Question 331
Refer to the exhibit. After running the code in the exhibit, which step reduces the amount of data that the NETCONF server returns to the NETCONF client, to only the interface's configuration?
A. Use the Ixml library to parse the data returned by the NETCONF server for the interface's configuration.
B. Create an XML filter as a string and pass it to get_config() method as an argument.
C. Create a JSON filter as a string and pass it to the get_config() method as an argument.
D. Use the JSON library to parse the data returned by the NETCONF server for the interface's configuration.
Question 332
Which method displays text directly into the active console with a synchronous EEM applet policy?
A. event manager applet boom event syslog pattern 'UP' action 1.0 syslog priority direct msg 'logging directly to console'
B. event manager applet boom event syslog pattern 'UP' action 1.0 gets 'logging directly to console'
C. event manager applet boom event syslog pattern 'UP' action 1.0 string 'logging directly to console'
D. event manager applet boom event syslog pattern 'UP' action 1.0 puts 'logging directly to console'
Question 333
Which line must be added in the Python function to return the JSON object {`cat_9k`: `FXS1932Q2SE`}?
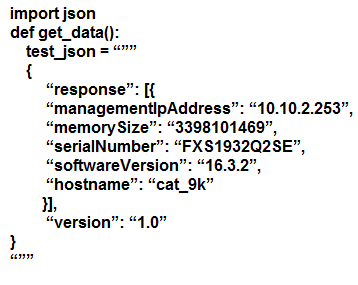
A. return (json.dumps({d['hostname']: d['serialNumber'] for d in json.loads(test_json)['response']}))
B. return (json.dumps({for d in json.loads(test_json)['response']: d['hostname']: d['serialNumber']}))
C. return (json.loads({d['hostname']: d['serialNumber'] for d in json.dumps(test_json)['response'}))
D. return (json.loads({for d in json.dumps(test_json)['response']: d['hostname']: d['serialNumber']}))
Question 334
Which two steps are required for a complete Cisco DNA Center upgrade? (Choose two.)
A. automation backup
B. system update
C. golden image selection
D. proxy configuration
E. application updates
Question 335
Which method creates an EEM applet policy that is registered with EEM and runs on demand or manually?
A. event manager applet ondemand event none action 1.0 syslog priority critical msg 'This is a message from ondemand'
B. event manager applet ondemand action 1.0 syslog priority critical msg 'This is a message from ondemand'
C. event manager applet ondemand event register action 1.0 syslog priority critical msg 'This is a message from ondemand'
D. event manager applet ondemand event manual action 1.0 syslog priority critical msg 'This is a message from ondemand'
Question 336
What does this EEM applet event accomplish?
"event snmp oid 1.3.6.1.3.7.6.5.3.9.3.8.7 get-type next entry-op gt entry-val 75 poll-interval 5"
A. Upon the value reaching 75%, a SNMP event is generated and sent to the trap server.
B. It reads an SNMP variable, and when the value exceeds 75%, it triggers an action.
C. It issues email when the value is greater than 75% for five polling cycles.
D. It presents a SNMP variable that can be interrogated.
Question 337
What is a requirement for an Ansible-managed node?
A. It must have an SSH server running.
B. It must be a Linux server or a Cisco device.
C. It must support ad hoc commands.
D. It must have an Ansible Tower installed.
Question 338
Which characteristic distinguishes Ansible from Chef?
A. Ansible uses Ruby to manage configurations. Chef uses YAML to manage configurations.
B. The Ansible server can run on Linux, Unix or Windows. The Chef server must run on Linux or Unix.
C. Ansible pushes the configuration to the client. Chef client pulls the configuration from the server.
D. Ansible lacks redundancy support for the primary server. Chef runs two primary servers in active/active mode.
Question 339
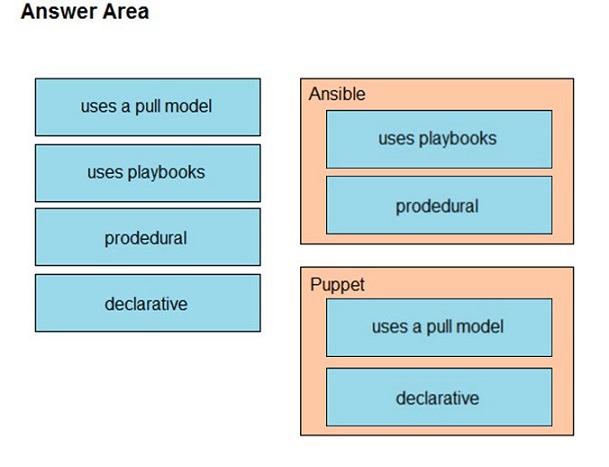
DRAG DROP -Drag and drop the characteristics from the left onto the orchestration tools that they describe on the right.
Select and Place:
Question 340
Refer to the exhibit. What does the snippet of code achieve?
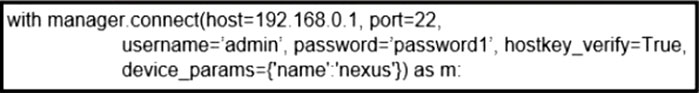
A. It creates an SSH connection using the SSH key that is stored, and the password is ignored.
B. It creates a temporary connection to a Cisco Nexus device and retrieves a token to be used for API calls.
C. It opens an ncclient connection to a Cisco Nexus device and maintains it for the duration of the context.
D. It opens a tunnel and encapsulates the login information, if the host key is correct.



