Question 411
Refer to the exhibit. An access list is required to permit traffic from any host on interface G0/0 and deny traffic from interface G/0/1. Which access list must be applied?
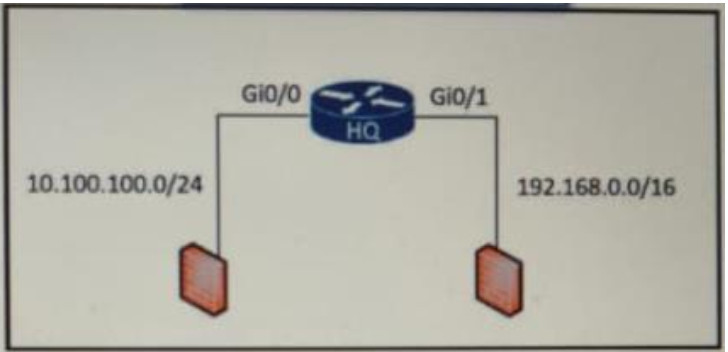
A. ip access-list standard 99 Permit 10.100.100.0 0.0.0.255 Deny 192.168.0.0 0.0.255.255
B. ip access-list standard 99 Permit 10.100.100.0 0.0.0.255 Deny 192.168.0.0 0.255.255.255
C. ip access-list standard 100 Permit 10.100.100.0 0.0.0.255 Deny 192.168.0.0 0.255.255.255
D. ip access-list standard 100 Permit 10.100.100.0 0.0.0.255 Deny 192.168.0.0 0.0.255.255
Question 412
Which device tracks the state of active connections in order to make a decision to forward a packet through?
A. wireless access point
B. firewall
C. wireless LAN controller
D. router
Question 413
How do servers connect to the network in a virtual environment?
A. wireless to an access point that is physically connected to the network
B. a cable connected to a physical switch on the network
C. a virtual switch that links to an access point that is physically connected to the network
D. a software switch on a hypervisor that is physically connected to the network
Question 414
What is recommended for the wireless infrastructure design of an organization?
A. group access points together to increase throughput on a given channel
B. configure the first three access points are configured to use Channels 1, 6, and 11
C. include a least two access points on nonoverlapping channels to support load balancing
D. assign physically adjacent access points to the same Wi-Fi channel
Question 415
Which network plane is centralized and manages routing decisions?
A. policy plane
B. management plane
C. control plane
D. data plane
Question 416
How does a switch process a frame received on Fa0/1 with the destination MAC address of 0e38.7363.657b when the table is missing the address?
A. lt drops the frame immediately.
B. It forwards the frame back out of interface Fa0/1.
C. It floods the frame to all interfaces except Fa0/1.
D. It holds the frame until the MAC address timer expires and then drops the frame.
Question 417
Refer to the exhibit. An access list is created to deny Telnet access from host PC-1 to RTR-1 and allow access from all other hosts. A Telnet attempt from PC-2 gives this message: "% Connection refused by remote host." Without allowing Telnet access from PC-1, which action must be taken to permit the traffic?
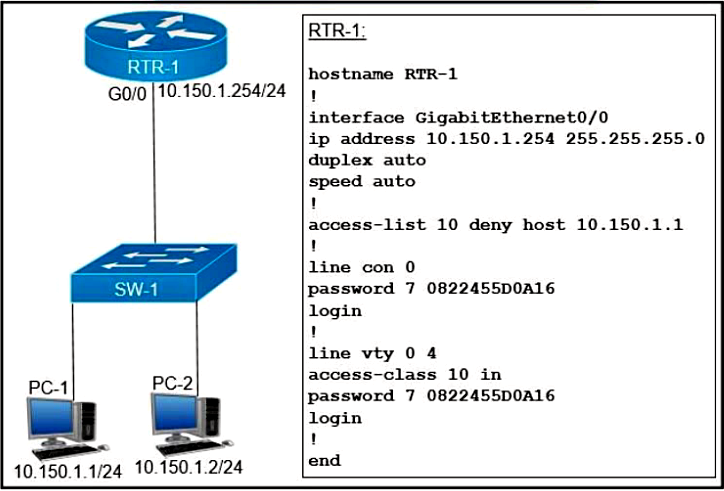
A. Add the access-list 10 permit any command to the configuration.
B. Remove the access-class 10 in command from line vty 0 4
C. Add the ip access-group 10 out command to interface g0/0.
D. Remove the password command from line vty 0 4.
Question 418
Which protocol does an IPv4 host use to obtain a dynamically assigned IP address?
A. ARP
B. DHCP
C. CDP
D. DNS
Question 419
What is a benefit of VRRP?
A. It provides traffic load balancing to destinations that are more than two hops from the source.
B. It provides the default gateway redundancy on a LAN using two or more routers.
C. It allows neighbors to share routing table information between each other.
D. It prevents loops in a Layer 2 LAN by forwarding all traffic to a root bridge, which then makes the final forwarding decision.
Question 420
Which type of security program is violated when a group of employees enters a building using the ID badge of only one person?
A. intrusion detection
B. user awareness
C. physical access control
D. network authorization

