Question 931
hostname CPE
service password-encryption
ip domain name ccna.cisco.com
ip name-server 198.51.100.210
crypto key generate rsa modulus 1024
username admin privilege 15 secret s0m3s3cr3t
line vty 0 4
transport input ssh
login local
Refer to the exhibit. An engineer executed the script and added commands that were not necessary for SSH and now must remove the commands. Which two commands must be executed to correct the configuration? (Choose two.)
A. no ip name-serveer 198.51.100.210
B. no login local
C. no service password-encryption
D. no ip domain mame ccna.cisco.com
E. no hostname CPE
Question 932
Which two actions are taken as the result of traffic policing? (Choose two.)
A. bursting
B. dropping
C. remarking
D. fragmentation
E. buffering
Question 933
Which two server types support domain name to IP address resolution? (Choose two.)
A. authoritative
B. web
C. file transfer
D. resolver
E. ESX host
Question 934
What is a purpose of traffic shaping?
A. It enables policy-based routing.
B. It enables dynamic flow identification.
C. It provides best-effort service.
D. It limits bandwidth usage.
Question 935
An engineering team asks an implementer to configure syslog for warning conditions and error conditions.
Which command does the implementer configure to achieve the desired result?
A. logging trap 5
B. logging trap 2
C. logging trap 3
D. logging trap 4
Question 936
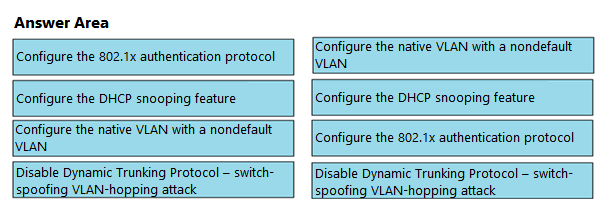
DRAG DROP -Drag and drop the attack-mitigation techniques from the left onto the types of attack that they mitigate on the right.
Question 937
Which WLC management connection type is vulnerable to man-in-the-middle attacks?
A. console
B. Telnet
C. SSH
D. HTTPS
Question 938
Which type of encryption does WPA1 use for data protection?
A. PEAP
B. TKIP
C. AES
D. EAP
Question 939
Refer to the exhibit. A network administrator must permit traffic from the 10.10.0.0/24 subnet to the WAN on interface Serial0. What is the effect of the configuration as the administrator applies the command?
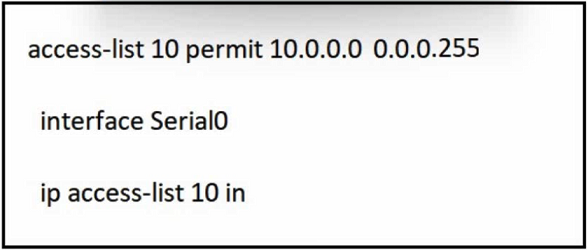
A. The router accepts all incoming traffic to Serial0 with the last octet of the source IP set to 0.
B. The permit command fails and returns an error code.
C. The router fails to apply the access list to the interface.
D. The sourced traffic from IP range 10.0.0.0 - 10.0.0.255 is allowed on Serial0.
Question 940
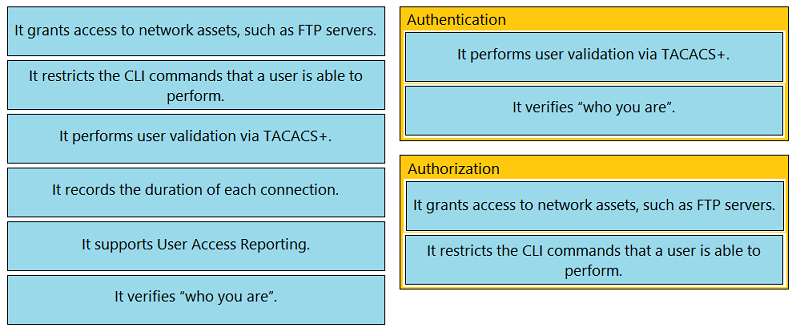
DRAG DROP -Drag and drop the statements about AAA services from the left to the corresponding AAA services on the right. Not all options are used.