Question 161
Which two aspects of the cloud PaaS model are managed by the customer but not the provider? (Choose two.)
A. middleware
B. applications
C. virtualization
D. operating systems
E. data
Question 162
Which public cloud provider supports the Cisco Next Generation Firewall Virtual?
A. Google Cloud Platform
B. Red Hat Enterprise Virtualization
C. Amazon Web Services
D. VMware ESXi
Question 163
What is an attribute of the DevSecOps process?
A. security scanning and theoretical vulnerabilities
B. development security
C. isolated security team
D. mandated security controls and check lists
Question 164
On which part of the IT environment does DevSecOps focus?
A. application development
B. wireless network
C. data center
D. perimeter network
Question 165
In a PaaS model, which layer is the tenant responsible for maintaining and patching?
A. hypervisor
B. virtual machine
C. network
D. application
Question 166
Which two deployment model configurations are supported for Cisco FTDv in AWS? (Choose two.)
A. Cisco FTDv configured in routed mode and managed by an FMCv installed in AWS
B. Cisco FTDv with one management interface and two traffic interfaces configured
C. Cisco FTDv configured in routed mode and managed by a physical FMC appliance on premises
D. Cisco FTDv with two management interfaces and one traffic interface configured
E. Cisco FTDv configured in routed mode and IPv6 configured
Question 167
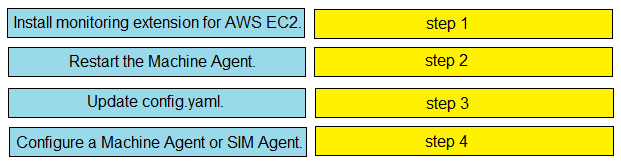
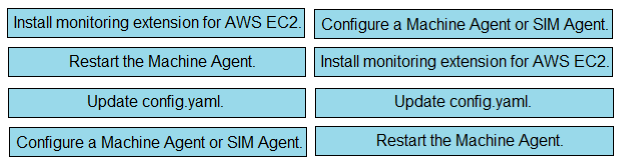
DRAG DROP -Drag and drop the steps from the left into the correct order on the right to enable Cisco AppDynamics to monitor an EC2 instance in AWS.Select and Place:
Question 168
What is a required prerequisite to enable malware file scanning for the Secure Internet Gateway?
A. Enable IP Layer enforcement.
B. Activate the Cisco AMP license.
C. Activate SSL decryption.
D. Enable Intelligent Proxy.
Question 169
A company is experiencing exfiltration of credit card numbers that are not being stored on-premise. The company needs to be able to protect sensitive data throughout the full environment. Which tool should be used to accomplish this goal?
A. Cisco ISE
B. Web Security Appliance
C. Security Manager
D. Cloudlock
Question 170
What are the two types of managed Intercloud Fabric deployment models? (Choose two.)
A. Service Provider managed
B. User managed
C. Public managed
D. Hybrid managed
E. Enterprise managed

