Question 21
An administrator wants to simplify remote access without asking users to provide user credentials.
Which access control method provides this solution?
A. ZTNA full mode
B. SSL VPN
C. L2TP
D. ZTNA IP/MAC filtering mode
Question 22
Which two statements are true about the ZTNA rule? (Choose two.)
A. It enforces access control.
B. It redirects the client request to the access proxy.
C. It applies security profiles to protect traffic.
D. It defines the access proxy.
Question 23
What is the function of the quick scan option on FortiClient?
A. It scans programs and drivers that are currently running, for threats.
B. It performs a full system scan including all files, executable files, DLLs, and drivers for threats.
C. It allows users to select a specific file folder on their local hard disk drive (HDD), to scan for threats.
D. It scans executable files, DLLs, and drivers that are currently running, for threats.
Question 24
Which two benefits are benefits of using multi-tenancy mode on FortiClient EMS? (Choose two.)
A. It provides granular access and segmentation.
B. The fabric connector must use an IP address to connect to FortiClient EMS.
C. Licenses are shared among sites.
D. Separate host servers manage each site.
Question 25
Refer to the exhibit.
Based on the settings shown in the exhibit, what action will FortiClient take when it detects that a user is trying to download an infected file?
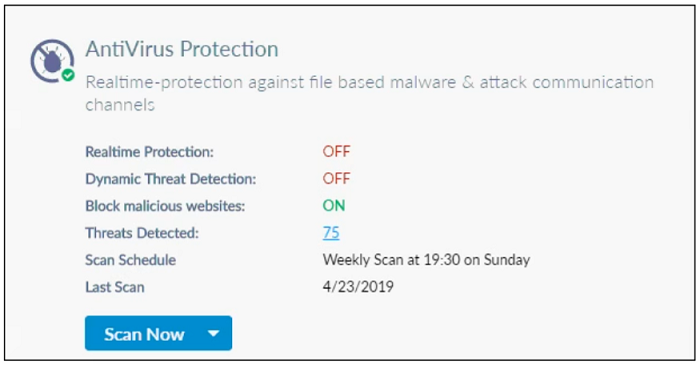
A. Blocks the infected files as it is downloading
B. Sends the infected file to FortiGuard for analysis
C. Quarantines the infected files and logs all access attempts
D. Allows the infected file to download without scan
Question 26
Refer to the exhibit.
Based on the Security Fabric automation settings, what action will be taken on compromised endpoints?
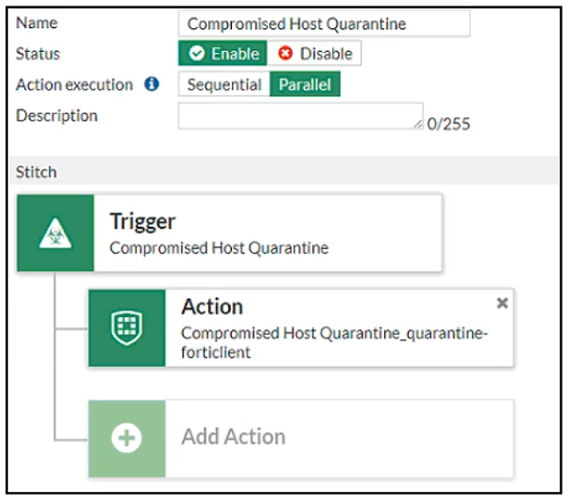
A. Endpoints will be banned on FortiGate.
B. Endpoints will be quarantined through a network device.
C. An email notification will be sent for compromised endpoints.
D. Endpoints will be quarantined through EMS.
Question 27
Refer to the exhibits, which show the Zero Trust Tag Monitor and the FortiClient GUI status.
Remote-Client is tagged as Remote-Users on the FortiClient EMS Zero Trust Tag Monitor.
What must an administrator do to show the tag on the FortiClient GUI?
