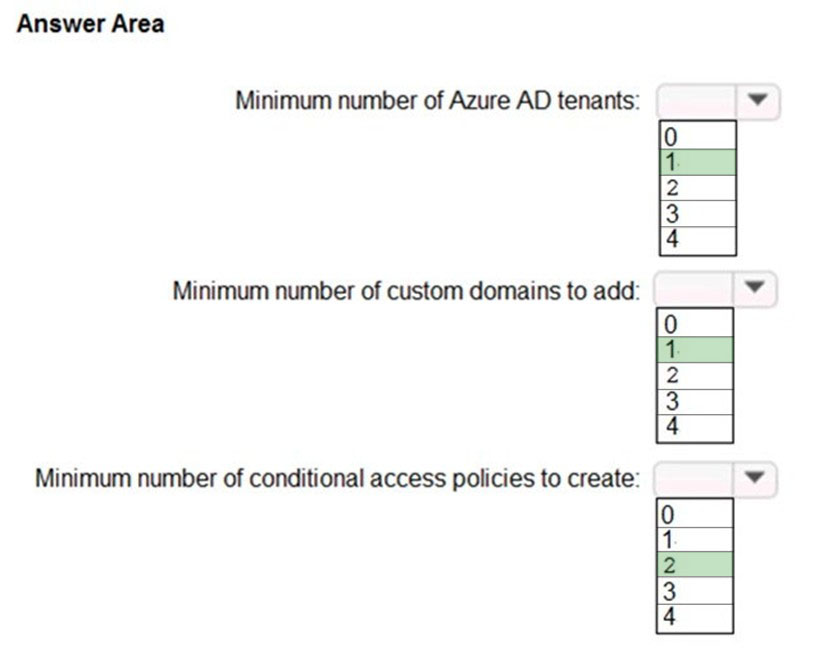
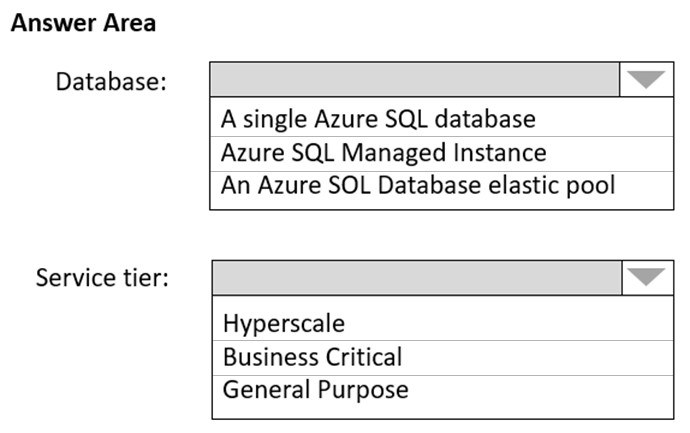
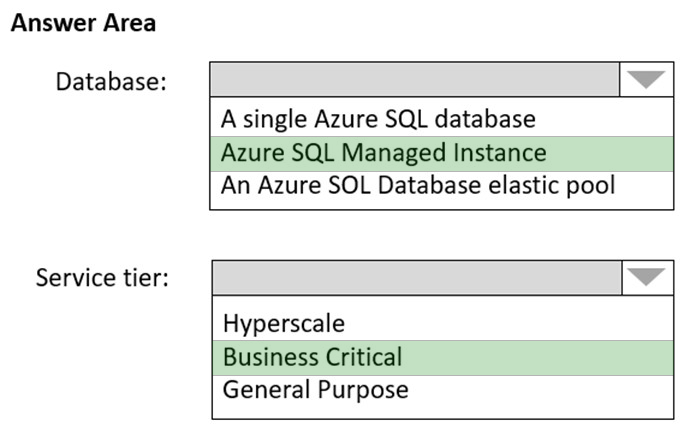
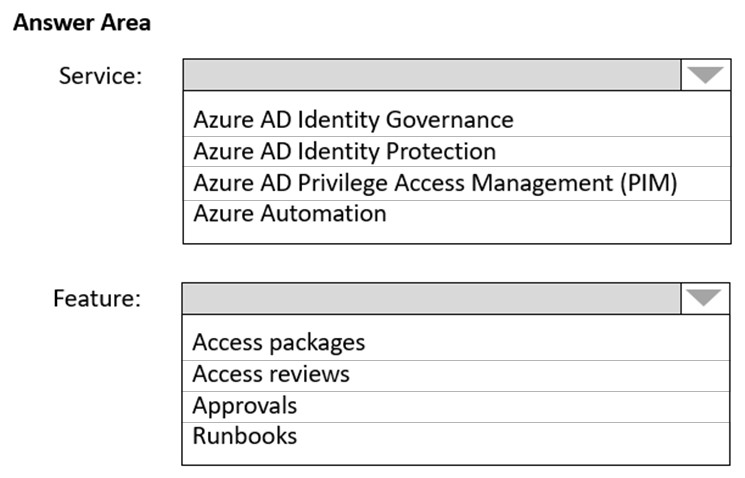
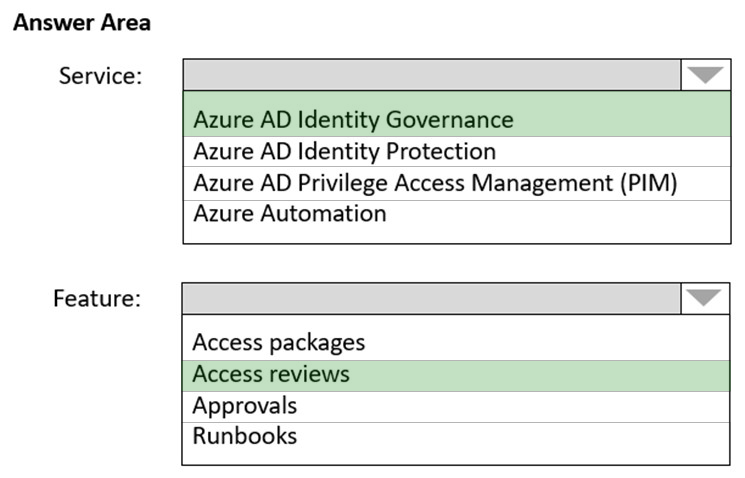
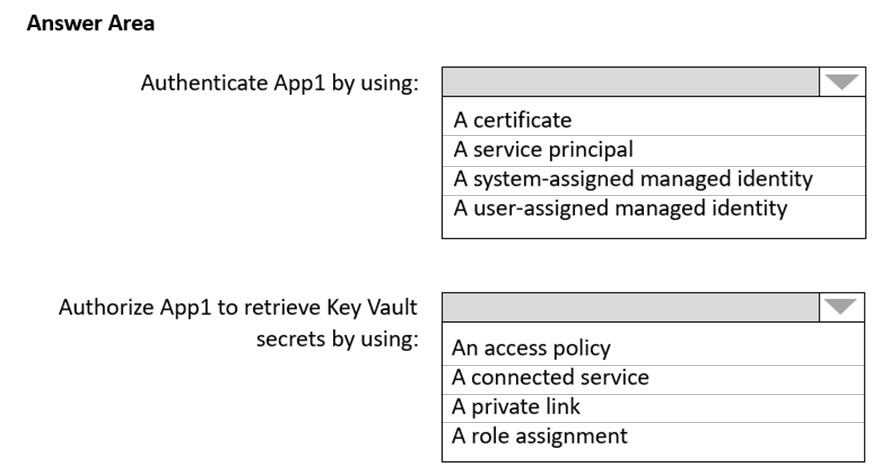
