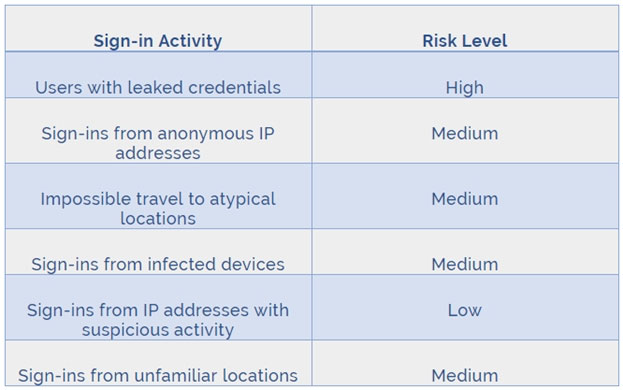
Azure AD Identity protection can detect six types of suspicious sign-in activities:
- Users with leaked credentials
- Sign-ins from anonymous IP addresses
- Impossible travel to atypical locations
Sign-ins from infected devices -
- Sign-ins from IP addresses with suspicious activity
- Sign-ins from unfamiliar locations
These six types of events are categorized in to 3 levels of risks - High, Medium & Low:
References:
http://www.rebeladmin.com/2018/09/step-step-guide-configure-risk-based-azure-conditional-access-policies/