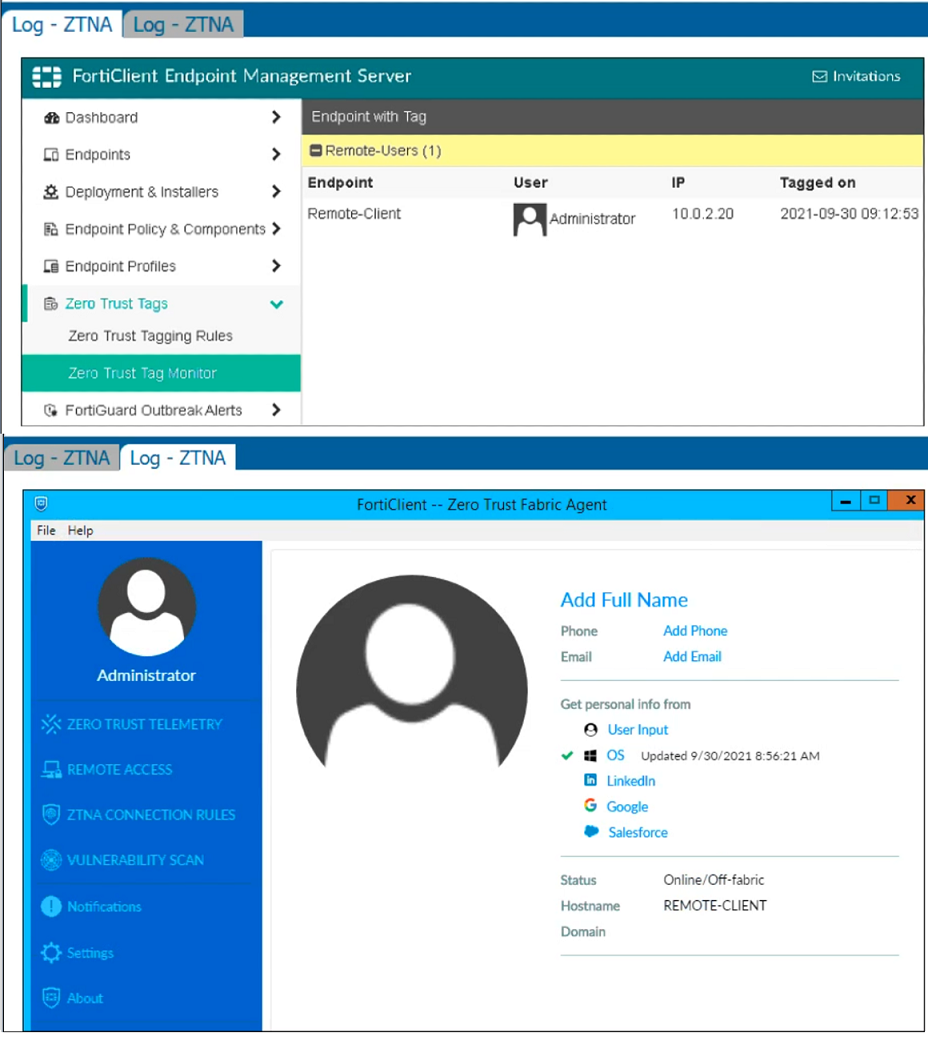
A. Change the FortiClient system settings to enable tag visibility.
B. Update tagging rule logic to enable tag visibility.
C. Change the user identity settings to enable tag visibility.
D. Change the endpoint control setting to enable tag visibility.
Question 28
An administrator configures ZTNA configuration on the FortiGate for remote users.
Which statement is true about the firewall policy?
A. It defines the access proxy.
B. It redirects the client request to the access proxy.
C. It applies security profiles to protect traffic.
D. It enforces access control.
Question 29
Why does FortiGate need the root CA certificate of FortiClient EMS?
A. To update FortiClient client certificates
B. To trust certificates issued by FortiClient EMS
C. To revoke FortiClient client certificates
D. To sign FortiClient CSR requests
Question 30
Which statement about the FortiClient enterprise management server is true?
A. It receives the configuration information of endpoints from FortiGate.
B. It provides centralized management of multiple endpoints running FortiClient software.
C. It receives the CA certificate from FortiGate to validate client certificates.
D. It enforces compliance on the endpoints using tags.


