Question 141
Which evasion technique is indicated when an intrusion detection system begins receiving an abnormally high volume of scanning from numerous sources?
A. resource exhaustion
B. tunneling
C. traffic fragmentation
D. timing attack
Question 142
DRAG DROP -Drag and drop the technology on the left onto the data type the technology provides on the right.
Select and Place:

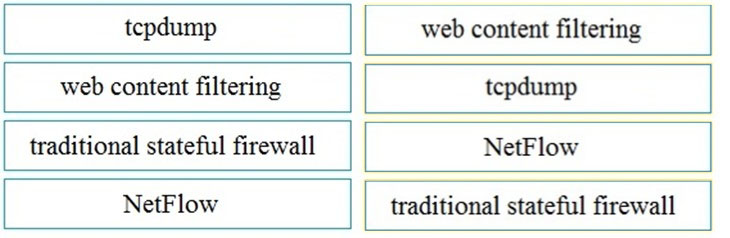
Question 143
Refer to the exhibit. Which application protocol is in this PCAP file?
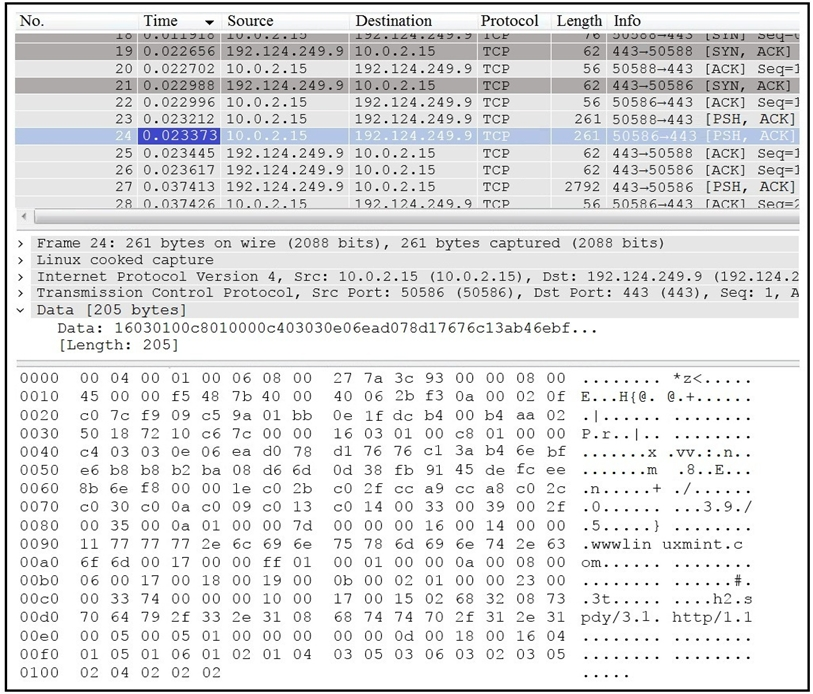
A. SSH
B. TCP
C. TLS
D. HTTP
Question 144
DRAG DROP -Refer to the exhibit. Drag and drop the element name from the left onto the appropriate piece of the PCAP file on the right.
Select and Place:


Question 145
Refer to the exhibit. What is the expected result when the "Allow subdissector to reassemble TCP streams" feature is enabled?

A. insert TCP subdissectors
B. extract a file from a packet capture
C. disable TCP streams
D. unfragment TCP
Question 146
Which type of data collection requires the largest amount of storage space?
A. alert data
B. transaction data
C. session data
D. full packet capture
Question 147
An analyst discovers that a legitimate security alert has been dismissed.
Which signature caused this impact on network traffic?
A. true negative
B. false negative
C. false positive
D. true positive
Question 148
Which signature impacts network traffic by causing legitimate traffic to be blocked?
A. false negative
B. true positive
C. true negative
D. false positive
Question 149
Which two pieces of information are collected from the IPv4 protocol header? (Choose two.)
A. UDP port to which the traffic is destined
B. TCP port from which the traffic was sourced
C. source IP address of the packet
D. destination IP address of the packet
E. UDP port from which the traffic is sourced
Question 150
Which HTTP header field is used in forensics to identify the type of browser used?
A. referrer
B. host
C. user-agent
D. accept-language