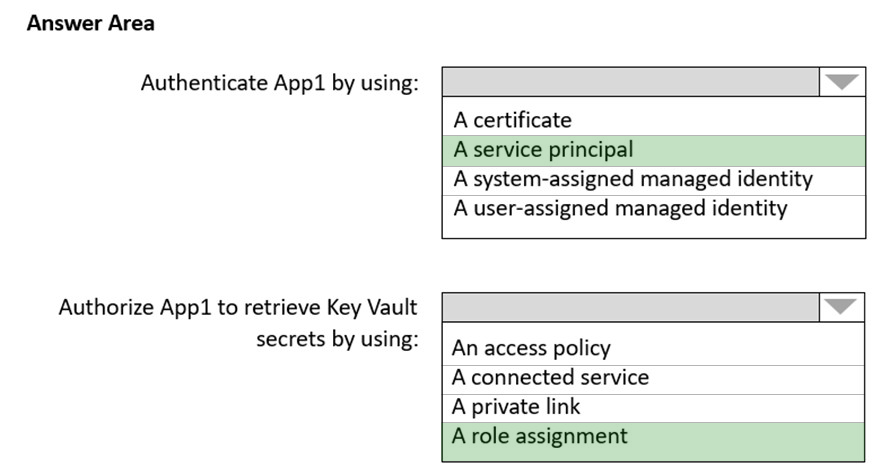
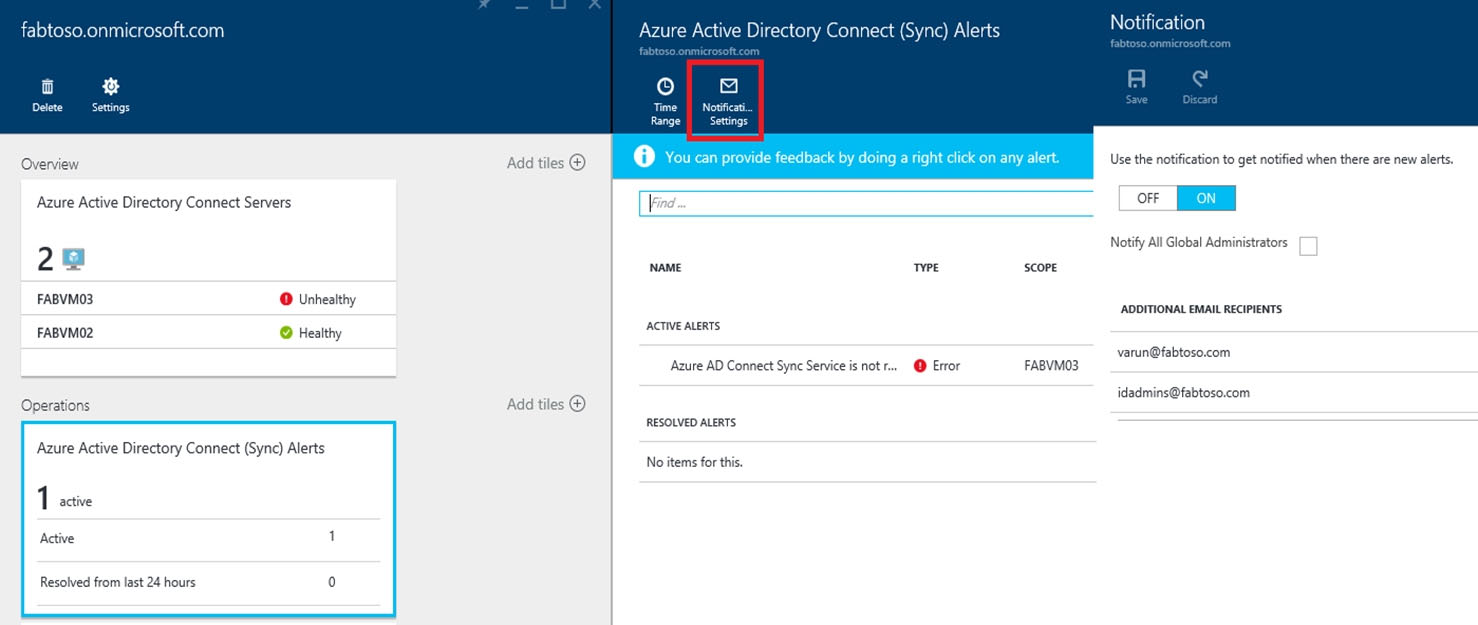
An email distribution group named IT Support must be notified of any issues relating to the directory synchronization services.
Note: You can configure the Azure AD Connect Health service to send email notifications when alerts indicate that your identity infrastructure is not healthy. his occurs when an alert is generated, and when it is resolved.
Reference:
https://docs.microsoft.com/en-us/azure/active-directory/hybrid/how-to-connect-health-operations