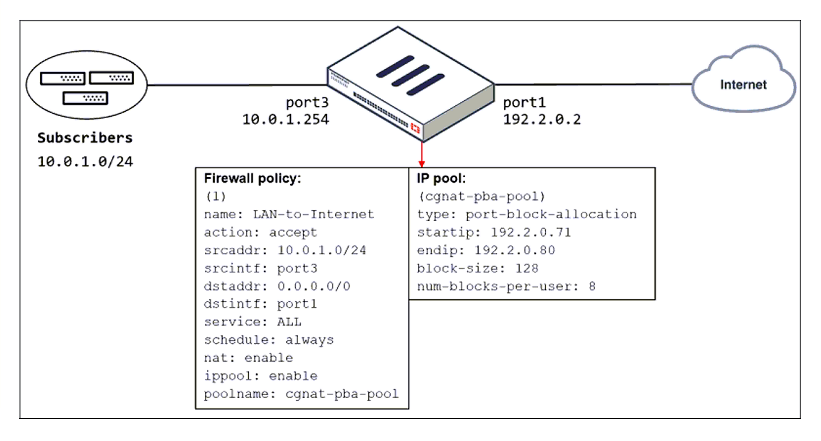
A. FortiGate allocates port blocks per user, based on the configured range of internal IP addresses.
B. FortiGate allocates port blocks on a first-come, first-served basis.
C. FortiGate generates a system event log for every port block allocation made per user.
D. FortiGate allocates 128 port blocks per user.
Question 35
Which two statements about the Security Fabric rating are true? (Choose two.)
A. It provides executive summaries of the four largest areas of security focus.
B. The Security Fabric rating is a free service that comes bundled with all FortiGate devices.
C. Many of the security issues can be fixed immediately by clicking Apply where available.
D. The Security Fabric rating must be run on the root FortiGate device in the Security Fabric.
Question 36
An administrator wants to configure timeouts for users. Regardless of the user's behavior, the timer should start as soon as the user authenticates and expire after the configured value.
Which timeout option should the administrator configure on FortiGate?
A. new-session
B. idle-timeout
C. hard-timeout
D. soft-timeout
E. auth-on-demand
Question 37
Which two statements explain antivirus scanning modes? (Choose two.)
A. In flow-based inspection mode, files bigger than the buffer size are scanned.
B. In proxy-based inspection mode, files bigger than the buffer size are scanned.
C. In flow-based inspection mode, FortiGate buffers the file, but also simultaneously transmits it to the client.
D. In proxy-based inspection mode, antivirus scanning buffers the whole file for scanning, before sending it to the client.
Question 38
Refer to the exhibits.
The exhibits show a network diagram and firewall configurations.
An administrator created a Deny policy with default settings to deny Webserver access for Remote-User2. Remote-User1 must be able to access the Webserver. Remote-User2 must not be able to access the Webserver.
In this scenario, which two changes can the administrator make to deny Webserver access for Remote-User2? (Choose two.)
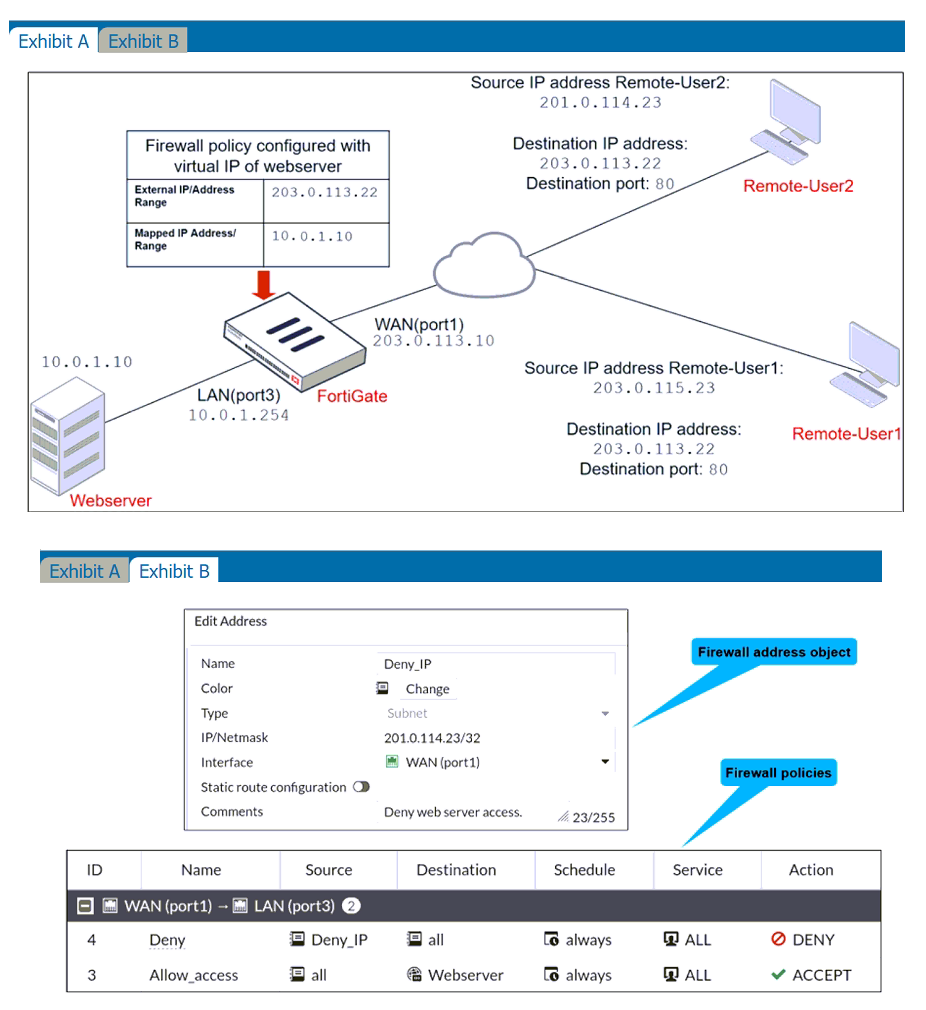
A. Disable match-vip in the Deny policy.
B. Set the Destination address as Webserver in the Deny policy.
C. Enable match-vip in the Deny policy.
D. Set the Destination address as Deny_IP in the Allow_access policy.
Question 39
Refer to the exhibit.
Examine the intrusion prevention system (IPS) diagnostic command shown in the exhibit.
If option 5 is used with the IPS diagnostic command and the outcome is a decrease in the CPU usage, what is the correct conclusion?
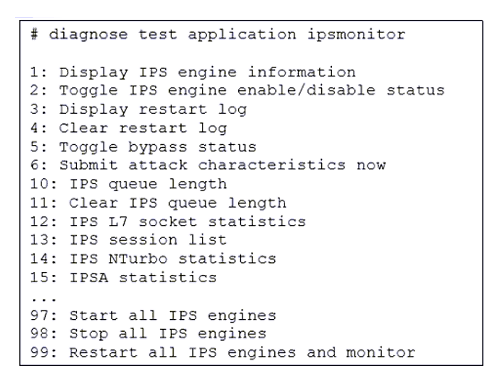
A. The IPS engine is unable to prevent an intrusion attack.
B. The IPS engine is inspecting a high volume of traffic.
C. The IPS engine will continue to run in a normal state.
D. The IPS engine is blocking all traffic.
Question 40
Which two protocols are used to enable administrator access of a FortiGate device? (Choose two.)
A. FTM
B. SSH
C. HTTPS
D. FortiTelemetry



