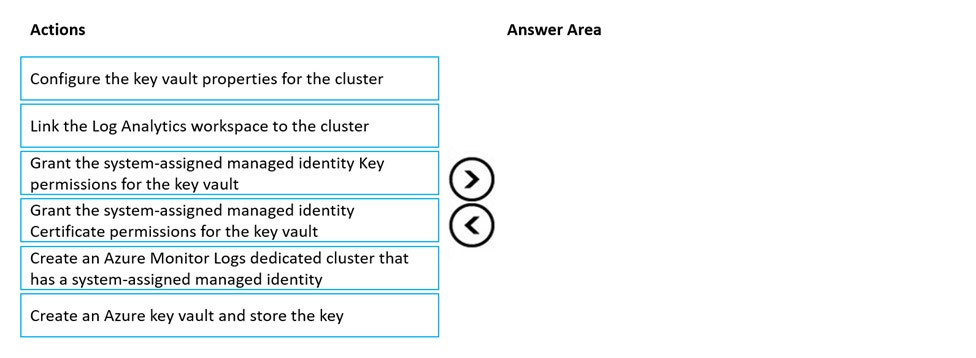
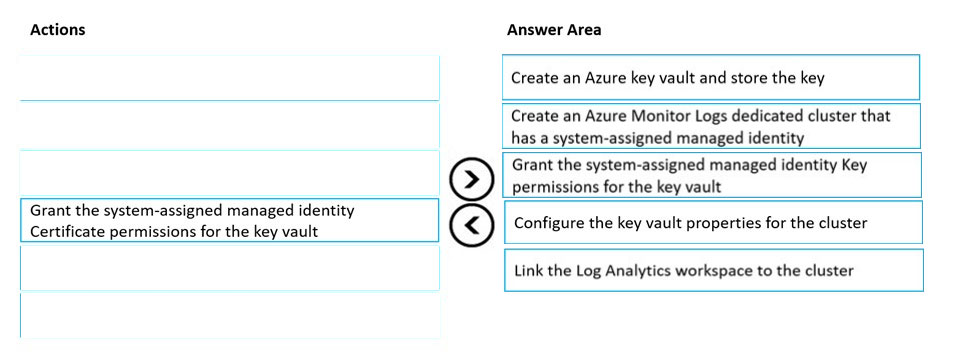
Customer-Managed key provisioning steps:
Step 1: Create an Azure Key vault and store the key.
Creating Azure Key Vault and storing key. Create or use an existing Azure Key Vault in the region that the cluster is planed, and generate or import a key to be used for logs encryption.
Step 2: Create an Azure Monitor Logs dedicate cluster that has a system-assigned managed identity
Clusters uses managed identity for data encryption with your Key Vault. Configure identity type property to SystemAssigned when creating your cluster to allow access to your Key Vault for "wrap" and "unwrap" operations.
Step 3: Grant the system-assigned managed Identity Key permissions for the key vault.
Grant Key Vault permissions.
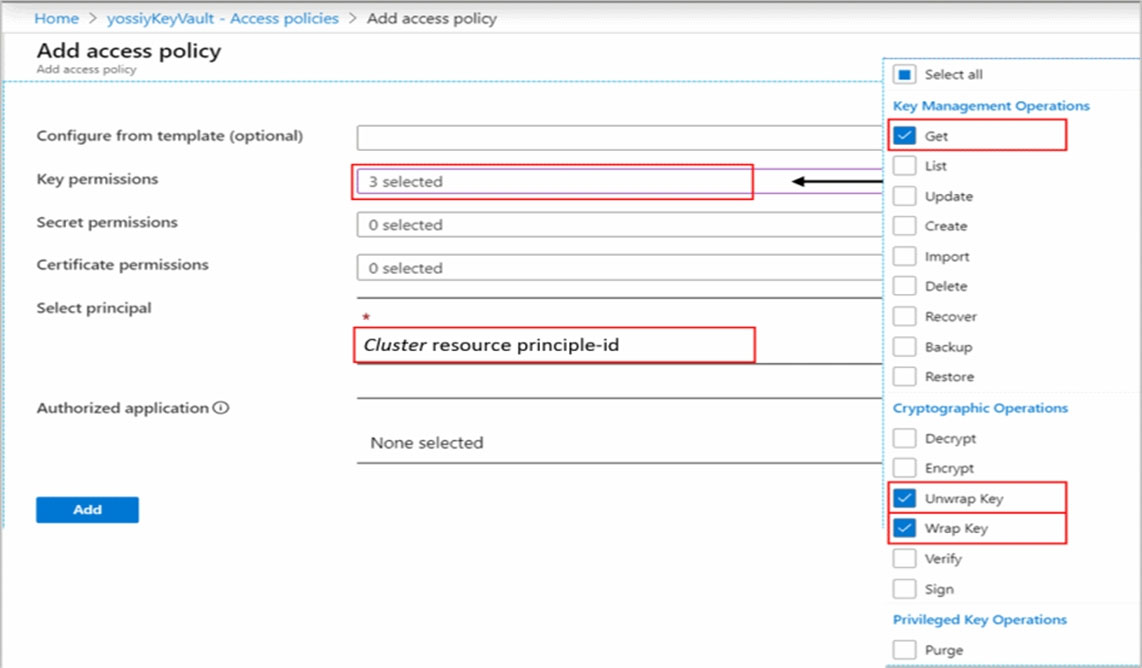
Create Access Policy in Key Vault to grants permissions to your cluster. These permissions are used by the underlay cluster storage. Open your Key Vault in
Azure portal and click Access Policies then + Add Access Policy to create a policy with these settings:
Key permissions-select Get, Wrap Key and Unwrap Key.
Etc.
1. Creating cluster
2. Granting permissions to your Key Vault
3. Updating cluster with key identifier details
4. Linking workspaces
Step 4: Configure the key vault properties for the cluster.
Update cluster with key identifier details.
Step 5: Link the Log Analytics workspace to the cluster
Link workspace to cluster.
This step should be performed only after the cluster provisioning. If you link workspaces and ingest data prior to the provisioning, ingested data will be dropped and won't be recoverable.
Reference:
https://docs.microsoft.com/en-us/azure/azure-monitor/logs/customer-managed-keys