Question 451
Refer to the exhibit. An engineer attempts to create a configuration to allow the Blue VRF to leak into the global routing table, but the configuration does not function as expected
Which action resolves this issue?
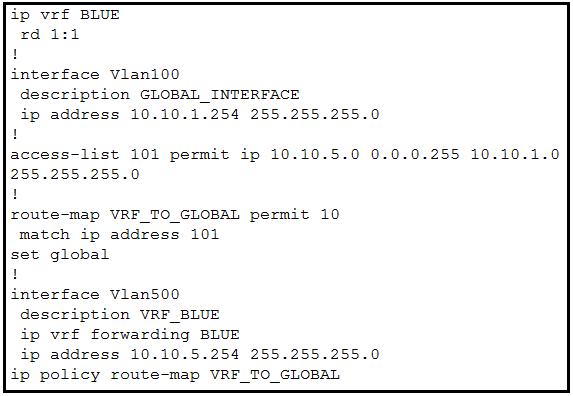
A. Change the source network that is specified in access-list 101.
B. Change the access-list destination mask to a wildcard.
C. Change the access-list number in the route map.
D. Change the route-map configuration to VRF_BLUE.
Question 452
An engineer must configure a multicast UDP jitter operation
Which configuration should be applied?
A. Router(config)#ip sla 1 Router(config)#udp-jitter 192.0.2.115 65051
B. Router(config)#ip sla 1 Router(config)#udp jitter 239.1.1.1 65051 end-point list List source-ip 192.168.1.1
C. Router(config)#ip sla 1 Router(config)#udp-jitter 192.0.2.115 65051 num-packets 20
D. Router(config)#ip sla 1 Router(config)#udp jitter 10.0.0.1 source-ip 192.168.1.1
Question 453
Refer to the exhibit. The network administrator must be able to perform configuration changes when all the RADIUS servers are unreachable
Which configuration allows all commands to be authorized if the user has successfully authenticated?

A. aaa authentication login default group radius local none
B. aaa authorization exec default group radius
C. aaa authorization exec default group radius if-authenticated
D. aaa authorization exec default group radius none
Question 454
In a Cisco SD-WAN solution, which two functions are performed by OMP? (Choose two.)
A. advertisement of network prefixes and their attributes
B. configuration of control and data policies
C. gathering of underlay infrastructure data
D. delivery of crypto keys
E. segmentation and differentiation of traffic
Question 455
How can an engineer prevent basic replay attacks from people who try to brute force a system via REST API?
A. Add a timestamp to the request in the API header.
B. Use a password hash.
C. Add OAuth to the request in the API header.
D. Use HTTPS.
Question 456
What are the main components of Cisco TrustSec?
A. Cisco ISE and Enterprise Directory Services
B. Cisco ISE, network switches, firewalls, and routers
C. Cisco ISE and TACACS+
D. Cisco ASA and Cisco Firepower Threat Defense
Question 457
What is a characteristic of a WLC that is in master controller mode?
A. Configuration on the master controller is executed on all wireless LAN controllers.
B. The master controller is responsible for load balancing all connecting clients to other controllers.
C. All new APs that join the WLAN are assigned to the master controller.
D. All wireless LAN controllers are managed by the master controller.
Question 458
Which Cisco FlexConnect state allows wireless users that are connected to the network to continue working after the connection to the WLC has been lost?
A. Authentication Down/Switching Down
B. Authentication-Central/Switch-Local
C. Authentication-Central/Switch-Central
D. Authentication-Down/Switch-Local
Question 459
Refer to the exhibit. Object tracking has been configured for VRRP-enabled routers Edge-01 and Edge-02
Which commands cause Edge-02 to preempt Edge-01 in the event that interface G0/0 goes down on Edge-01?

A. Edge-01(config)#interface G0/1 Edge-01(config-if)#vrrp 10 track 10 decrement 30
B. Edge-02(config)#interface G0/1 Edge-02(config-if)#vrrp 10 track 10 decrement 30
C. Edge-02(config)#interface G0/1 Edge-02(config-if)#vrrp 10 track 10 decrement 10
D. Edge-01(config)#interface G0/1 Edge-01(config-if)#vrrp 10 track 10 decrement 10
Question 460
Refer to the exhibit. An engineer must prevent the R6 loopback from getting into Area 2 and Area 3 from Area 0
Which action must the engineer take?
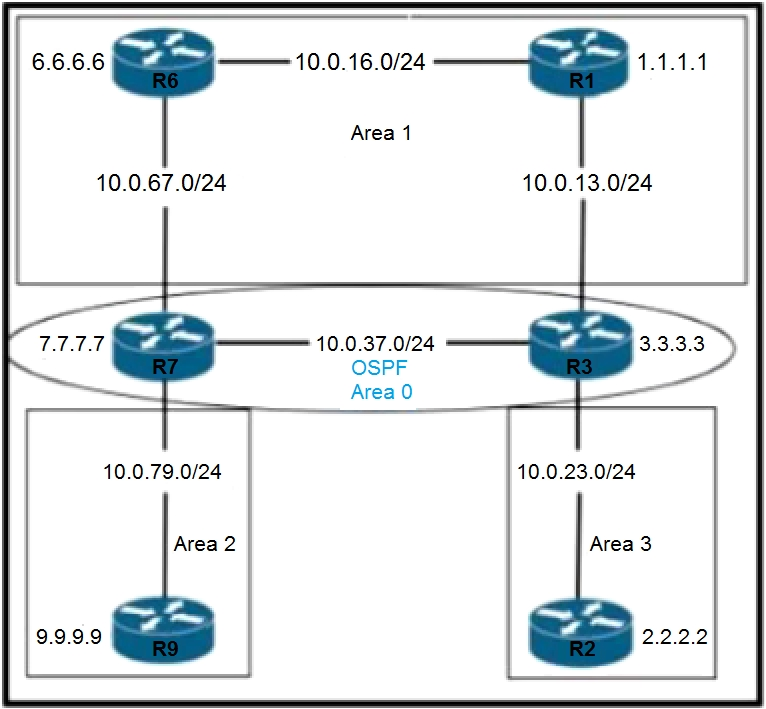
A. Apply a filter list outbound on R3 and R7.
B. Apply a filter list inbound on R2 and R9.
C. Apply a filter list inbound on R3 and R7.
D. Apply a filter list outbound on R7 only.



