Question 1
Which component or device shares device status information through ZTNA telemetry?
A. FortiClient
B. FortiGate
C. FortiGate Access Proxy
D. FortiClient EMS
Question 2
Which statement about FortiClient comprehensive endpoint protection is true?
A. It helps to safeguard systems from email spam.
B. It helps to safeguard systems from advanced security threats, such as malware.
C. It helps to safeguard systems from data loss.
D. It helps to safeguard systems from DDoS.
Question 3
Which two third-party tools can an administrator use to deploy FortiClient? (Choose two.)
A. Microsoft Active Directory GPO
B. Microsoft SCCM
C. QR code generator
D. Microsoft Windows Installer
Question 4
In a FortiSandbox integration, what does the remediation option do?
A. Deny access to a file when it sees no results
B. Wait for FortiSandbox results before allowing files
C. Alert and notify only
D. Exclude specified files
Question 5
An administrator is required to maintain a software vulnerability on the endpoints, without showing the feature on the FortiClient dashboard.
What must the administrator do to achieve this requirement?
A. Click the hide icon on the vulnerability scan tab
B. Use the default endpoint profile
C. Disable select the vulnerability scan feature in the deployment package
D. Select the vulnerability scan feature in the deployment package, but disable the feature on the endpoint profile
Question 6
An administrator deploys a FortiClient installation through the Microsoft AD group policy. After the installation is complete, all the custom configuration is missing.
What could have caused this problem?
A. The FortiClient MST file is missing from the distribution package.
B. The FortiClient package is not assigned to the group.
C. The FortiClient .exe file is included in the distribution package.
D. FortiClient does not have permission to access the distribution package.
Question 7
An administrator installs FortiClient on Windows Server.
What is the default behavior of real-time protection control?
A. Real-time protection must update AV signature database.
B. Real-time protection is disabled.
C. Real-time protection sends malicious files to FortiSandbox when the file is not detected locally.
D. Real-time protection must update the signature database from FortiSandbox.
Question 8
Refer to the exhibit, which shows the output of the ZTNA traffic log on FortiGate.
What can you conclude from the log message?

A. The remote user connection does not match the explicit proxy policy.
B. The remote user connection does not match the ZTNA server configuration.
C. The remote user connection does not match the ZTNA firewall policy.
D. The remote user connection does not match the ZTNA rule configuration.
Question 9
What action does FortiClient anti-exploit detection take when it detects exploits?
A. Deletes the compromised application process
B. Blocks memory allocation to the compromised application process
C. Terminates the compromised application process
D. Patches the compromised application process
Question 10
Refer to the exhibit.
Based on the settings shown in the exhibit, which action will FortiClient take when users try to access www facebook.com?
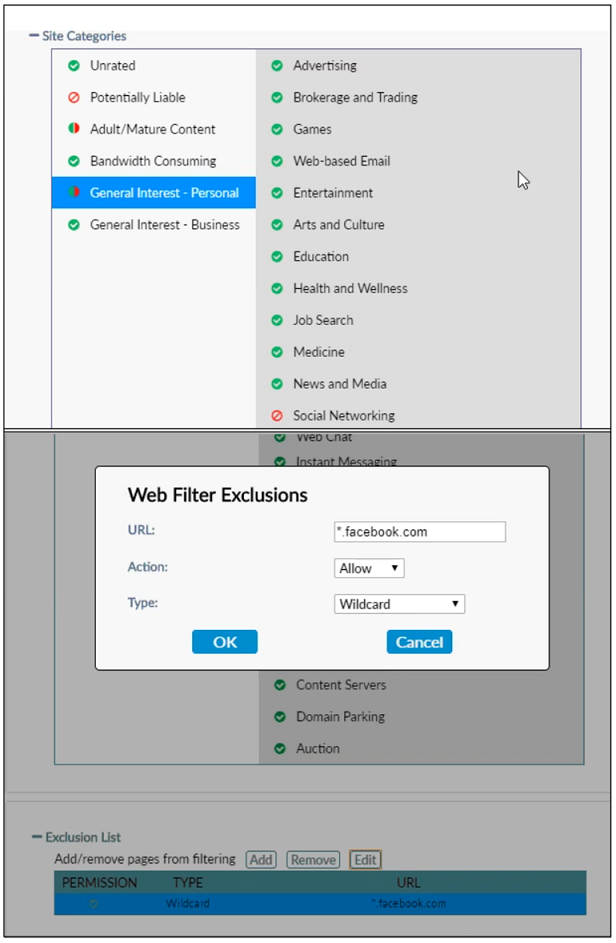
A. FortiClient will prompt a warning message to warn the user before they can access the Facebook website.
B. FortiClient will block access to Facebook and its subdomains.
C. FortiClient will monitor only the user’s web access to the Facebook website.
D. FortiClient will allow access to Facebook.

