Question 651
An engineer is installing a new wireless printer with a static IP address on the Wi-Fi network. Which feature must be enabled and configured to prevent connection issues with the printer?
A. client exclusion
B. DHCP address assignment
C. passive client
D. static IP tunneling
Question 652
Refer to the exhibit. The ntp server 192.168.0.3 command has been configured on router 1 to make it an NTP client of router 2. Which command must be configured on router 2 so that it operates in server-only mode and relies only on its internal clock?
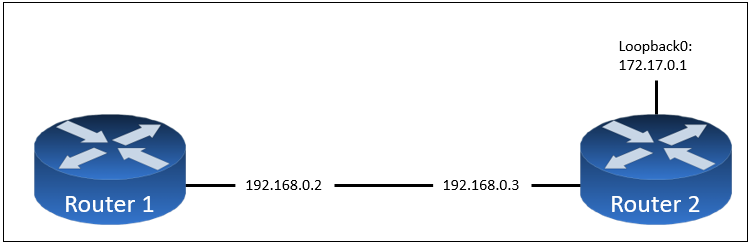
A. Router2(config)#ntp server 172.17.0.1
B. Router2(config)#ntp server 192.168.0.2
C. Router2(config)#ntp passive
D. Router2(config)#ntp master 4
Question 653
An engineer is configuring switch SW1 to act as an NTP server when all upstream NTP server connectivity fails. Which configuration must be used?
A. SW1# config t SW1(config)#ntp peer 192.168.1.1 SW1(config)#ntp access-group peer accesslist1
B. SW1# config t SW1(config)#ntp master SW1(config)#ntp server192.168.1.1
C. SW1# config t SW1(config)#ntp backup SW1(config)#ntp server192.168.1.1
D. SW1# config t SW1(config)#ntp server192.168.1.1 SW1(config)#ntp access-group peer accesslist1
Question 654
Which two statements about NTP operations are true? (Choose two.)
A. NTP uses UDP over IP.
B. Cisco routers can act as both NTP authoritative servers and NTP clients.
C. Cisco routers can act only as NTP servers.
D. Cisco routers can act only as NTP clients.
E. NTP uses TCP over IP.
Question 655
Refer to the exhibit. Which configuration must be applied to the router that configures PAT to translate all addresses in VLAN 200 while allowing devices on VLAN100 to use their own IP addresses?
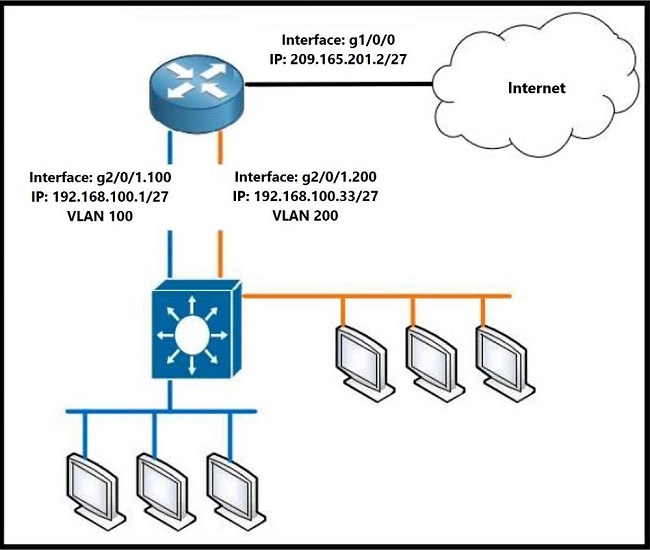
A. Router1(config)#access-list 99 permit 192.168.100.32 0.0.0.31 Router1(config)#ip nat inside source list 99 interface gi1/0/0 overload Router1(config)#interface gi2/0/1.200 Router1(config)#ip nat inside Router1(config)#interface gi1/0/0 Router1(config)#ip nat outside
B. Router1(config)#access-list 99 permit 192.168.100.0 0.0.0.255 Router1(config)#ip nat inside source list 99 interface gi1/0/0 overload Router1(config)#interface gi2/0/1.200 Router1(config)#ip nat inside Router1(config)#interface gi1/0/0 Router1(config)#ip nat outside
C. Router1(config)#access-list 99 permit 209.165.201.2 255.255.255.255 Router1(config)#ip nat inside source list 99 interface gi1/0/0 overload Router1(config)#interface gi2/0/1.200 Router1(config)#ip nat inside Router1(config)#interface gi1/0/0 Router1(config)#ip nat outside
D. Router1(config)#access- list 99 permit 209.165.201.2 0.0.0.0 Router1(config)#ip nat inside source list 99 interface gi1/0/0 overload Router1(config)#interface gi2/0/1.200 Router1(config)#ip nat inside Router1(config)#interface gi1/0/0 Router1(config)#ip nat outside
Question 656
Refer to the exhibit. Which two commands must be added to update the configuration of router R1 so that it accepts only encrypted connections? (Choose two.)
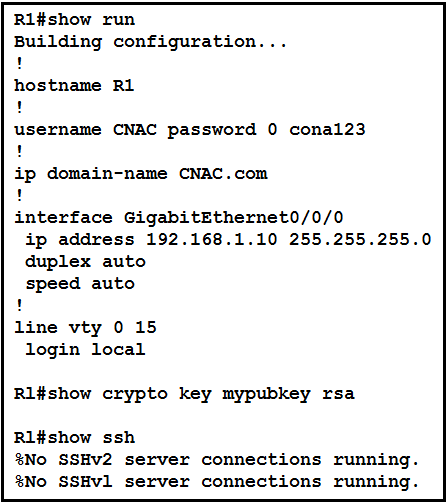
A. transport input ssh
B. username CNAC secret R!41!3705926@
C. crypto key generate rsa 1024
D. line vty 0 4
E. ip ssh version 2
Question 657
Which command implies the use of SNMPv3?
A. snmp-server user
B. snmp-server host
C. snmp-server enable traps
D. snmp-server community
Question 658
R1 as an NTP server must have:
- NTP authentication enabled
- NTP packets sourced from Interface loopback 0
- NTP stratum 2
- NTP packets only permitted to client IP 209.165.200.225
How should R1 be configured?
A. ntp authenticate ntp authentication-key 2 sha1 CISCO123 ntp source Loopback0 ntp access-group server-only 10 ntp master 2 ! access-list 10 permit udp host 209.165.200.225 any eq 123
B. ntp authenticate ntp authentication-key 2 md5 CISCO123 ntp interface Loopback0 ntp access-group server-only 10 ntp stratum 2 ! access-list 10 permit 209.165.200.225
C. ntp authenticate ntp authentication-key 2 md5 CISCO123 ntp source Loopback0 ntp access-group server-only 10 ntp master 2 ! access-list 10 permit 209.165.200.225
D. ntp authenticate ntp authentication-key 2 md5 CISCO123 ntp source Loopback0 ntp access-group server-only 10 ntp stratum 2 ! access-list 10 permit udp host 209.165.200.225 any eq 123
Question 659
A network engineer is configuring a switch so that it is remotely reachable via SSH. The engineer has already configured the host name on the router. Which additional command must the engineer configure before entering the command to generate the RSA key?
A. password password
B. ip ssh authentication-retries 2
C. ip domain-name domain
D. crypto key generate rsa modulus 1024
Question 660
Which QoS traffic handling technique retains excess packets in a queue and reschedules these packets for later transmission when the configured maximum bandwidth has been surpassed?
A. traffic policing
B. weighted random early detection
C. traffic prioritization
D. traffic shaping


