Question 391
A port security violation has occurred on a switch port due to the maximum MAC address count being exceeded Which command must be configured to increment the security-violation count and forward an SNMP trap?
A. switchport port-security violation access
B. switchport port-security violation protect
C. switchport port-security violation restrict
D. switchport port-security violation shutdown
Question 392
Refer to the exhibit. Which type of configuration is represented in the output?
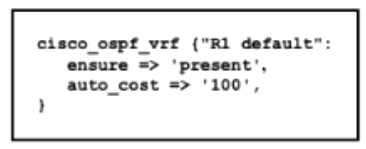
A. Ansible
B. JSON
C. Chef
D. Puppet
Question 393
Refer to the exhibit. An engineer configured the New York router with static routes that point to the Atlanta and Washington sites. Which command must be configured on the Atlanta and Washington routers so that both sites are able to reach the loopback2 interface on the New York router?
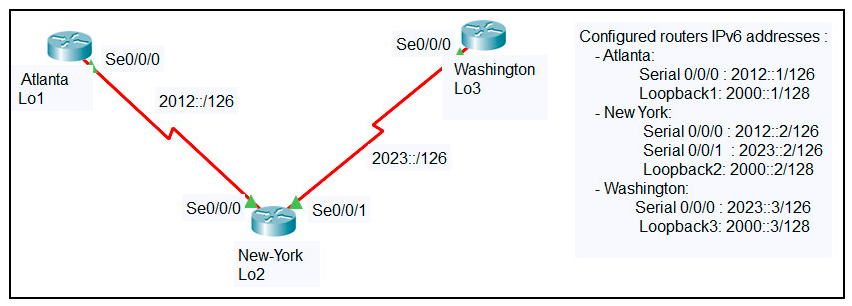
A. ipv6 route::/0 Serial 0/0/0
B. ipv6 route::/0 Serial 0/0/1
C. ipv6 route:0/0 Serial 0/0/0
D. ip route 0.0.0.0 0.0.0.0 Serial 0/0/0
E. ipv6 route::/0 2000::2
Question 394
In software defined architectures, which plane is distributed and responsible for traffic forwarding?
A. management plane
B. control plane
C. policy plane
D. data plane
Question 395
An engineer requires a scratch interface to actively attempt to establish a trunk link with a neighbor switch. What command must be configured?
A. switchport mode trunk
B. switchport mode dynamic desirable
C. switchport mode dynamic auto
D. switchport nonegotiate
Question 396
What are two recommendations for protecting network ports from being exploited when located in an office space outside of an IT closet? (Choose two)
A. configure static ARP entries
B. enable the PortFast feature on ports
C. implement port-based authentication
D. configure ports to a fixed speed
E. shut down unused ports
Question 397
Refer to the exhibit. After the election process, what is the root bridge in the HQ LAN? -Switch1:0C:E0:38:81:32:58 -Switch2:0C:0E:15:22:1A:61 -Switch3:0C:0E:15:1D:3C:9A -Switch4:0C:E0:19:A1:4D:16
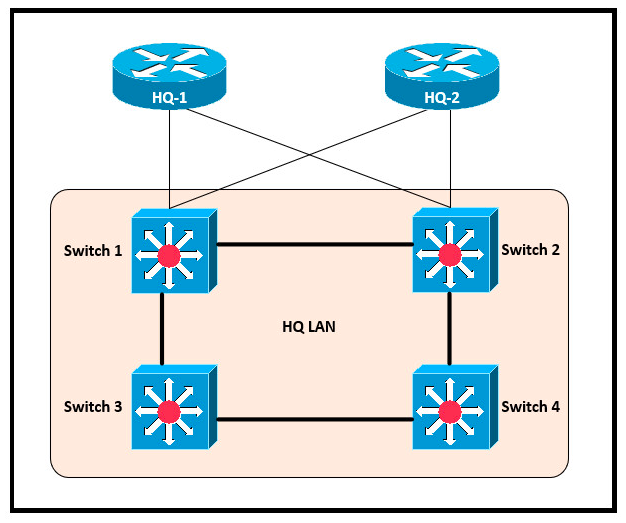
A. Switch 1
B. Switch 2
C. Switch 3
D. Switch 4
Question 398
What is a function of TFTP in network operations?
A. transfers a backup configuration file from a server to a switch using a username and password
B. transfers files between file systems on a router
C. transfers a configuration files from a server to a router on a congested link
D. transfers IOS images from a server to a router for firmware upgrades
Question 399
Which CRUD operation modifies an existing table or view?
A. read
B. create
C. replace
D. update
Question 400
What is a function of a remote access VPN?
A. used cryptographic tunneling to protect the privacy of data for multiple users simultaneously
B. used exclusively when a user is connected to a company's internal network
C. establishes a secure tunnel between two branch sites
D. allows the users to access company internal network resources through a secure tunnel


